Estimated Reading Time: 9 minutesAMSI, CLM and ETW – defeated* with one Microsoft signed tool Let’s start with AMSI – everyone loves bypassing AMSI! In recent years, many (not all) antivirus products have begun to rely on Antimalware Scan Interface (AMSI) to detect more advanced malicious activity. Today, it captures every PowerShell, Jscript, VBScript, VBA or .NET command or…
Author: Ian
Extracting Plaintext Credentials from Palo Alto Global Protect
Estimated Reading Time: 5 minutesOn a recent Red Team engagement, I was poking around having a look at different files and trying to see if I could extract any information that would allow me to move laterally through the network. I was hopeful, as always, that I would land on domain_admin_passwords_2024.xlsx or something (don’t laugh – we’ve all found…
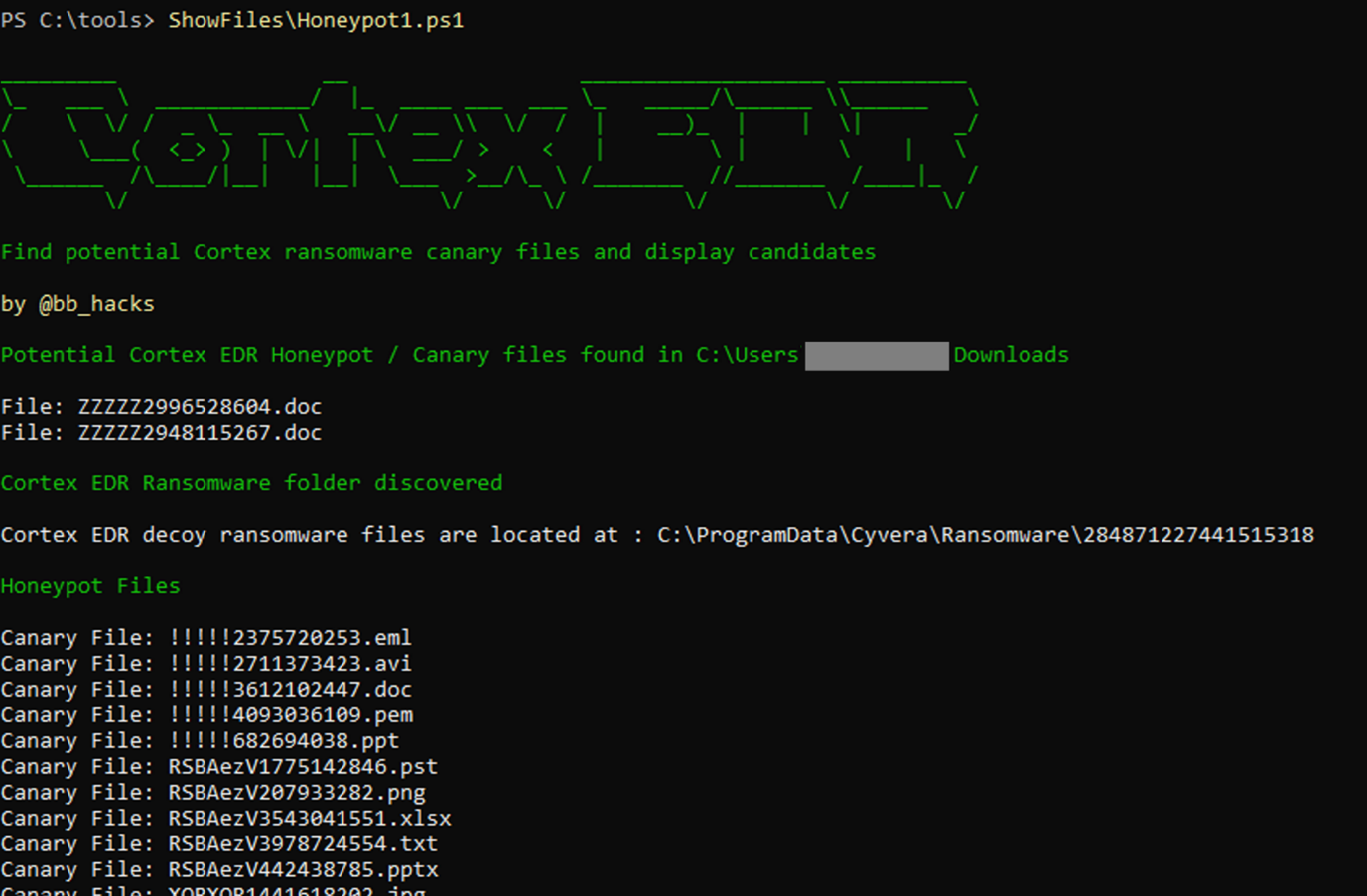
Cortex XDR Ransomware Protection, Chocolate Teapots and Inflatable Dartboards
Estimated Reading Time: 6 minutesA post exploring how to enumerate and avoid Cortex XDR ransomware files/folders and avoid getting caught
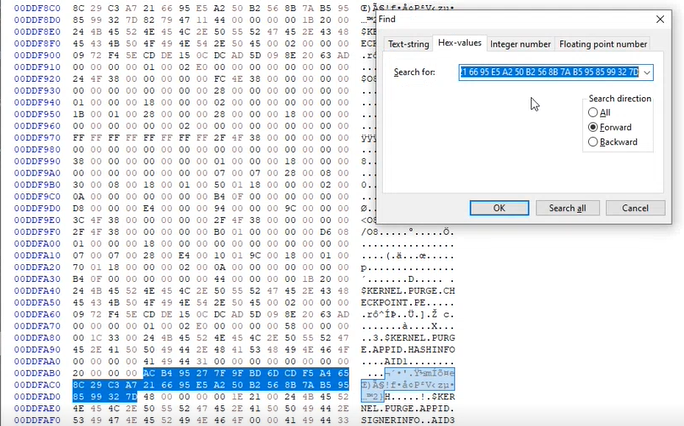
Bypassing AppLocker by abusing HashInfo
Estimated Reading Time: 4 minutesThis article is based mostly on the work of Grzegorz Tworek (@0gtweet) I recently saw this tweet from Grzegorz Tworek (@0gtweet – who if you aren’t following you really should be!) come across my timeline I had seen previous tweets referencing the AppLocker hash/signature cache and having a CPD day I thought I would take…
The Birth of NSGenCS
Estimated Reading Time: 7 minutesOne of the hats I wear at work means that I help our offensive team with strategies and tooling. Since the company I work for is only a few years old, we don’t have the depth and maturity of tooling in some areas and one of my responsibilities is to try and create those resources…
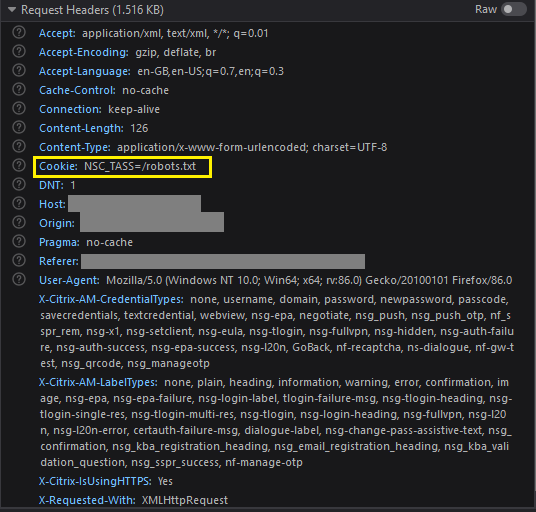
Customising an existing evilginx phishlet to work with modern Citrix
Estimated Reading Time: 6 minutesAs part of a recent Red Team engagement, we had a need to clone the Citrix endpoint of the target company and see if we could grab some credentials. Sounded like a job for evilginx2 (https://github.com/kgretzky/evilginx2) – the amazing framework by the immensely talented @mrgretzky. What is evilginx2? evilginx2 is a man-in-the-middle attack framework used…
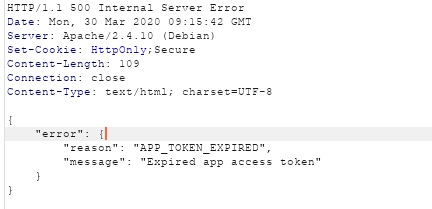
Adventures in Burp Extender Land
Estimated Reading Time: 7 minutesRecently I was testing a mobile application and it’s interaction with an API backend. It was the first time that I had come across an application that used two different JWT tokens in the headers to authorise against the API end point. Burp is great at handling cookies, but is not so great on handling…