APT-Hunter is Threat Hunting tool for windows event logs which made by purple team mindset to provide detect APT movements hidden in the sea of windows event logs to decrease the time to uncover suspicious activity without the need to have complicated solution for parsing and detecting attacks in windows event logs like SIEM solutions and log collectors . If you are a Threat Hunter , Incident Responder or forensic investigator , i assure you will enjoy using this tool , why ? i will discuss the reason in this article and how it will make your life easy just it made mine . Kindly note this tool is heavily tested but still a beta version and may contain bugs .
APT-Hunter can be downloaded from here : APT-Hunter
Why I Built this Tool ?
Many analysts ignore windows event logs or does not know where to search for suspicious activity and most of them does know what event logs to collect in case of attack .i work as Security specialist in SOC environment and we provide threat hunting , incident response and forensic investigation to our customers . Usually the customer does not have SIEM or log collector solution which make it really hard to collect the windows event logs , upload them to ( SIEM solution , parse the data , start searching to uncover any indication of compromise using searches which you have to memorize them in order to not miss anything ) if you have license but if you don’t then you are on your own to enjoy extracting CSV from evtx files and start looking for events in the sheet with millions of events . also if you search the web there is not much open source tools to analyze windows event logs and many analyst gets lazy and only depend on other forensic sources to uncover system compromise . Now if you are using APT-Hunter you will have :
- uncover any suspicious activity you don’t know about before it turns to a big incident .
- Detect APT movements in the system based on events from previous discovered APT attacks.
- Make a good use of the windows event logs you collected .
- faster attack detection which will decrease the response time in order to quickly contain and eradicate the attacks.
- Output configured to be compatible with timesketch so you can do time line analysis .
- With the important 60 use cases configured in one place you will invest your time in other data sources .
- Faster investigating multiple servers in short amount of time .
- it will help you in cases you don’t have much time to do deep investigation .
- Free Open source tool that will serve you without any limitation .
- Personally i used it in many incident and helped me uncover events i missed out and allowed me finish the investigations faster .
- Turn millions of events into hundreds with severity you can use as a filter.
How APT-Hunter work ?
APT-Hunter have two parts that work together to help the user get the data he want quickly . This tool will be used to speed up windows log analysis but will never replace the deep log analysis .
- Collecting logs : user can collect the logs in both CSV and EVTX format manually or use the powershell scripts discussed latter in this article to automatically extract the required logs .
- Analyzing CSV logs : APT-hunter use builtin library ( csv ) in order to parse the CSV log files then using Regex the fields extracted for every events used in APT-Hunter. users can use the extracted fields to create their use cases .
- Analyzing EVTX logs : APT-hunter use external library ( evtx ) in order to parse the EVTX log files then using Regex the fields extracted for every events used in APT-Hunter. users can use the extracted fields to create their use cases .
- Logs Analyzed : ( Sysmon , Security , System , Powershell , Powershell_Operational , ScheduledTask , WinRM , TerminalServices , Windows_Defender )
APT-Hunter Features
- Provide output with timesketch format to upload it directly and start analyzing the time line .
- Events Categorized based Severity to make the filtering easy and focus on what important.
- Have A log collection automation script to collect all the required logs to save the time required to export important logs .
- Gather and analyze ( Sysmon , Security , System , Powershell , Powershell_Operational , ScheduledTask , WinRM , TerminalServices , Windows_Defender ) .
- This rule tested in many real incidents and provided a great information that reduced the time to detect initial evidence .
- Can run on any system thanks to python3 . you can do live analysis on the affected system or take the logs offline and analyze them on any system .
- Log Parsing and extraction using Regex .
- This tool built based on researches published on the internet and testing done by me in order to collect most of the useful use cases in one tool .
- Includes more than 60 Use cases along with Security and terminal services logs statistics and more will be added soon . Say good bye to memorizing use cases and SIEM searches .
- Now you don’t need to setup instance of SIEM , Log collector solutions to help you parse and extract the required data nor you have to keep looking at sheet with million of events.
- Log statistics that will help you uncover the anomaly .
- Easy to add new detection rule as the fields clear and syntax easy to use .
- Support windows event logs exported as EVTX and CSV .
- Analyst can add new malicious executable names directly to list .
- Provide output as excel sheet with every Log as work sheet .
- This release is just the beginning and more uses cases to come .
How to Use APT-Hunter
The first thing to do is to collect the logs if you didn’t and with powershell log collectors its easy to collect the needed logs automatically you just run the powershell scripts as administrator .
To collect the logs in EVTX format use : windows-log-collector-full-v3-EVTX.ps1 To collect the logs in CSV format use : windows-log-collector-full-v3-CSV.ps1
APT-Hunter built using python3 so in order to use the tool you need to install the required libraries .
python3 -m pip install -r Requirements.txt
APT-Hunter is easy to use you just use the argument -h to print help to see the options needed .
# python3 APT-Hunter.py -h
usage: APT-Hunter.py [-h] [-p PATH] [-o OUT] [-t {csv,evtx}]
[--security SECURITY] [--system SYSTEM]
[--scheduledtask SCHEDULEDTASK] [--defender DEFENDER]
[--powershell POWERSHELL] [--powershellop POWERSHELLOP]
[--terminal TERMINAL] [--winrm WINRM] [--sysmon SYSMON]
optional arguments:
-h, --help show this help message and exit
-p PATH, --path PATH path to folder containing windows event logs generated by the APT-Hunter-Log-Collector.ps1
-o OUT, --out OUT output file name
-t {csv,evtx}, --type {csv,evtx}
csv ( logs from get-eventlog or windows event log GUI
or logs from Get-WinEvent ) , evtx ( EVTX extension
windows event log )
--security SECURITY Path to Security Logs
--system SYSTEM Path to System Logs
--scheduledtask SCHEDULEDTASK
Path to Scheduled Tasks Logs
--defender DEFENDER Path to Defender Logs
--powershell POWERSHELL
Path to Powershell Logs
--powershellop POWERSHELLOP
Path to Powershell Operational Logs
--terminal TERMINAL Path to TerminalServices LocalSessionManager Logs
--winrm WINRM Path to Winrm Logs
--sysmon SYSMON Path to Sysmon Logs
-p : provide path to directory containing the extracted using the powershell log collectors ( windows-log-collector-full-v3-CSV.ps1 , windows-log-collector-full-v3-EVTX.ps1 ) .
-o : name of the project which will be used in the generated output sheets
-t : the log type if its CSV or EVTX
The remaining arguments if you want to analyze single type of logs.
Exmaples :
#python3 APT-Hunter.py -t evtx -p /opt/wineventlogs/ -o Project1 #python3 APT-Hunter.py -t csv -p /opt/wineventlogs/ -o Project1 #python3 APT-Hunter.py -t evtx --security evtx/security.evtx -o Project2
The result will be available in two sheets :
Project1_Report.xlsx : this excel sheet will include all the events detected from every windows logs provided to APT-Hunter
Project1_TimeSketch.csv : This CSV file you can upload it to timesketch in order to have timeline analysis that will help you see the full picture of the attack .
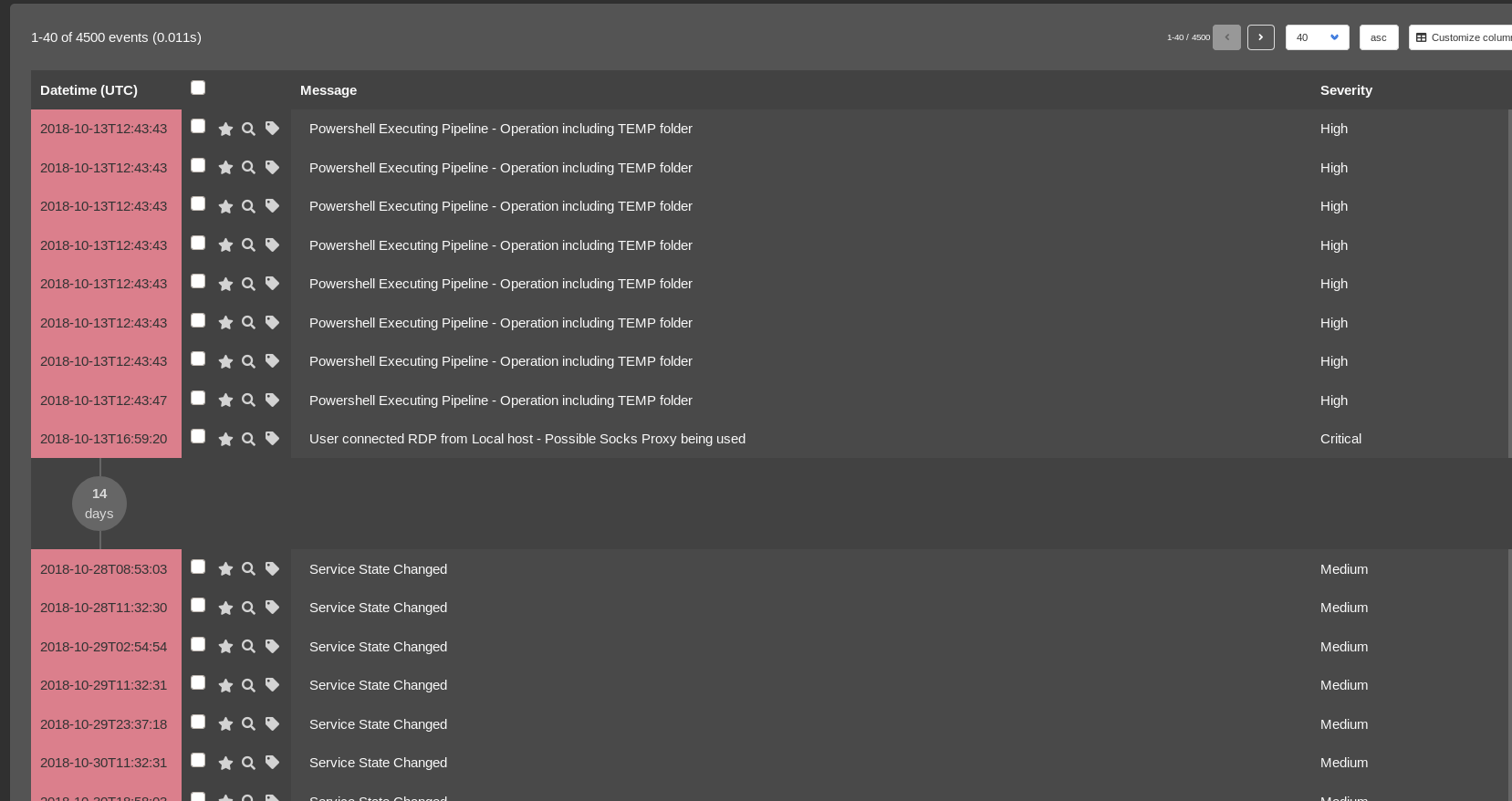
Below screenshot from uploading TimeSketch CSV file to timesketch instance :
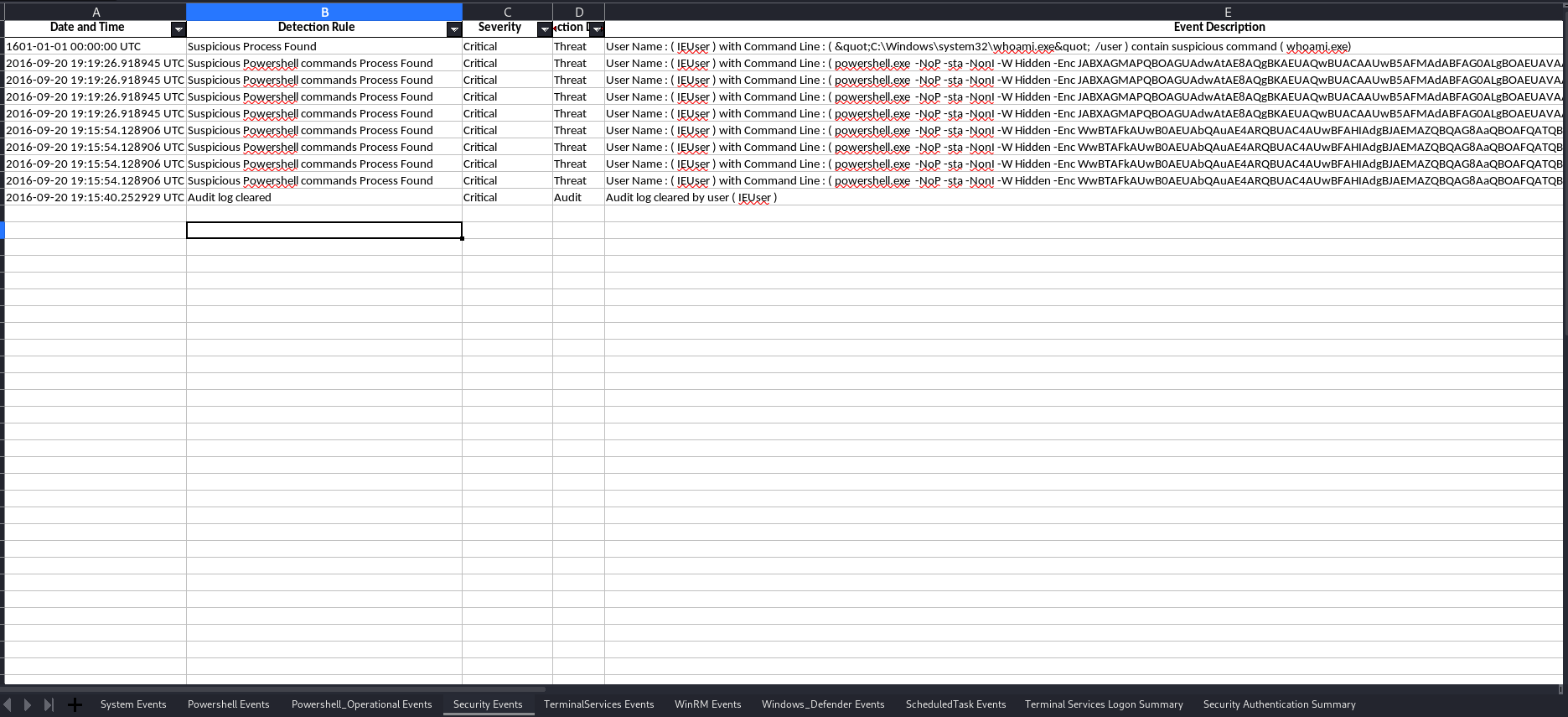
Below Screenshots shows the output in the excel sheet :
1. Findings in each log source .
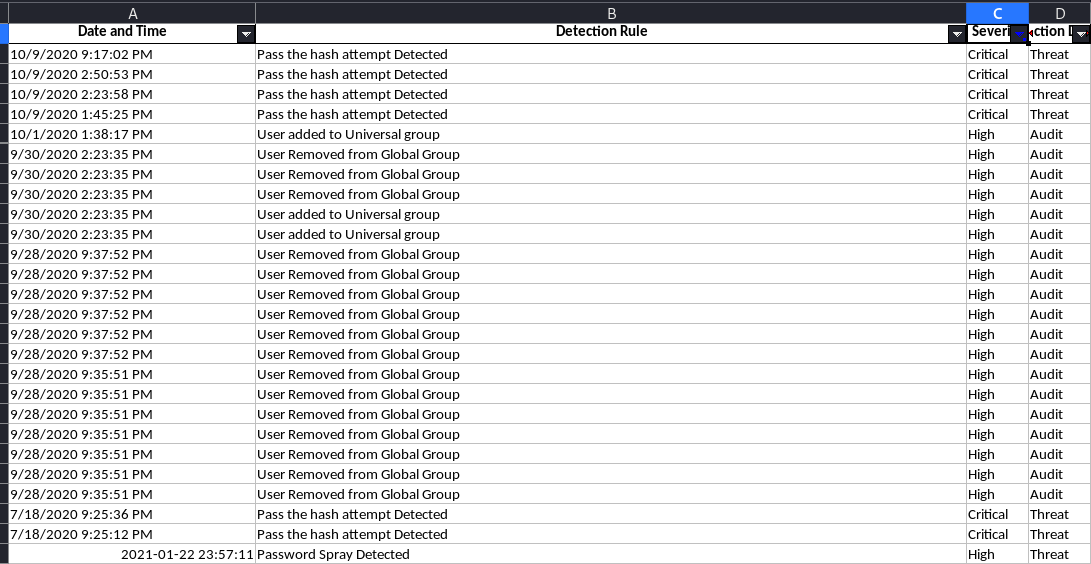
2. Statistics for Terminal Services in order to have over view of users accessing server GUI terminal interactively or using RDP .
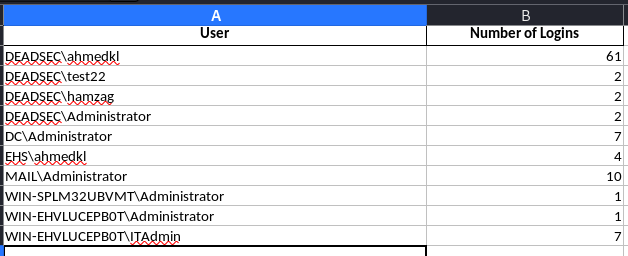
3. Statistics for successful/failed authentication in order to have summary for the authentication which may help you detect an anomaly or user who should not be logged on to the device .
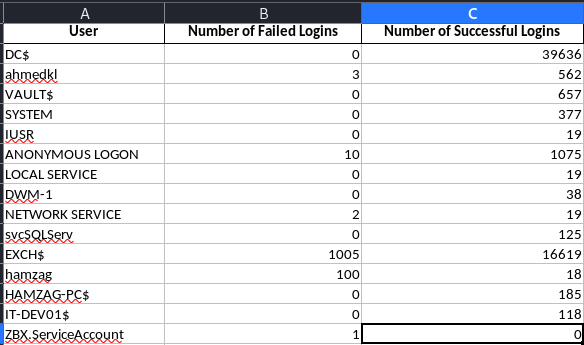
Events Detected by APT-Hunter
- [ T1086 ] Detecting Powershell with Suspicious Argument using sysmon logs
- [ T1543 ] Detecting Sc.exe manipulating windows services
- [ T1059 ] Detecting wscript or cscript runing script
- [ T1218.005 ] Detecting Mshta found running in the system
- [T1053] Detecting Scheduled Task manipulation
- [T1047] Command run remotely Using WMI
- [T1082] System Information Discovery
- [T1117] Bypassing Application Whitelisting with Regsvr32
- Prohibited Process connecting to internet
- Detecting Psexec running in the system
- Detecting Prohibited Process connecting to internet
- Detect Exchange Web service exploitation , such as ( CVE-2020-0688 )
- Detecting password spray attack using security logs
- Detecting Pass the hash attack using security logs
- Detecting Suspicious Attempt to enumerate users or groups using security logs
- Detecting Powershell Operation including TEMP Folder using Powershell operational logs
- Detecting Suspicious powershell commands using multiple event IDs using Powershell operational logs
- Detecting Suspicious powershell commands using multiple event IDs using Powershell logs
- Detecting connecting RDP from socks proxy using terminal services logs
- Detecting connecting RDP from public IP using terminal services logs
- Detecting connection is initiated using WinRM from machine Powershell remoting
- Detecting connection is initiated using WinRM to machine Powershell remoting
- Detecting User Creation using Net command using security logs
- Detecting Process running in suspicious location using security logs
- Detecting privilege Escalation using Token Elevation using security logs
- Detecting suspicious executable running using security logs
- Detecting suspicious powershell commands using security logs
- Detecting User Created through management interface using security logs
- Detecting Windows shutting down Events using security logs
- Detecting User added to local group using security logs
- Detecting User added user to global group using security logs
- Detecting User added user to universal group using security logs
- Detecting User removed from global group using security logs
- Detecting User removed from universal group using security logs
- Detecting User removed from local group using security logs
- Detecting User removed from global group using security logs
- Detecting User account removed using security logs
- Detecting Audit log cleared .
- Detecting System audit policy changes using security logs
- Detecting scheduled tasks creation using security logs
- Detecting scheduled task deletion using security logs
- Detecting scheduled task updates using security logs
- Detecting schedule task enabled using security logs
- Detecting schedule task disabled using security logs
- Detecting Windows Defender took action against Malware using windows defender logs
- Detecting Windows Defender failed to take action against Malware using windows defender logs
- Detecting Windows Defender Found Malware using windows defender logs
- Detecting Windows Defender deleted history of malwares using windows defender logs
- Detecting Windows Defender detected suspicious behavior Malware using windows defender logs
- Detecting Windows Defender real-time protection disabled using windows defender logs
- Detecting Windows Defender real-time protection configuration changed using windows defender logs
- Detecting Windows Defender scanning for malware is disabled using windows defender logs
- Detecting schedule task registered using scheduled tasks log
- Detecting schedule task updated using scheduled tasks log
- Detecting schedule task deleted using scheduled tasks log
- Detecting System Logs cleared using system logs
- Detecting Service Installed with executable in TEMP Folder using system logs
- Detecting Service installed in the system using system logs
- Detecting Service start type changed using system logs
- Detecting service state changed using system logs
What to expect in the future
- Adding more windows event logs support
- Add support for exchange logs to detect more exchange attacks
- Add support for IIS logs to detect more web app attacks
- Add more statistics to help discover the anomaly
- Threat Intelligence integration
- More use cases for sysmon .
13 Replies to “Introducing APT-Hunter : Threat Hunting Tool via Windows Event Log”