Since last release i was working on new features and to increase the processing speed for large number of windows event logs files so i rebuilt the tool to use multiprocessing and added more feature that will help you in your next investigation.
Download from here : https://github.com/ahmedkhlief/APT-Hunter/releases/tag/V3.0
APT-HUNTER V3.0 Features
- New use cases based on new attacks and incidents.
- More statistics and detection for new log sources (Group Policy , SMB Client , SMB Server)
- Rebuilt with Multiprocessing to utilize available resources.
- Specify start and end date to focus on specific time period.
- lightning-fast Regex Hunt that go through tons of logs in minutes .
- New Object Access Report.
- New Process Execution Report.
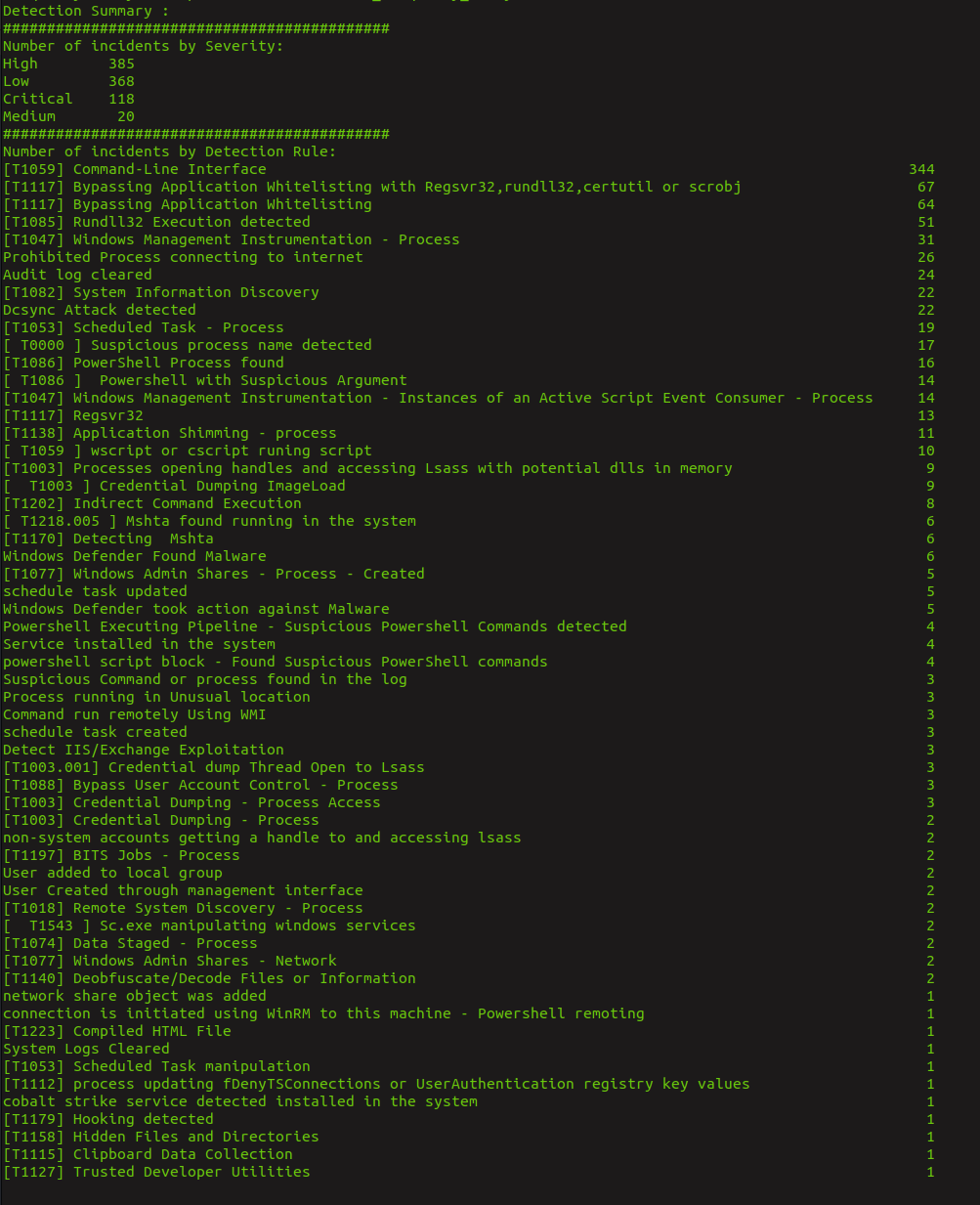
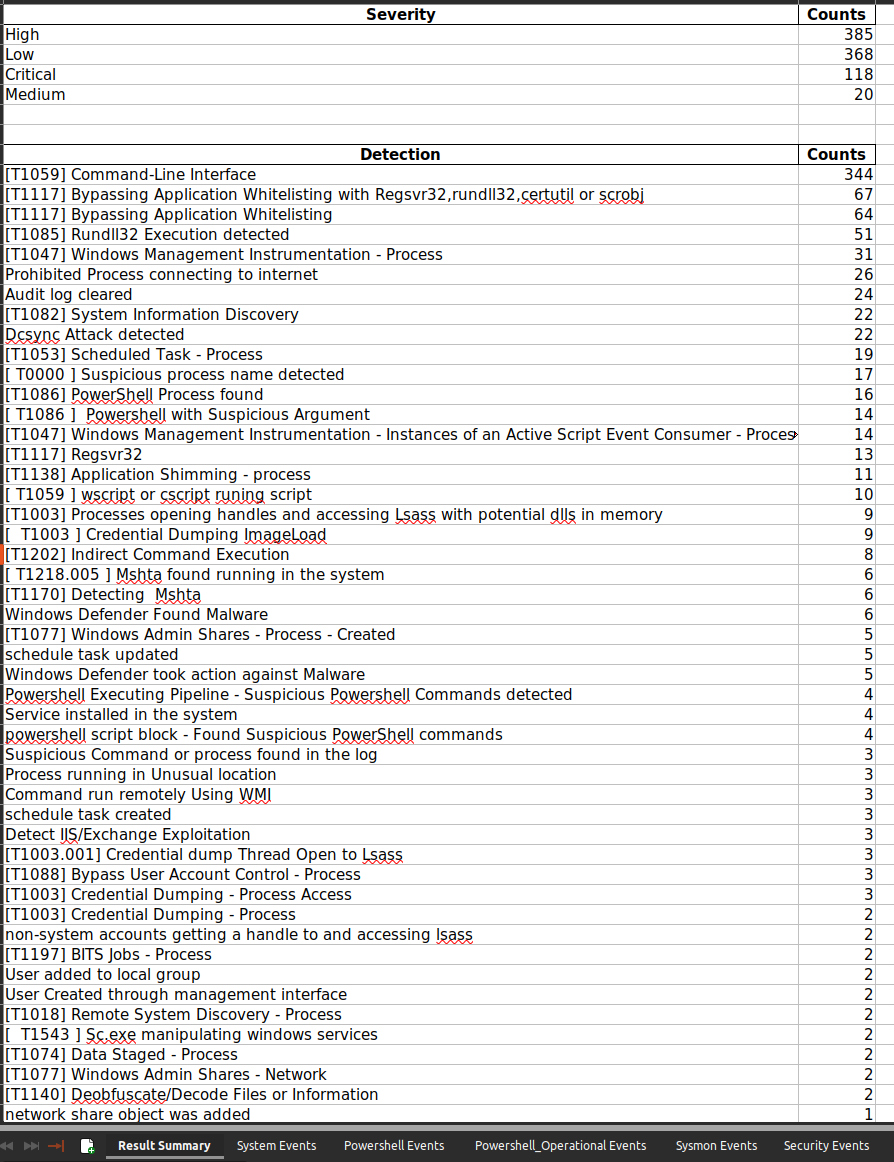
- New Summary of Detection Results.
- New statistics sheet that include the unique powershell commands executed in the systems.
- New Statistics sheet for RDP client events with events SID automatically resolved to users.
- New Statistics sheet for executed powershell commands.
- Now you don’t need to bruteforce EventID 1029 hash to get username .
- WinRM events SID now automatically resolved to user name.
- New collected SID report that will provide you all the discovered SID with their user name.
- New scoring system for powershell detection to let you focus on important events.
- APT-Hunter now can handle any number or size of windows event logs.
- Hunting module now allow you to include specific event ID to search.
- Hunting module now allow you to provide a file with a list of regex
Running APT-Hunter
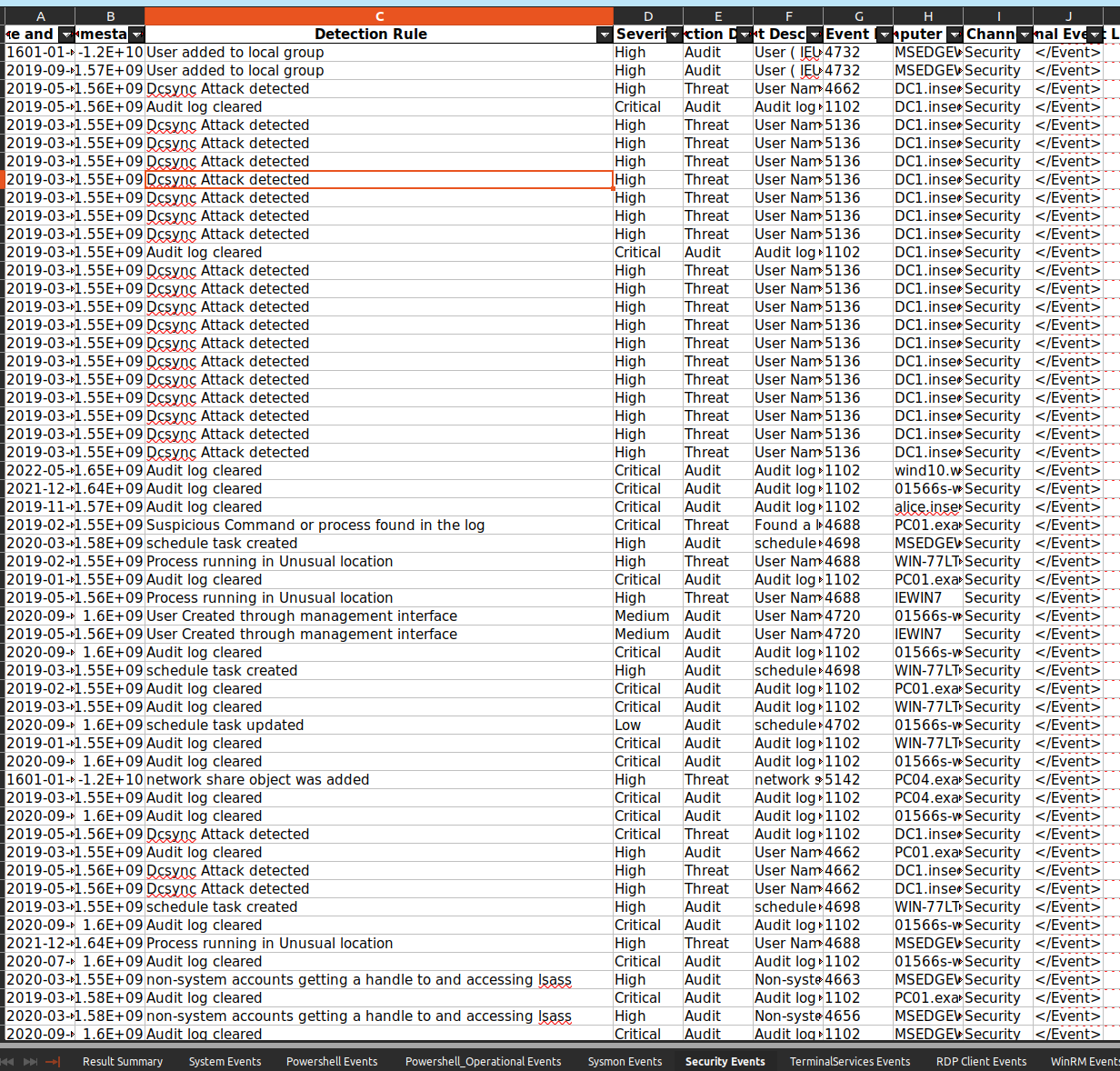
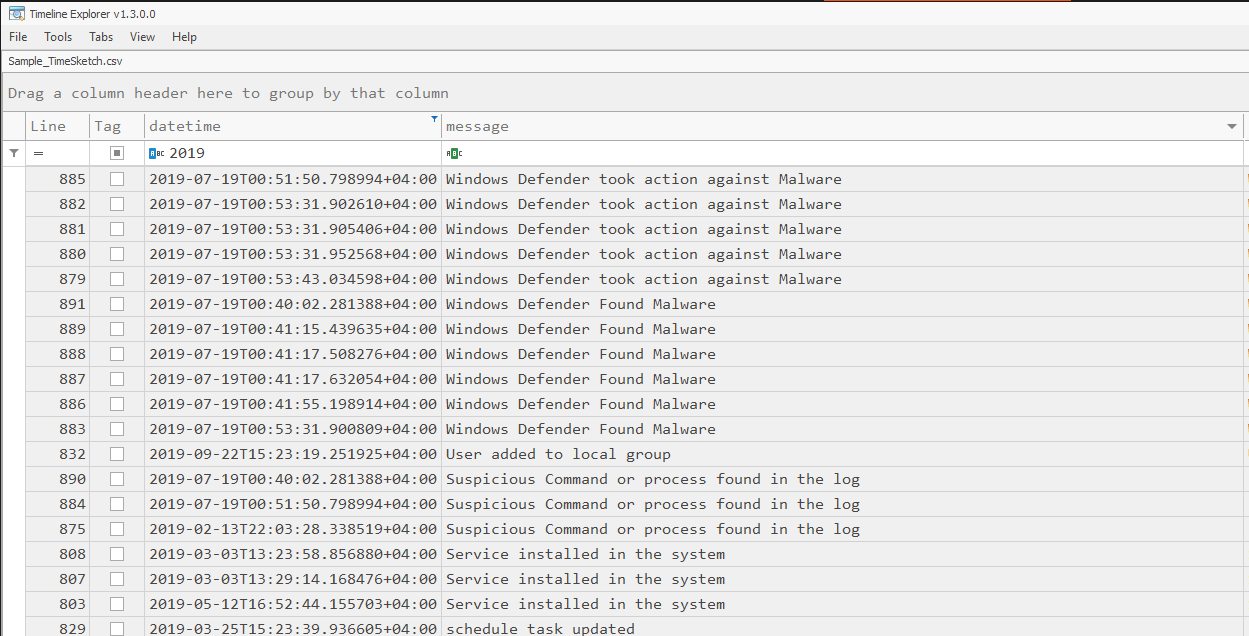
You can check the report samples in from the github repo.