Estimated Reading Time: 9 minutesWhen you’re running any sort of offensive operations, managing your C2 traffic and hiding it with modern technologies is always an important thing to do, it’s not just a “nice-to-have”; it’s something you want to take care of while putting together your attack infrastructure. While reading through some of the latest AI buzz, I came…
Tag: redirectors
Oh my API, abusing TYK cloud API management to hide your malicious C2 traffic
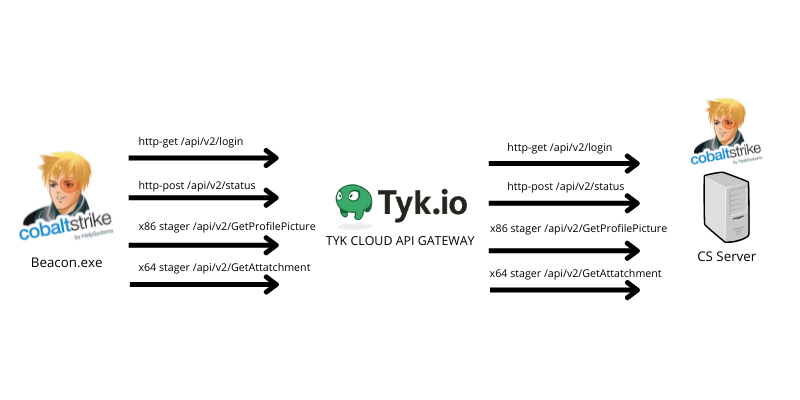
Estimated Reading Time: 10 minutesHiding your malicious C2 traffic through legitimate channels is challenging nowadays, especially while CDN providers block all known techniques to use domain fronting to hide your malicious traffic. For that reason, I was looking for a service that I can (ab)use to forward and hide my malicious C2 traffic using their domains without exposing my…
Automate Octopus C2 RedTeam Infrastructure Deployment
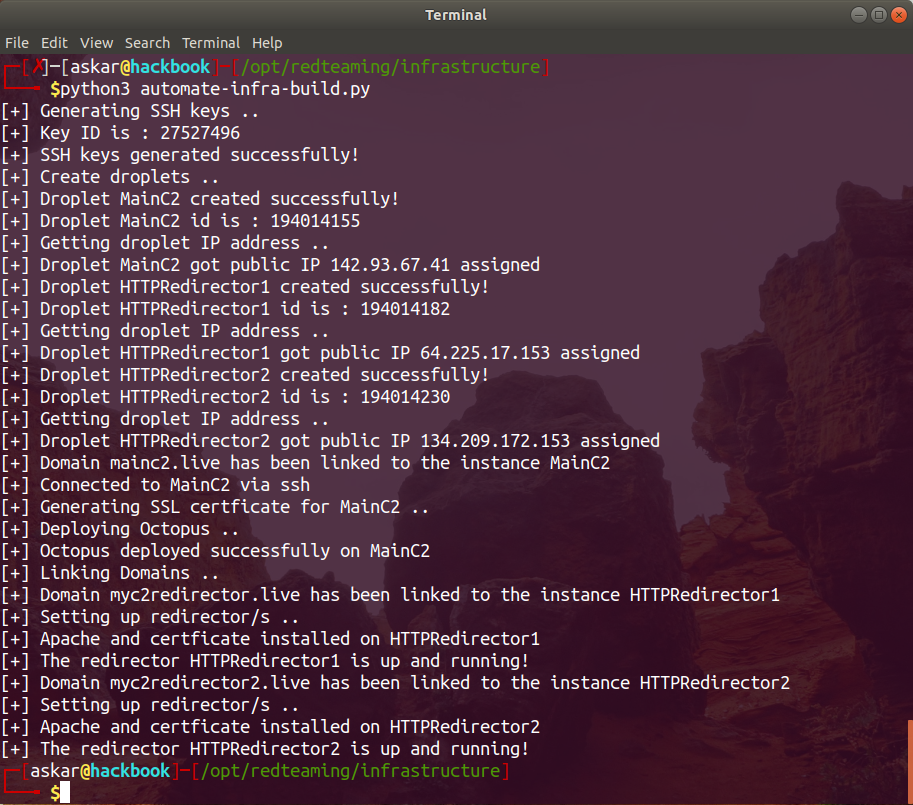
Estimated Reading Time: 15 minutesEstablishing a red team infrastructure for your operation is something you need to take care of every time, and you need to make sure it’s working without any obstacles before you begin your operation. Every time I start a new operation, I set up the infrastructure manually using DigitalOcean or AWS, and it’s always enjoyable…