After months of releasing the first version of Octopus, I’m more than glad to announce that the stable version of Octopus is out!
During the past few months, I worked with talented people to enhance Octopus capabilities and adding great features to it, also we fixed a couple of errors and made the usage of Octopus more stable for red teamers.
Our main goal of maintaining Octopus is to bring a nice and clean C2 for red teamers that could be deployed and used without thinking too much about how to prevent AVs/EDRs from detecting it and without putting your real infrastructure in danger, and I think we are doing good so far with that.
We added the following features to Octopus:
- Deploy cobalt strike beacon directly from Octopus
- DigiSpark payload generation
- Custom oneliner for windows 7
- Results logging
- Auto kill via profile
- New AMSI bypass
Also, we fixed some performance and usability issues to avoid any problems while using Octopus in real operations.
For now, Octopus is a terminal-based tool but in the near future, we are planning to add a web GUI for Octopus and add the ability to have multiple users working together.
Before we start with the new features, Take a look at this article to know more about Octopus and to see how you can use it.
Fixed Bugs
We fixed the following bugs in this release:
- Python2.7 failure while executing Octopus.
- Encryption error handling.
- Handling some EOF issues.
- Invalid listener handling.
I also fixed some issues related to listener creation and deletion to be more stable.
Deploy cobalt strike beacon directly from Octopus
As we always say that Octopus is only a pre-operation C2 and not a full C2 like (Empire, Cobalt Strike, Covenant, etc ..) so we are aiming to focus more on the first hit (Initial compromise/foothold) and because of that, we are integrating some C2s with Octopus to make them ready to deploy with one click after getting a clean foothold on the target’s infrastructure.
You can now deploy your own Powershell Cobalt Strike beacon directly from Octopus using the command:
deploy_cobalt_beacon beacon_pathOctopus will disable AMSI in the current Powershell process then loads Cobalt Strike beacon and runs it directly, This video shows how to perform that:
DigiSpark payload generation
You can now generate a DigiSpark payload that will run the Powershell agent once you plugged the Digispark to any PC.
You can use the following command to generate the payload:
generate_digispark listener_name payload_path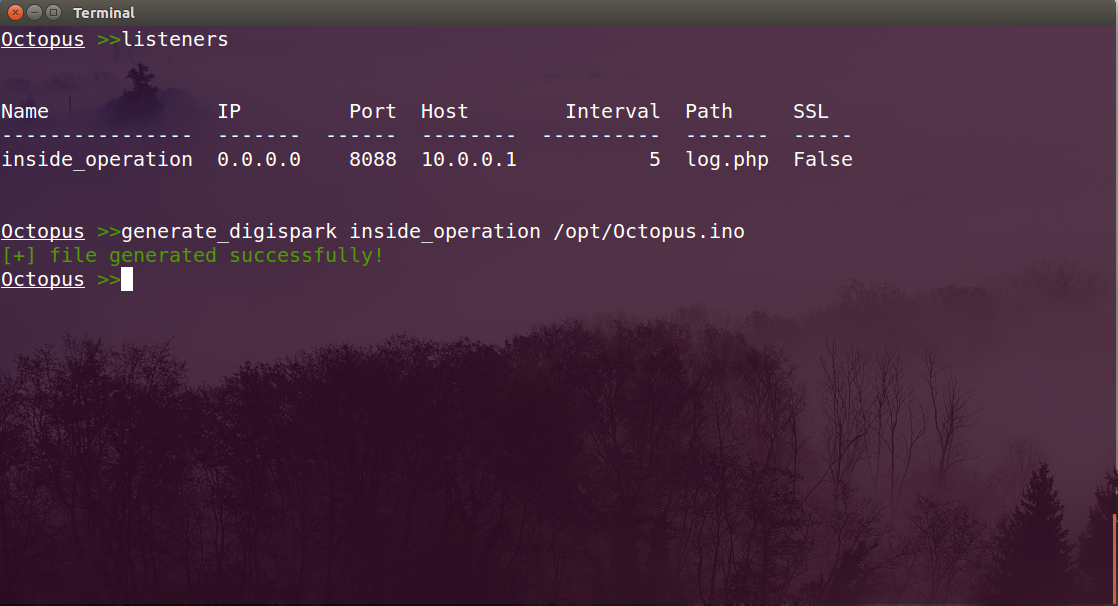
Agent auto-kill
The auto-kill feature in Octopus gives you the ability to control how many failed retries that Octopus needs to perform with the C2 before it kills the process.
For example, your C2 has been blocked by the firewall or got down for any reason, Octopus will try to connect to the server as usual and if there was an error while connecting and the server is not responding, Octopus will kill the process after a pre-defined number of failed tries that you can set in your profile.py file using auto_kill variable like the following:
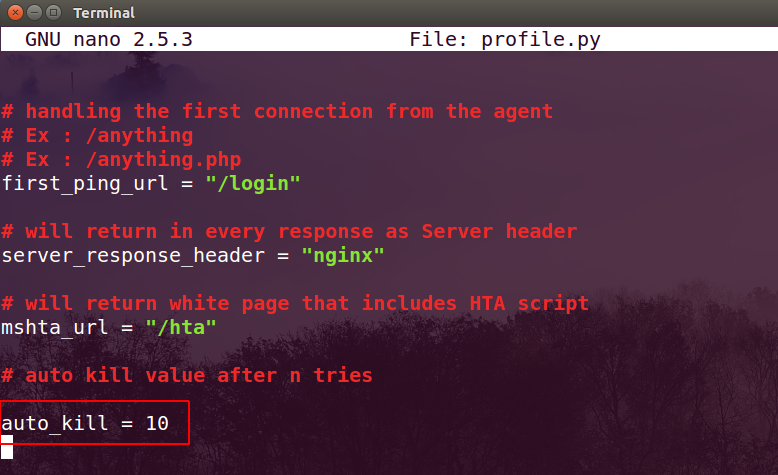
As we can see the auto_kill value here is 10 tries, which means Octopus will just count to hit 10 failed requests with the C2 and then it will kill the process and will no more exist in the system.
Results logging
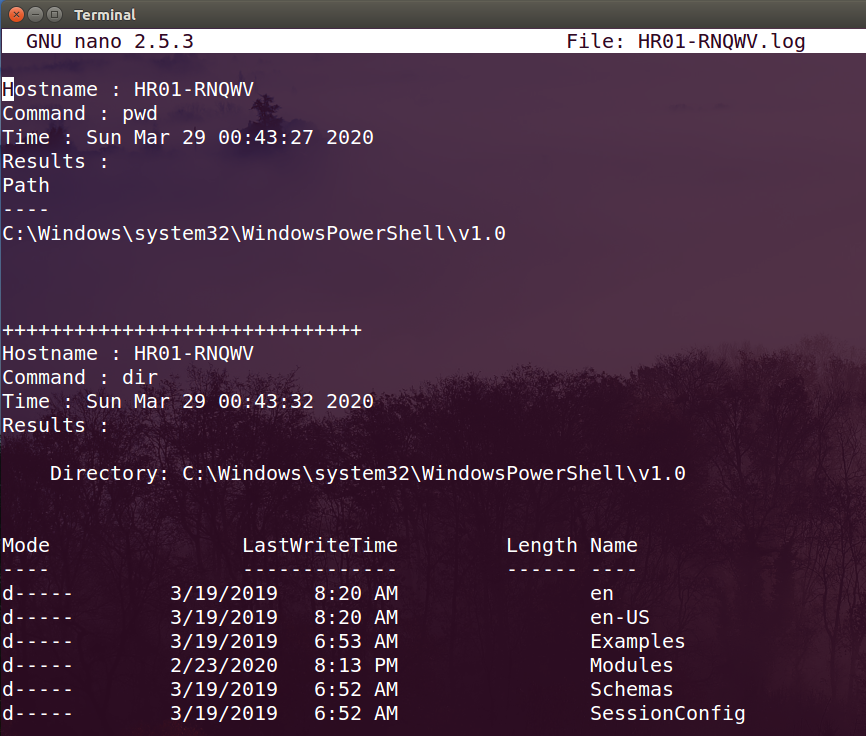
Octopus now can log and save every command that you execute on any machine, Octopus will create a file under “logs” directory inside Octopus main directory and save the log file by the target’s hostname.
It will save the following inside the log file:
- The target’s hostname.
- The executed command.
- When the command executed.
- Results of execution.
And the following is an example of the log file for the host “HR01-RNQWV”:
Upcoming features
Well, I guess we have a lot of features to be added soon to Octopus such as:
- Standalone C# agent.
- Screenshot module.
- Persistence module.
- Random variable generator for the agent.
- And much much more to come!
Final words
Octopus is still under development and always will be! my main goal is to maintain a useful tool for red teamers that can be used to have a quick and clean foothold on the target’s infrastructure.
So if you have the same interest in developing such as a tool, you can start enhancing and developing Octopus by opening issues and creating PR via the main Github Repo for Octopus.
Credits
I really want to thank the following fellows who made great contributions to Octopus:
- Ian Lyte for reporting multiple bugs in Octopus and pushing an enhanced AMSI bypass module.
- Moath Maharmah for enhancing the encryption module and writing a standalone C# Octopus agent which will be added to the upcoming release.
- Khlief for adding the HTA module and fix a bug in download.
- TeslaPulse for testing Octopus.
- J005 for adding enhanced Powershell oneliner and fix an issue in the HID attack script.
4 Replies to “Octopus v1.0 stable: Cobalt Strike deployment & much more!”